Why is apt-key deprecated?
The secure installation process contains many pitfalls, one of which is downloading files and resources with privacy and authentication. Linux distributions have implemented the apt-key and add-apt-repository utilities, which automate the process of checking repository packages against added keys. However, a significant security issue has emerged: there is no mechanism for assigning a specific key to a repository. This means that if a company key is compromised or employees abuse their authority, a malicious file could be signed. Newer versions of the distributions have already integrated a more secure solution using GPG directly, which we will discuss below.
Which command has replaced apt-key?
Instead of the obsolete apt-key and apt-add-repository, which mediated the verification mechanism, only the GPG utility will operate. It was present in the identification and integrity and authentication mechanism before. However, the update will allow you to get rid of the intermediary utilities that posed a number of threats.

GPG or GNU Privacy Guard is a crypto package that allows you to encrypt, decrypt, sign documents and messages with EDS, store keys with identifiers in a database, and perform many cryptosystem functions. Just one of these is signature verification on apt packages. For more clear demonstration all steps in the tutorial can be performed on powerful cloud servers.
It will take some time to deploy server capacity. After that you can connect in any of the convenient ways. And let's move to the terminal with our OS!
How to add keys and repository in terminal?
First, we need to get the public keys and a link to the repository where the packages will be downloaded from. For example, let's look at the MongoDB database. Go to the official site to find a repository for the Debian distribution and fix the main components:
- Public key: www.mongodb.org/static/pgp/server-7.0.asc
- Link to repository: repo.mongodb.org/apt/debian
The curl and gpg utilities are required to work with the components, if they are not available, install them via the command below:
apt install curl gnupg -y When downloading data from the repository before installation, Linux accesses the list of trusted keys and checks the signatures, if they match, then proceed to the installation process. Otherwise, the utility displays the signatures do not match and the package is considered potentially untrustworthy. In order for the files to be verified, it is necessary to download the public key and add it to the list of trusted keys.
curl -fsSL https://www.mongodb.org/static/pgp/server-7.0.asc | sudo\
gpg --dearmor -o /usr/share/keyrings/mongokey.gpg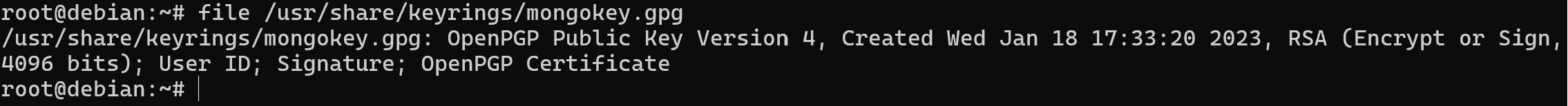
Having verified that the file is indeed a public signature, we now need to add a repository and associate it with the key. To do this, let's write a command that will allow us to make changes to the repositories file:
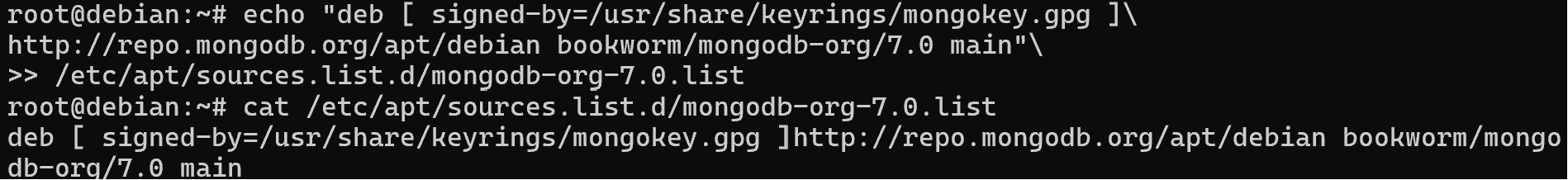
echo "deb [ signed-by=/usr/share/keyrings/mongokey.gpg ]\
http://repo.mongodb.org/apt/debian bookworm/mongodb-org/7.0 main"\
>> /etc/apt/sources.list.d/mongodb-org-7.0.listLet's take a closer look at each element of the command:
- the echo utility allows you to display values in quotes;
- the string [ signed-by=/usr/share/keyrings/mongokey.gpg ] is the path for the key checking mechanism;
- link to repository http://repo.mongodb.org/apt/debian bookworm/mongodb-org/7.0 main;
- redirects content from the screen, after the echo utility to the /etc/apt/sources.list.d/mongodb-org-7.0.list file.
Once we have checked with the cat utility to see if there is a record, we can update the distribution and try to download the software:
apt update && apt upgrade && apt install\
mongodb-org -y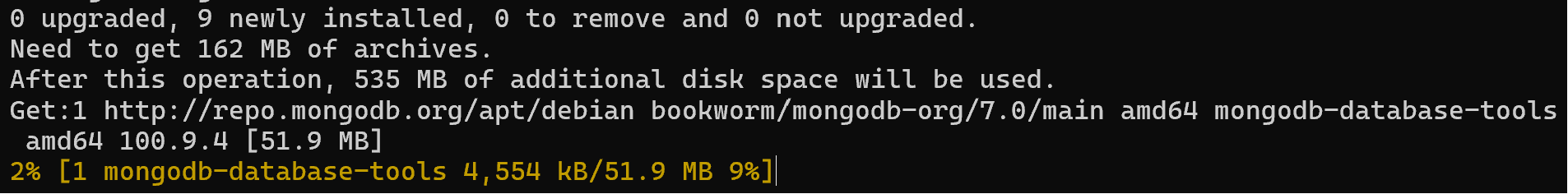
The packages were successfully downloaded and installed on the system! In this case, we have safely installed the keys, as we had previously connected via HTTPS to a site that had a valid certificate. This indicates the authenticity of the stored data and also the hash sum attached to the key certifies its integrity. Therefore, the transmitted packets are authentic and have not been modified!



