When trying to connect to a Docker repository, many users may have encountered the error ‘denied: 403 Forbidden. ‘Error response from daemon: error parsing HTTP 403 response body: invalid character “<” looking for beginning of value:’
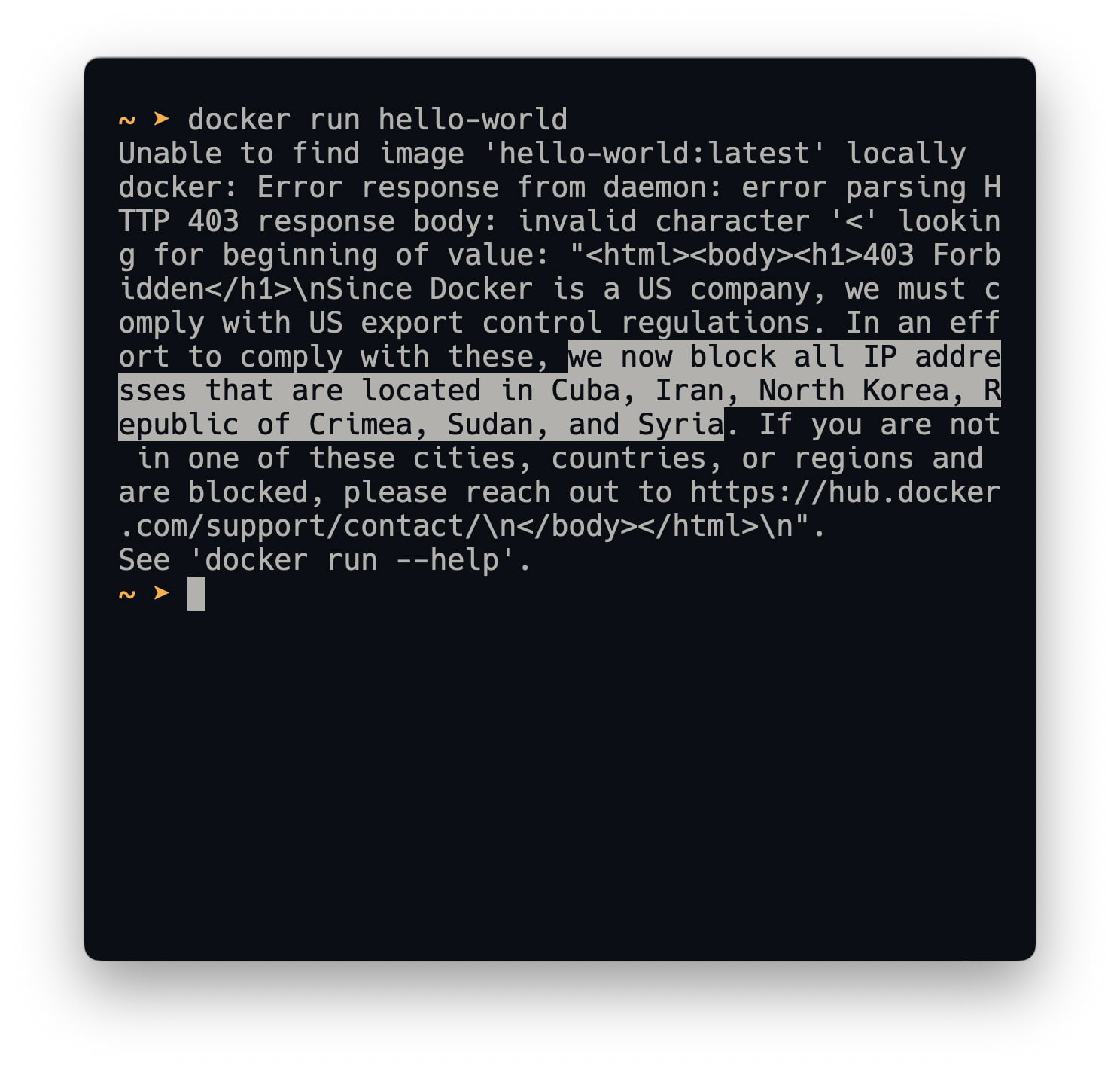
At the moment it is not illegal to use the containerisation platform, however, downloading images from repositories has been stopped for some countries! What to do if you accidentally get blocked? There are many options to solve the problem: raising a mirror of the site, a VPN server or a proxy tunnel. In this tutorial we will look at the simplest option to connect to Docker Hub. We will use ShadowSocks!
