One possible vector of attack on infrastructure is network devices, especially edge devices. If an attacker gains access to the device's shell and executes an attack, it could result in prolonged downtime of services, or even the entire infrastructure. So it's important to know what actions you can take to protect your device!
In this article, let's cover the basics and background on user management in a router!
User customisation
If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

Classically any configuration starts in the CLI starts with a view of current users and capabilities. The command will show the list of currently authenticated users:
show user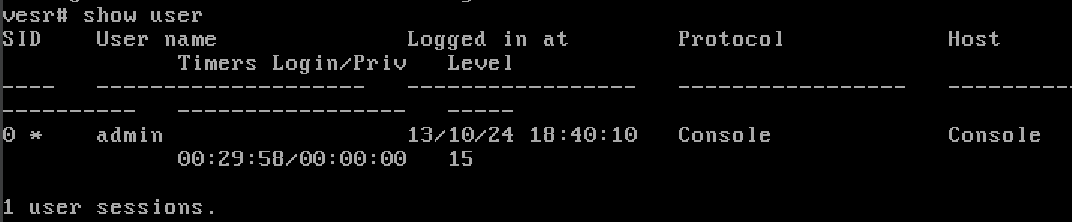
You can also view a list of ever created:
show running-config | include username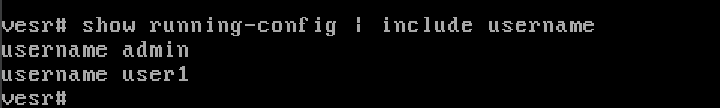
Suppose we need to create a new account for a network engineer, for this we will switch to privilege mode:
enableAfter that we will write the command to activate the configuration mode and create a user with the parameters:
config
user user1
password <value>
privilege 15
exit
exit
commit
confirm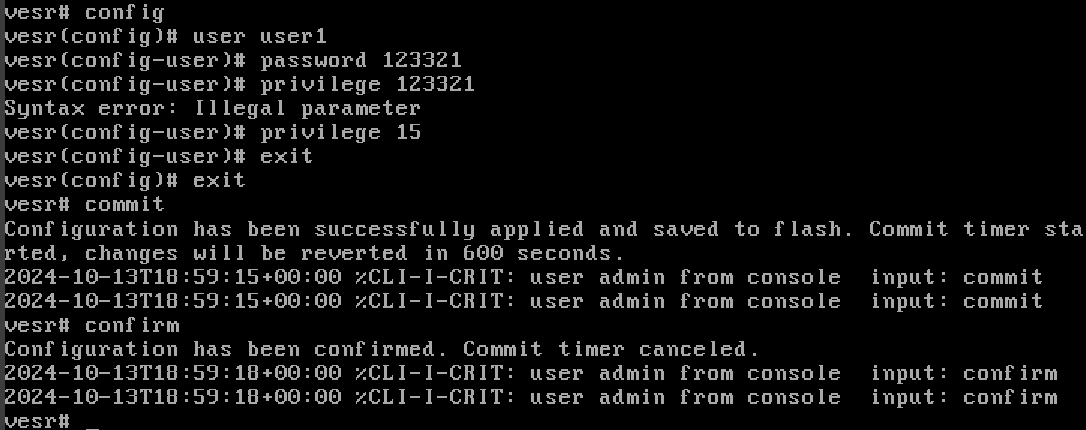
By writing the command, user user1, we created a new user, who then has a password. Then privilege level 15, which indicates that he has maximum privileges, as we needed an administrator. But if you need to create a user with lower privileges, you can specify a lower level. After that we exit the configuration and confirm the changes with the commands commit and confirm.
Pay attention to the line with privileges or privilege, which indicates that certain rights are allocated to the user at level 15. To understand what rights should be granted to a user and at what level, you can use the official documentation, which describes each of them.

It seems that the password in the previous task is too easy to bruteforce, let's change it to a more complex one:
user user1
password NEW-strong-P@sSIn the example only a template is given, so it is desirable to create a more complex sequence of 18 characters or more of different characters of different characters and case.
