Computer networks have become a fundamental part of modern organizations, enabling the seamless transition of business processes from paper-based systems to digital platforms. Since the 1990s, open communication systems have evolved rapidly, making it possible to exchange data across local and global networks. As a result, companies increasingly rely on networking technologies and hire dedicated IT specialists to manage, secure, and maintain their network infrastructure.
One of the key protocols that bridges the link layer and the network layer in modern networking is ARP — the Address Resolution Protocol. ARP plays a critical role in enabling devices to map IP addresses to MAC addresses, facilitating communication across segmented networks. Its development marked a shift from flat link-layer environments to more structured architectures like LANs and WANs. In this article, we’ll explore how the ARP protocol works, its vulnerabilities — including ARP spoofing — and the best practices to secure your network against such attacks.
ARP algorithm
ARP, or Address Resolution Protocol, is a protocol that allows you to match the IP address and MAC address of the requested device. ARP tables, in which this correspondence is prescribed, are maintained only for Layer 3 devices, separately for each of them.
Recall that all devices within the same subnet communicate only through switches, repeaters and other passive and active network devices. Routers are required when we are accessing a subnet that is not in the routing table of our device. This means that communication within our subnet we can call a channel environment. Let's look at an example of the ARP protocol and understand what function it fulfils:
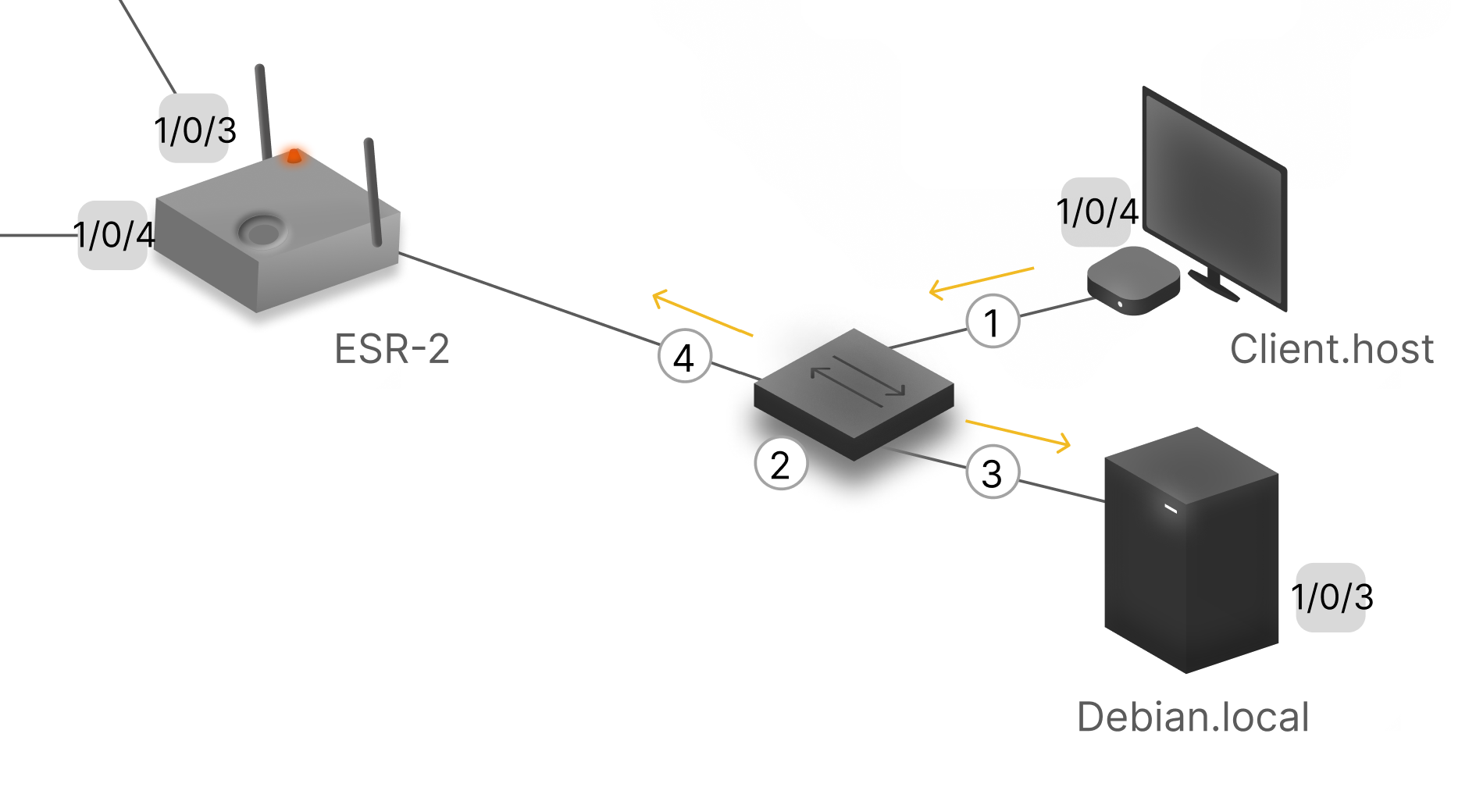
On first connection and empty tables on the devices, there are four main points of communication. Let's imagine that we want to connect to a local server with hostname Debian.local via SSH.
