Regularly checking your devices or corporate infrastructure is an integral part of securing them. This process is called auditing, where it is necessary to assess, using appropriate criteria, whether the security of the device meets the stated requirements.
In order not to manually evaluate each machine, a script was developed that allows you to automate the OS check. In this article we will consider one of such utilities, which will allow you to assess the security of your device and give an estimate in a few minutes.
What is Lynis?
Lynis is an OS audit or security compliance utility that can be thought of as a system scanner. Its task is to identify the front end OS and perform a profile-based scan and then provide an assessment of how secure the device is.
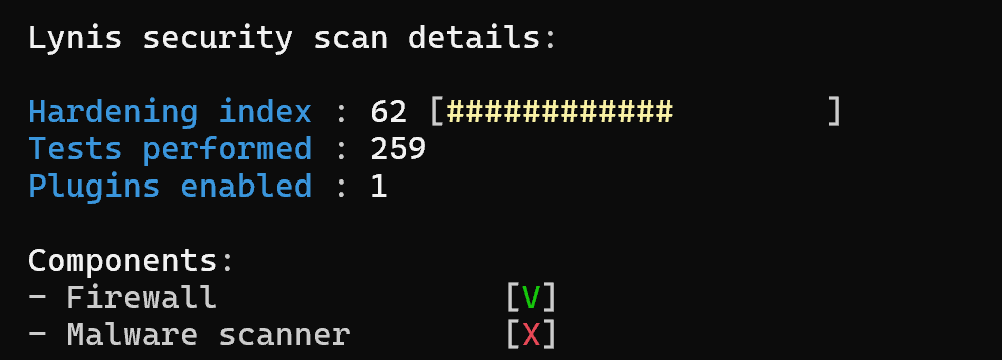
At the moment the utility is an Open-Source solution, there is a similar commercial version with a large pool of features.
This solution can be found in almost all repositories of popular Linux distributions, so downloading it should not cause any problems. For this purpose we will use any package manager:
sudo apt install lynis -y  Screenshot №2 — Installation
Screenshot №2 — Installation
The syntax is quite simple, you need to specify the command to run the lynis utility, additional sub-commands and options to it:
lynis show commands 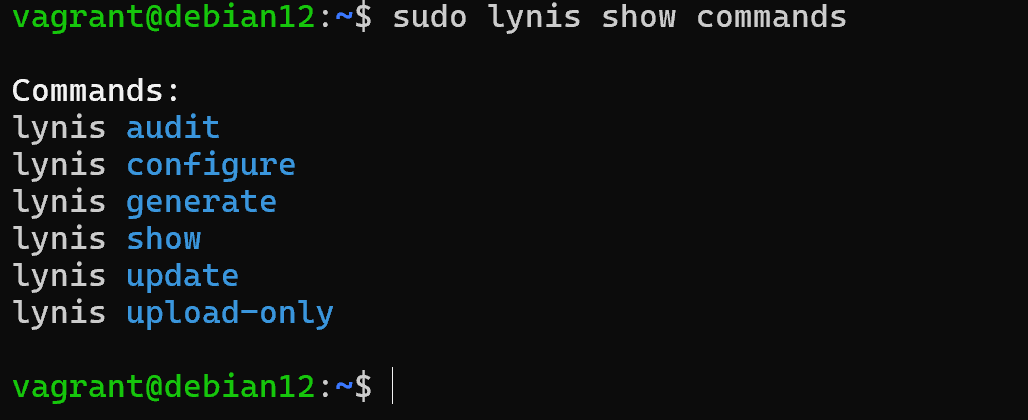
This command allows you to view a list of available sub-commands that can be executed:
- audit is directly a module for scanning the system, as well as virtual environment vorkers, more specifically Dockerfile.
- configuration command allows you to configure the tests and modes to be used when scanning the profile;
- generate allows you to generate the configs for the service to be brought up as a lynis that will periodically test the system;
- show command allows you to view navigation through the utility, as well as brief information about the device;
- update command allows you to check the software for new versions and in case the current one is outdated it will mark it.