What is ShadowSocks and how do I configure it?
ShadowSocks is a proxy server with the ability to encrypt tunnelled traffic passing through it for secure transmission, through untrusted parts of the network, as well as addressing through devices with a different IP address.
The principle of operation is as follows:
client <---> ss-local<--[encrypted traffic]--> ss-remote <---> target server
The client raises a proxy server on its side, which can be reached by internal address. All traffic coming to it is encrypted and sent to the ss-remote or endpoint, where it is received and decrypted. After that, it is addressed by the machine where the packets came from, and then the reverse process of transmission to the client takes place.
Configuring the ShadowSocks server
All steps in the tutorial can be performed on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

It will take some time to deploy server capacity. After that you can connect in any of the convenient ways!
Before installing and configuring the server, you need to update the repositories and download the required packages. If you are using apt-manager, the command will look as follows:
apt update && apt install curl snapd -y 
Before installing and configuring the server, you need to update the repositories and download the required packages. If you are using apt-manager, the command will look as follows:
snap install core After that, let's install the ShadowSocks package itself:
snap install shadowsocks-rustLet's check its components and permissions to work with the rest of the OS via commands:
snap services shadowsocks-rust snap connections shadowsocks-rust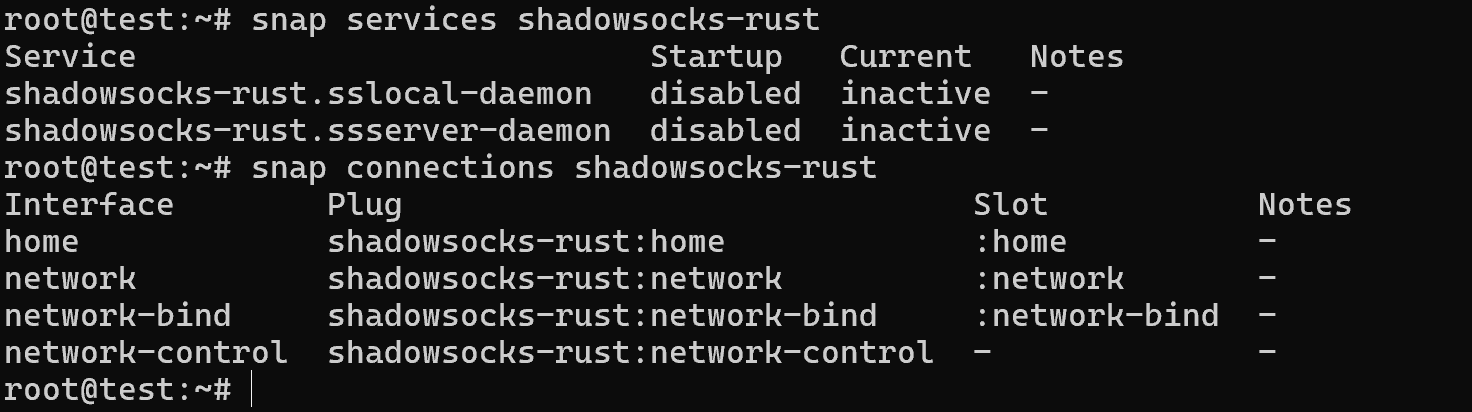
As you can see the package consists of two services local and server, where one is a client for connection and the other is a server. This image has rights to work with the network and the ability to make changes to the network stack.