Preliminarily, our device will check the network addresses, if they are the same, then we are in the same subnet and the device will directly address the arp request through the interface gi 1/0/4. But if we do not address the router within the channel environment, how can we find the right device by IP? That's exactly what the ARP protocol is for, our device in the first stage sent a broadcast packet asking: ‘What is the MAC address of such and such device with IP address <any address>’. The request packet reaches the switch and it sends packets to everyone as standard. The packet from the second stage will go to all available ports on the switch's link medium.
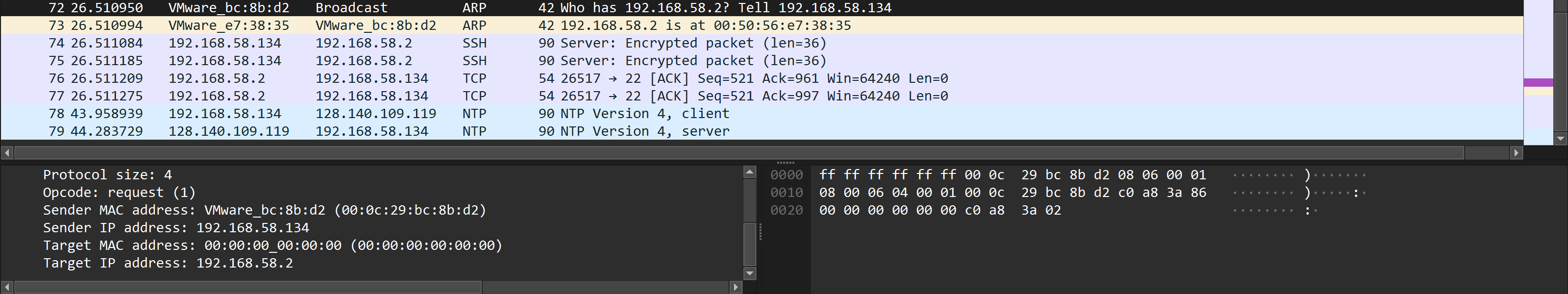
Debian.local will receive this package and see that it consists of IP.src, MAC.src and IP.dst and MAC.dst. So it needs to fill in the field with its MAC address, many people mistakenly call it an ARP address, and send it back to the author of this packet at the source addresses. Debian.local will then write into its ARP table, from the ARP packet, the sender's data and know that 192.168.58.134 corresponds to MAC address 00:0c:29:bc:8b:d2. At this time, the packet has reached back to the client and the client has written the response to its table. The Ethernet link medium packet then needs to be populated so that the switch can send it to the correct destination, the address is now taken by the client from its ARP table.
What if such a packet is answered not by a legitimate device, but by a hacker device? This is called ARP Spoofing or ARP packet spoofing, which is part of an already MitM attack or man in the middle.