The default set of tests and profiles is sufficient for basic scanning. The main difference from typical scanners is that Lynis first determines what software is currently running, on which OS, etc. And only then starts scanning with modules related to the detected software.
Lynis utility audit
To perform a basic check on pre-prepared modules, the command must be written:
sudo lynis audit system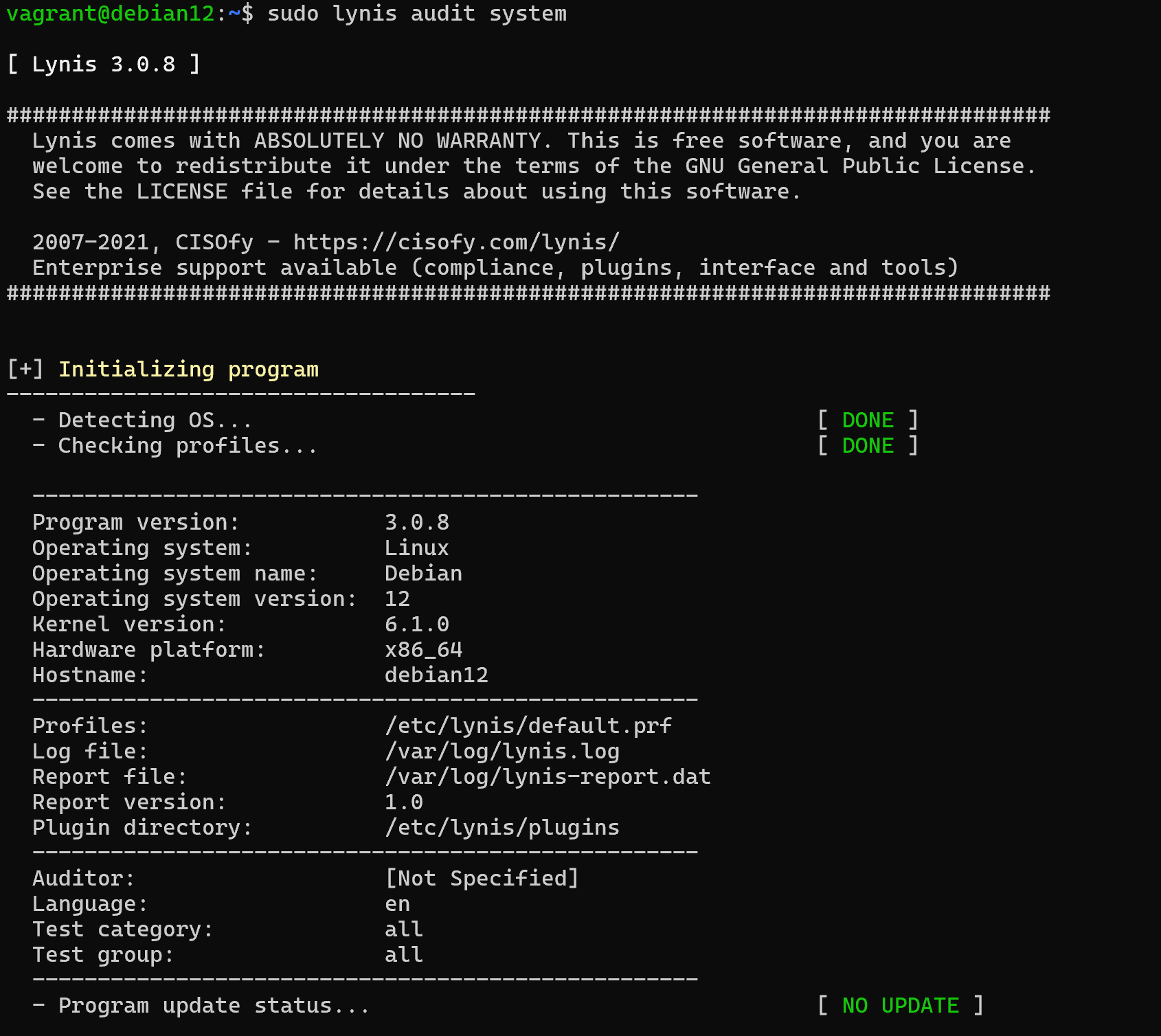
After OS scanning, profiles are initialised and additional information about where to look for scanning results is displayed. And also from which directory plug-ins will be pulled. This is followed by a detailed report, in order to run it in the background you can use the -q option:
sudo lynis audit system -q Or if this report is not enough, a more detailed one can be run with the --verbose option:
sudo lynis audit system --verbose .