Let's create a configuration file for our server, in json format:
nano /root/shadowsocks.jsonAnd write the configuration to connect to the server:
{
"server": "0.0.0.0",
"mode":"tcp_and_udp",
"server_port":1224,
"password":"ZmVlNmlldDVhZW5naWU2ZWlUb29nOGFobjNvaFlpZQo=",
"timeout":300,
"method":"2022-blake3-aes-256-gcm"
}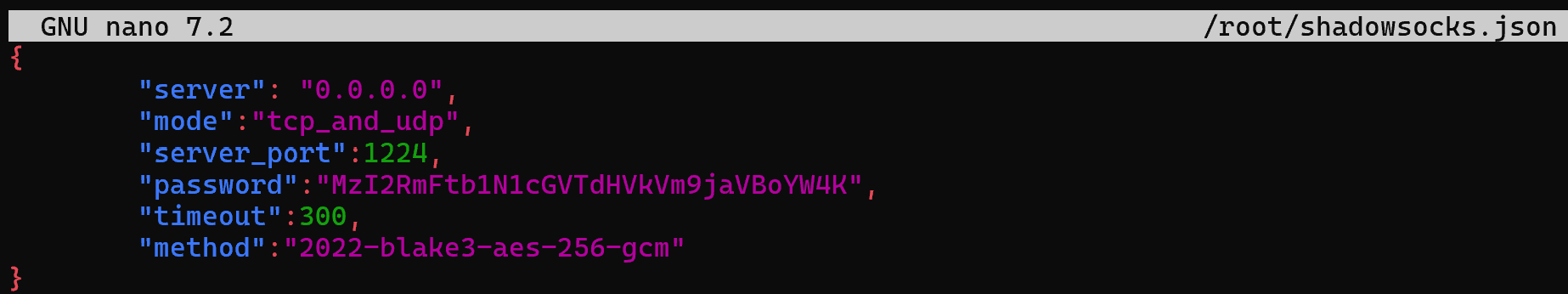
In the server field specify a specific external IP address or leave the default reception from all interfaces as 0.0.0.0.0. In the mode field specify the protocol for transporting your traffic, then specify the port to connect to the server. Password of 31 single characters in base64 form, for this purpose write the following command and enter the result in the password field:
echo “YOUR_PASSWORD” | base64 If you wish and your requirements, you can change the method of traffic encryption! Let's save the configuration file with the combination Ctrl + O. After that, let's test the server operability with the command, where we call the daemon and specify the config for its operation:
snap run shadowsocks-rust.ssserver-daemon -c /root/shadowsocks.json 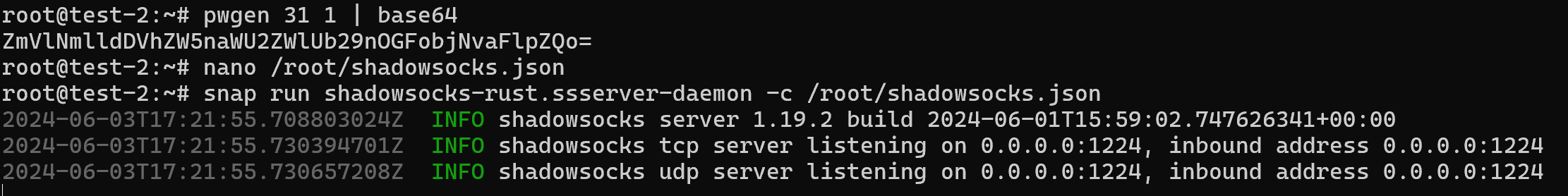
Great traffic is proxied, so we can add the server to autoload:
snap start --enable shadowsocks-rust.ssserver-daemon -c /root/shadowsocks.json This will create a unit in the initialisation system, which we need to edit and add our new configuration file:
nano /etc/systemd/system/snap.shadowsocks-rust.ssserver-daemon.serviceAdd a string to the ExecStart field and start reading configurations:
ExecStart=/usr/bin/snap run shadowsocks-rust.ssserver-daemon -c /root/shadowsocks.json 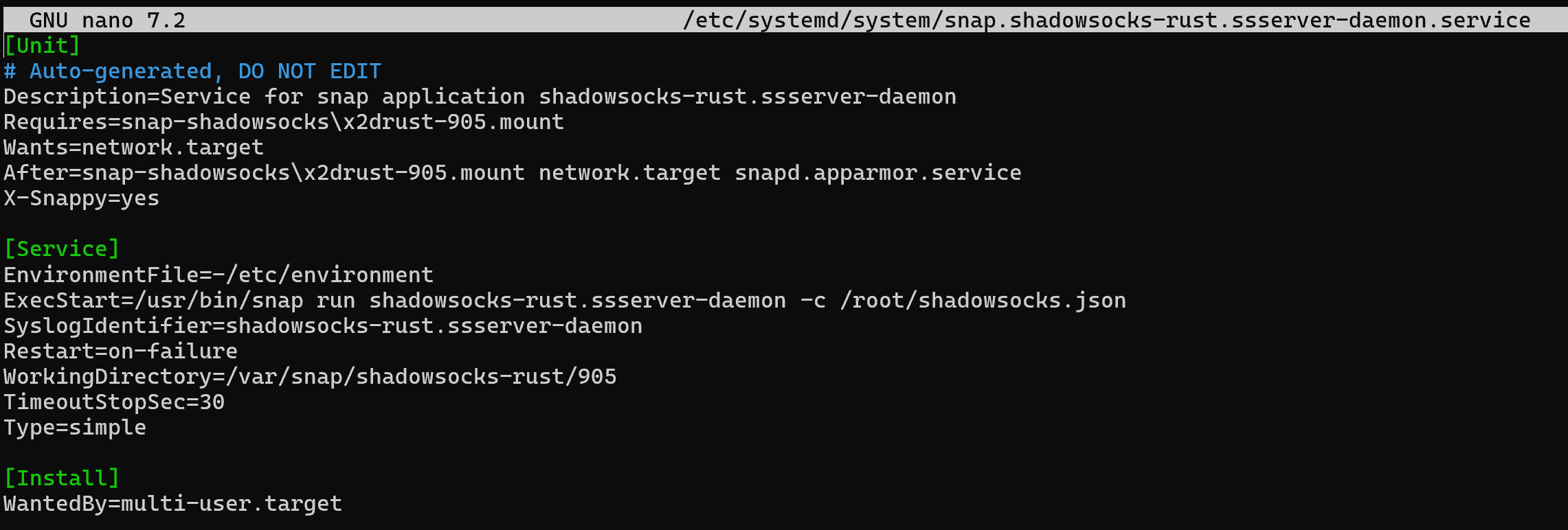
Let's save the file and reread the new configuration, then start the service:
systemctl daemon-reload && systemctl restart snap.shadowsocks-rust.ssserver-daemonAfter that we fix the result and check the ports:
systemctl status snap.shadowsocks-rust.ssserver-daemon netstat -tulnp 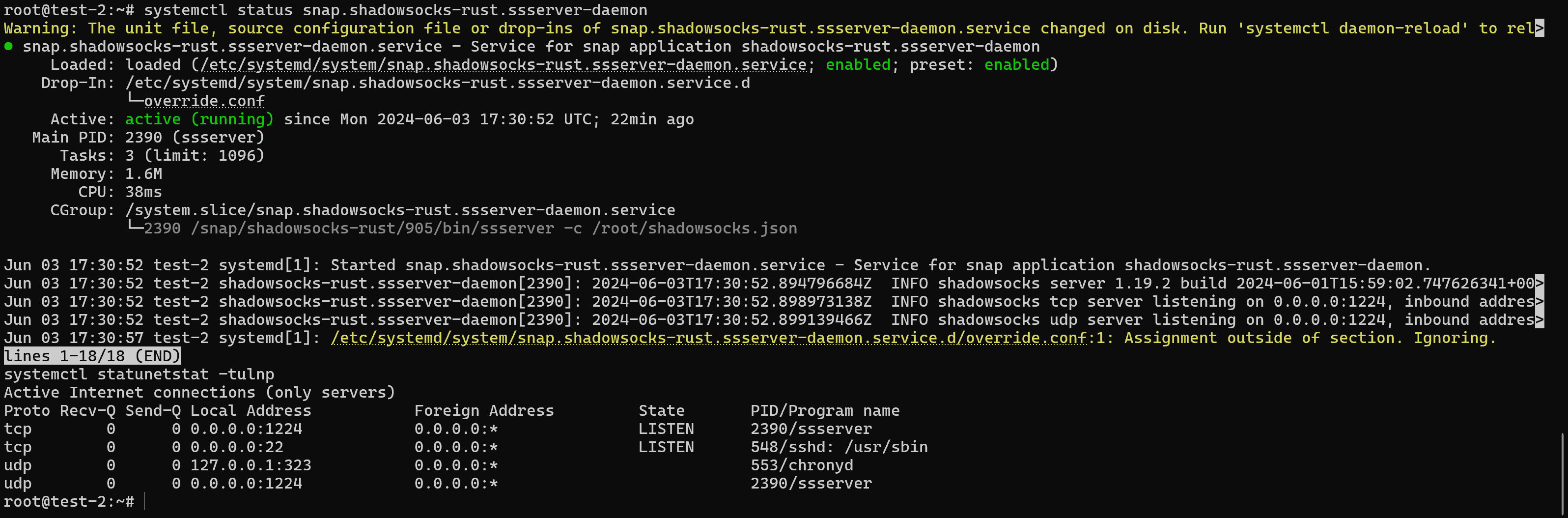
The ports are listening and the service is working properly, now you need to perform the same steps but for the client.