ARP Spoofing
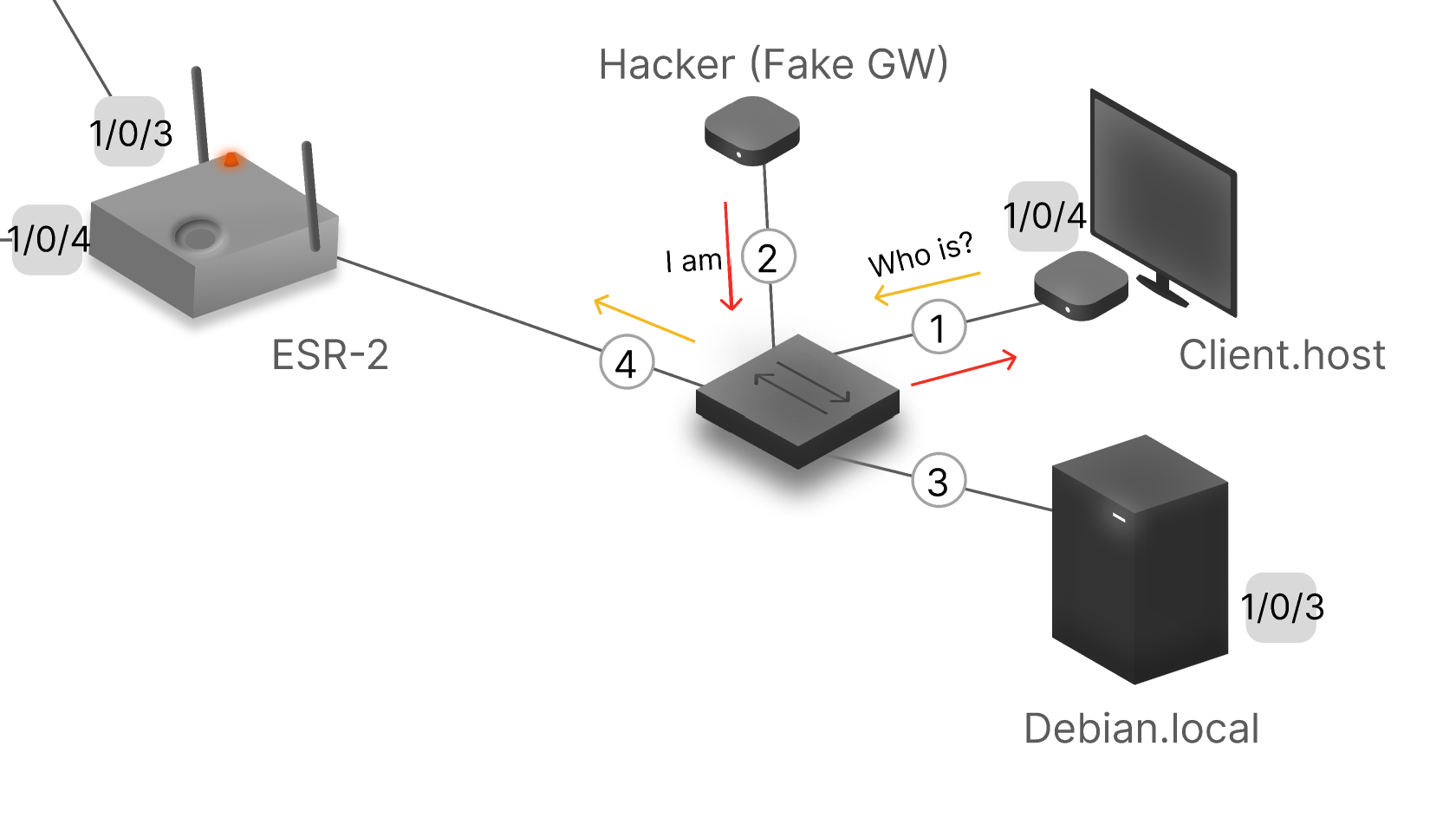
Unfortunately, the ARP protocol does not have authentication features built into it, so it is not possible to verify the legitimacy of the response without additional technologies like DHCP-Snooping or Port Security. A typical attack looks like this:
- Sooner or later, the device wants to update its ARP table data, due to some factors, can use the command arp -d <hostname>;
- The intruder sends ‘infected APR responses’ to the network in advance until the victim catches it;
- The infected entry is now entered into a table where the IP address of, for example, a router is correlated with the MAC address of the intruder's device.
- All traffic is routed to the perpetrator's interface and the perpetrator sniffs or reads it;
- It is then redirected to an endpoint, in this case a spoofed ‘router’.
To protect against this kind of attack, taking into account the peculiarities of the important protocol use differentiation of channel environments with the help of VLANs, assign addresses available for work on Port Security, configure static IP for important nodes, set up technology DHCP Snooping. The essence of the latter consists in assigning trusted ports, on which DHCP stands and records the correspondence of MAC-addresses to those IPs, which are leased to the machines. In conclusion, we can definitely say that it's an important part of a computer network.
If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.