The report will show the main categories related to software, file system, shells, etc. For each of them, the survey criteria will be described:
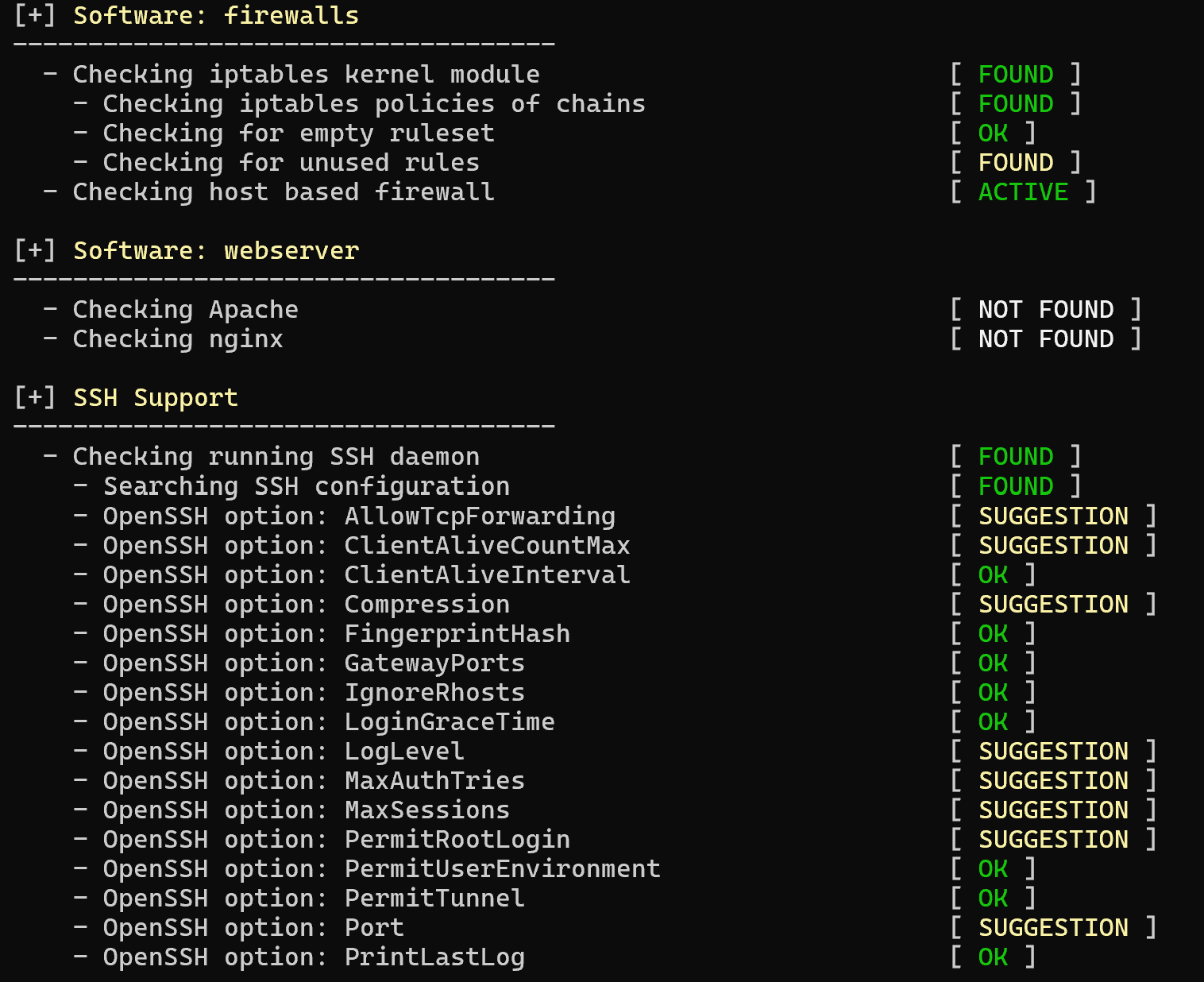
Green indicates requirements that matched the settings on the machine. Yellow indicates changes to improve safety, which will be suggested below. And red indicates a complete mismatch that needs to be corrected. You can also run pentest and forensics scans with the appropriate options:
sudo lynis audit system --pentest In the results, we will see an assessment of the security of our device in relation to best practices, which will allow us to understand what measures we need to take to protect ourselves.
