Introduction.
Automatic assembly of projects after updating the code is actually a standard procedure allows you to view & test the product developed on the go, immediately look through errors and, as a result, quickly find and fix the problem. With the advent of Docker, they have become no less relevant and in demand. There are dozens of CI systems themselves today: Jenkins, Atlassian Bamboo, Bitbucket Pipelines and so on. The problem is that they are quite complex, most of them are commercial and cost a certain amount and, most importantly, require a specialist and time to configure and constantly adjust, which they usually cannot afford in small projects and even more so in individual development.
Concourse CI is a continuous integration system required for automating testing pipelines using unified declarative syntax. Concourse CI makes the process of the implementation of continuous integration simpler, while it requires almost no time to deploy and study.
In our previous guide we looked at Concourse CI installation and configuration on a Debian 10 server. We figured out how to run it from the CLI and use the web interface.
In this instruction, we are going to look at protecting the gui by setting up the reverse proxy server via Nginx.
Reverse proxy usage has some advantages like: restricting access to certain content, allows staying anonymous, allows you to avoid restrictions on viewing content, reduces the load on the main servers due to caching of static and dynamic content, compresses content to reduce download time, and it uses a software firewall, which can protect against the most common web attacks.
Before we get started
Firstly we should deploy a virtual server with OS Debian 10. There should be at least 1 GB of RAM. Follow the tutorials according to the instructions to configure a simple account without superuser rights.
Install and set up Concourse CI using the official website or GitHub.
Installing Nginx and setting up an encrypted connection.
You should get a domain name to access by domain, not by IP address.
Reverse proxy specification
Let's begin with editing the server block file to configure SSL and redirect traffic to the Concourse CI server.
The /etc/nginx/sites-enabled directory contains the file, which is the default file after nginx is installed.
Let's make edits to the file to set up a proxy server. It will route traffic to the site by domain name.
Let's start. Add lines at the top of the default file from the /etc/nginx/sites-enabled directory before the main part of the server block. Specify the local server IP address and port that our Concourse server is listening on:
upstream concourse {
server 127.0.0.1:8080;
}You need to find the block responsible for servicing SSL. By default the line with listen 443 is used. Make sure that after server_name there is your domain name.
Set up the "location /" block in this block. It sends requests to the Concourse server:
location / {
include proxy_params;
proxy_http_version 1.1;
proxy_read_timeout 90;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_pass http://concourse;
}After making edits, don't forget to save the file and exit it.
Using the command let's check the correctness of the file:
nginx -tAs a result, we get syntax ok. Test is successful.
You need to reboot nginx to apply the changes
service nginx restartYou configured Concourse server for the domain.
Binding a domain to a network interface
After all the configuration settings, we need to bind our local address to our domain. Open the web-environment file from the /etc/concourse directory and convert the string CONCOURSE_EXTERNAL_URL to the following and add the local IP address:
CONCOURSE_EXTERNAL_URL=https://serverspace.tm
CONCOURSE_BIND_IP=127.0.0.1Let's exit and save the changes.
We must relaunch the concourse-web service to apply the edits.
service concourse-web restartLet's check which address works with port 8080 using the command:
netstat -tlnup | grep :8080As an output, we get the following line
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN 1781/concourseThe interface only listens on the local IP address.
Now we will make edits to the firewall deleting the rule for port 8080:
ufw delete allow 8080All requests will be processed by Nginx which runs on port 80.
Iterface verification
Interface provide the ability to browse all pipelines and tasks, monitor the results.
Let's open a browser and enter our domain name. We will get to the Concourse welcome page:
Then enter the login and password you specified during configuring Concourse:
After successful authorization, we can open the interface:
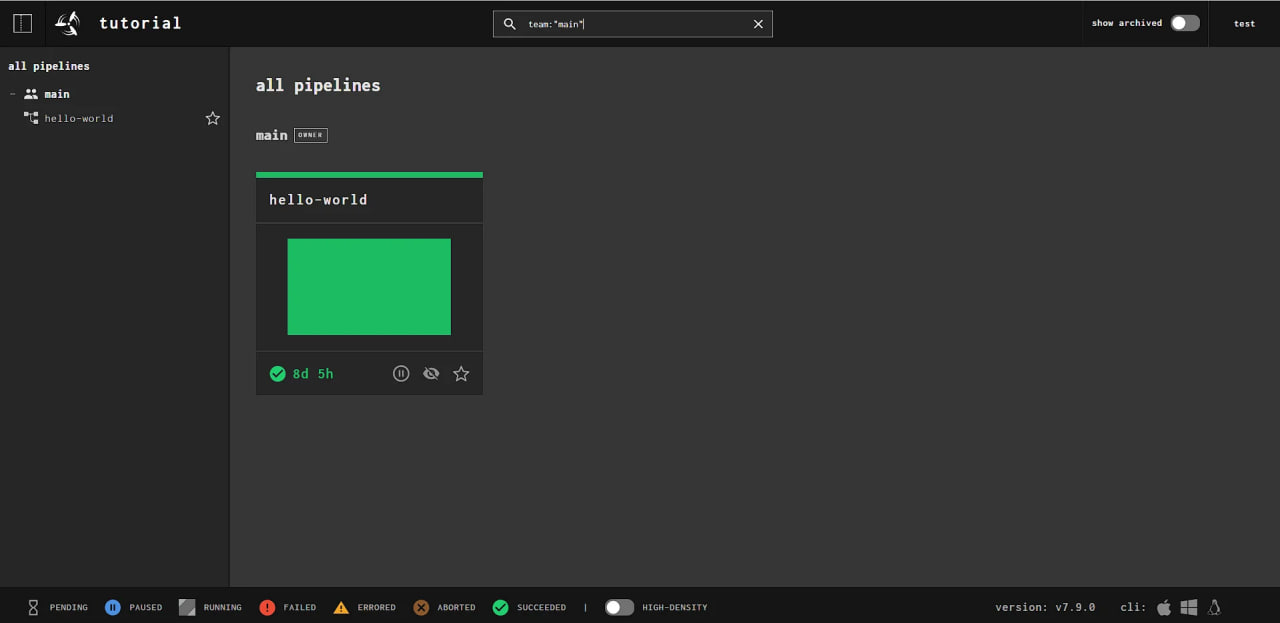
Now you have the access to Concourse gui via the domain.
Conclusions
We looked through:
- Changing Nginx file to route traffic by default;
- Binding a local IP address to a domain;
- Gui testing via a domain.