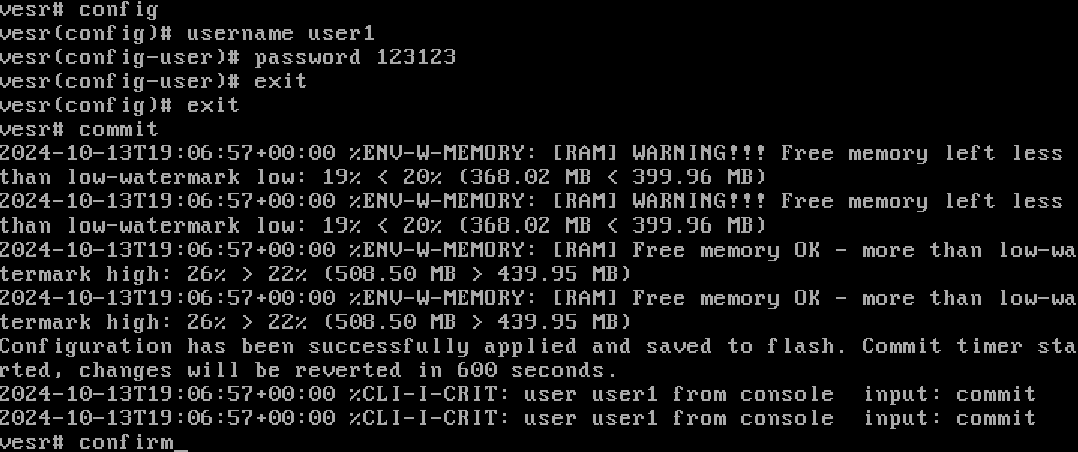
Let's try authenticating through a new user using the console, log out of the current session and log in with new creds. And also make sure that the users are authenticated:
show user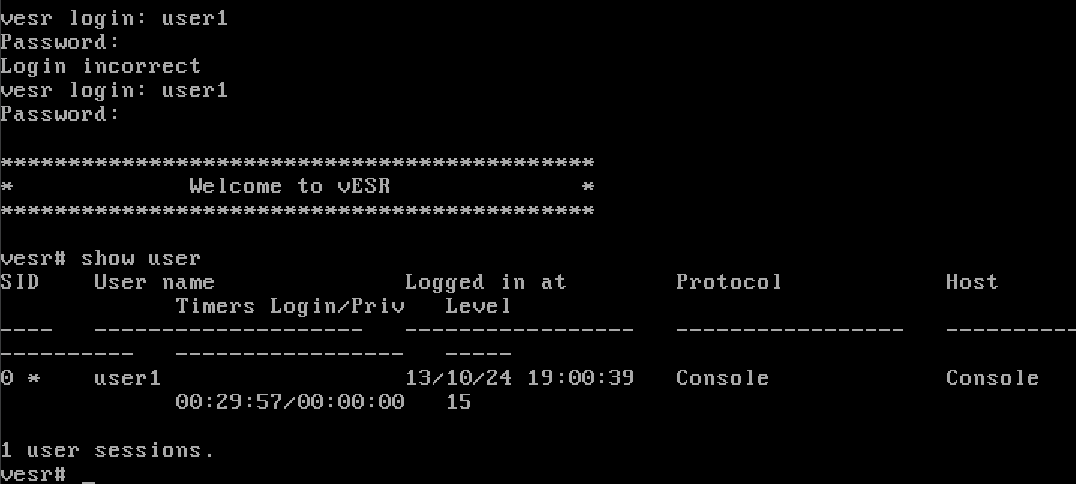
Let's remove an old one that is not needed, which might have been lodged in our router OS after one of the engineers was fired. After all, this is also an attack vector:
config
no user user1Enough, a short command allows you to remove the user, after which don't forget to apply the settings! Remember that you can only perform this action with a certain privilege level. Keep your account data in a safe place!
Conclusion
Managing users on Eltex routers is a critical step in securing your network infrastructure. By creating accounts with the correct privilege levels, setting strong passwords, and removing unnecessary users, you reduce the risk of unauthorized access and potential downtime. Always follow best practices, rely on official documentation for privilege levels, and review user accounts regularly to maintain a secure and stable environment.
FAQ
- Q1: Why is user management important on Eltex routers?
User management helps control access, prevents unauthorized logins, and reduces the risk of attacks on network infrastructure. - Q2: What privilege level should an administrator have?
Typically, administrators are assigned privilege level 15, which grants full access to all configuration commands. - Q3: How strong should router passwords be?
Passwords should be at least 18 characters long, include uppercase and lowercase letters, numbers, and special symbols for maximum security. - Q4: Can I manage users only via CLI?
No, Eltex routers also allow user management via the web interface, but CLI provides more granular control and flexibility. - Q5: What should I do with old or unused accounts?
It’s recommended to promptly delete any inactive or unnecessary accounts, as they pose a potential attack vector.