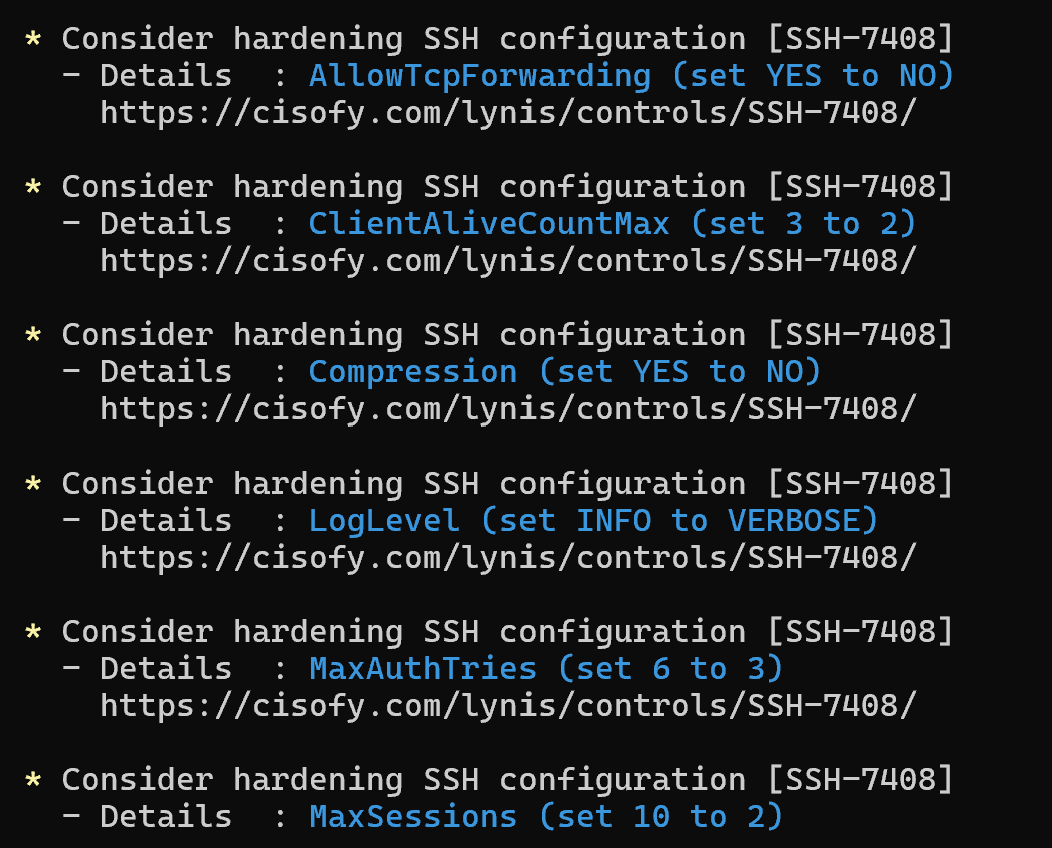
Each of them will either directly, or with a reference to help, describe how the device should be hardened. But not all settings may fit your tech processes, for example, the maximum number of login attempts is mentioned from 3 to 6. But usually the acceptable value can be 10 quite, so rely on these recommendations more as a hint. Critical issues will be highlighted separately:
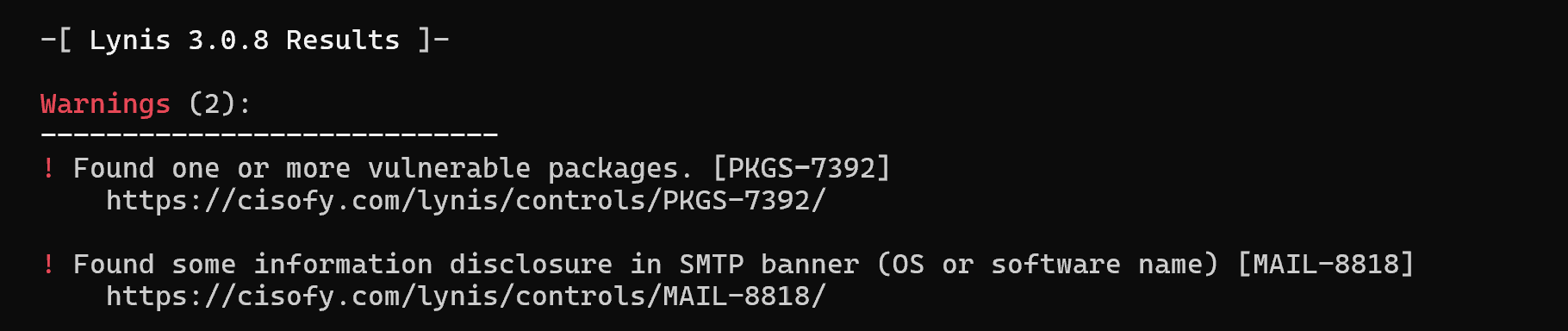
In this context, there is a mailer banner sticking out, which gives the version of either the OS or the software itself and allows the attacker to try to find an exploit for it. It also presents a couple of vulnerable packages that can be found from the report and patched.
If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

Then you can connect to the server via remote control protocols such as SSH and work with the machine!
Conclusion
Regular security audits are essential for maintaining a robust Linux environment. Using tools like Lynis, administrators can quickly assess system configurations, identify vulnerabilities, and receive actionable recommendations for hardening the OS. Whether for personal devices or corporate infrastructure, automated audits help ensure compliance with best practices, reduce attack surfaces, and maintain overall system integrity. Performing these checks regularly allows you to stay ahead of potential threats and maintain a secure computing environment.
FAQ
- Q1: What is Lynis and why should I use it?
A: Lynis is an open-source security auditing tool for Linux systems. It helps assess the security posture of your system, identify vulnerabilities, and provide recommendations for improvement. - Q2: How do I install Lynis on my Linux system?
A: Lynis is available in most Linux repositories. For example, on Ubuntu, you can install it with:
sudo apt install lynis -y - Q3: How do I perform a basic system audit using Lynis?
A: Run the following command to start a basic audit:
sudo lynis audit system - Q4: Can I get a more detailed audit report?
A: Yes, use the --verbose option for a detailed report:
sudo lynis audit system --verbose - Q5: What do the color codes in Lynis reports mean?
A: Green indicates compliance with best practices, yellow suggests improvements, and red highlights critical issues that require attention. - Q6: Can Lynis be used for advanced security testing?
A: Yes, Lynis includes options for pentesting and forensic scans using the --pentest option. - Q7: Are Lynis recommendations mandatory?
A: Not always. Recommendations serve as guidance. Some parameters may need adjustment based on your environment and technical requirements. - Q8: Can Lynis help with ongoing monitoring?
A: Yes, you can configure Lynis to run periodically and generate reports to continuously assess your system’s security.