Configuring the ShadowSocks client
Also install the snapd and curl packages and follow the same steps as for the server.
apt install snapd curl -yLet's install the client and write a new configuration file for it:
snap install shadowsocks-rustnano /root/client.jsonIn the file itself, insert the following JSON fields:
{
"server": "IP_Server",
"mode":"tcp_and_udp",
"server_port":Remote_port,
"local_address":"127.0.0.1",
"local_port":Local_port,
"password":"Pass in Base64 from server",
"timeout":300,
"method":"Method of encrypt"
}Let's connect the autoloader for the user's client and configure the file:
snap start --enable shadowsocks-rust.sslocal-daemonnano /etc/systemd/system/snap.shadowsocks-rust.sslocal-daemon.serviceLet's write in the ExecStart field the necessary config for loading and operation:
ExecStart=/usr/bin/snap run shadowsocks-rust.sslocal-daemon -c /root/client.json After that we start reading the new configuration files
systemctl daemon-reloadLet's restart the service and check our settings via curl:
systemctl restart snap.shadowsocks-rust.sslocal-daemon.servicenetstat -tulnp && curl -- proxy socks5://127.0.0.1:1224 https://ifconfig.me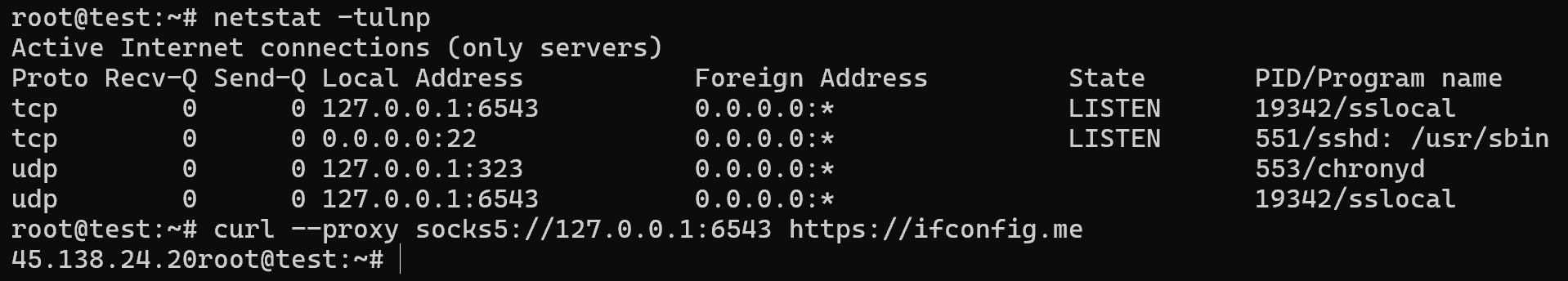
In order for only Docker traffic to go through the proxy it is necessary to complete the initialisation system unit. Let's create a folder and enter the config file:
mkdir /etc/systemd/system/docker.service.dnano /etc/systemd/system/docker.service.d/http-proxy.conf
Let's write the necessary variables for dockerd to work and save via Ctrl + O:
Environment="HTTP_PROXY=127.0.0.1:1224"
Environment="HTTPS_PROXY=127.0.0.1:1224"Re-read the new configuration files and restart Docker:
sudo systemctl daemon-reload
sudo systemctl restart dockerShadowSocks, thanks to its ability to encrypt traffic, provides a secure connection to the resources you need by bypassing restrictions and providing access to Docker Hub. By configuring the ShadowSocks server and client, and integrating it with the Docker client and daemon, you can create a stable and reliable connection. By following the step-by-step installation and configuration instructions, you will be able to configure the system so that all Docker traffic goes through the proxy, providing access to the required images and repositories.
This way, even in a lockdown environment, you can continue to leverage Docker's containerisation capabilities using modern and reliable traffic proxying solutions.



