Hashcat is a powerful tool for recovering passwords from hashes. It supports a wide range of algorithms and can use both CPU and GPU, making it one of the fastest in its class. In this tutorial, we will look at how to get started with hashcat using the example of cracking a SHA256 hash.
Installing hashcat
On most Linux systems, hashcat can be installed directly via the package manager:
sudo apt update
sudo apt install hashcat -y 
For Windows, an official build is available, which can be installed from official site. Check the installation:
hashcat --version For example, let's use the string "password" hashed in SHA256:
echo -n "password" | sha256sum Result: 5e884898da28047151d0e56f8dc6292773603d0d6aabbdd62a11ef721d1542d8
Create a file with the hash:
echo "5e884898da28047151d0e56f8dc6292773603d0d6aabbdd62a11ef721d1542d8" > hash.txt Create a simple dictionary:
echo -e "123456\npassword\nqwerty" > dict.txt 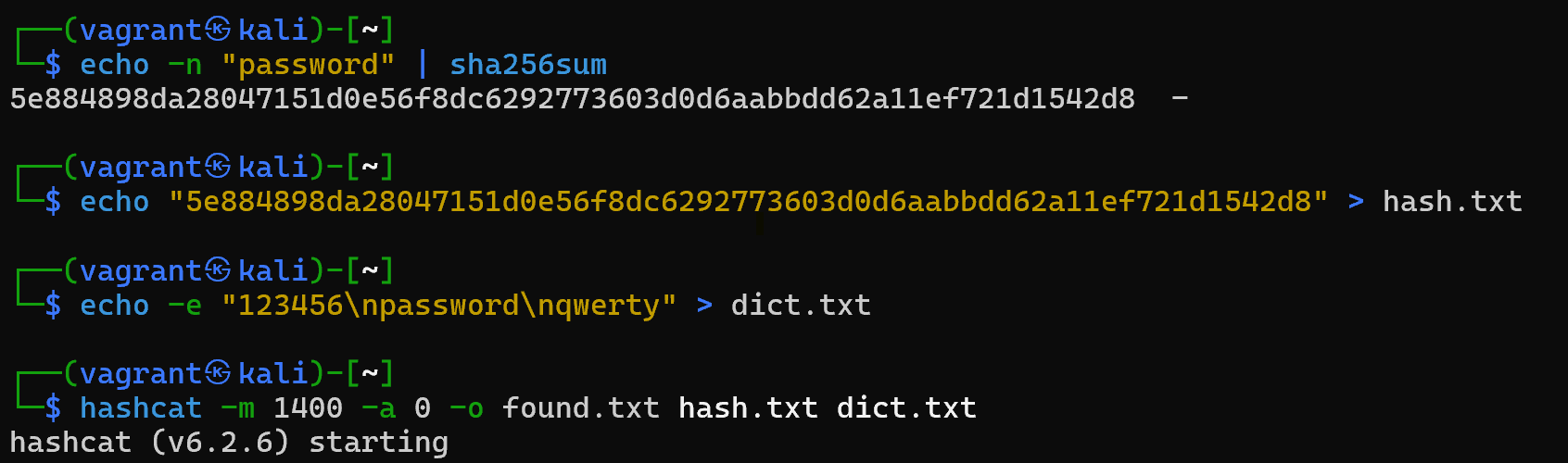
Hashcat uses numeric codes to denote algorithms. For SHA256, it is 1400.
Run the search:
hashcat -m 1400 -a 0 -o found.txt hash.txt dict.txt Parameters:
- -m 1400 — SHA256 mode
- -a 0 — dictionary attack
- -o found.txt — file to save found passwords to
After completion, check the result:
cat found.txt Example output:
5e884898da28047151d0e56f8dc6292773603d0d6aabbdd62a11ef721d1542d8:password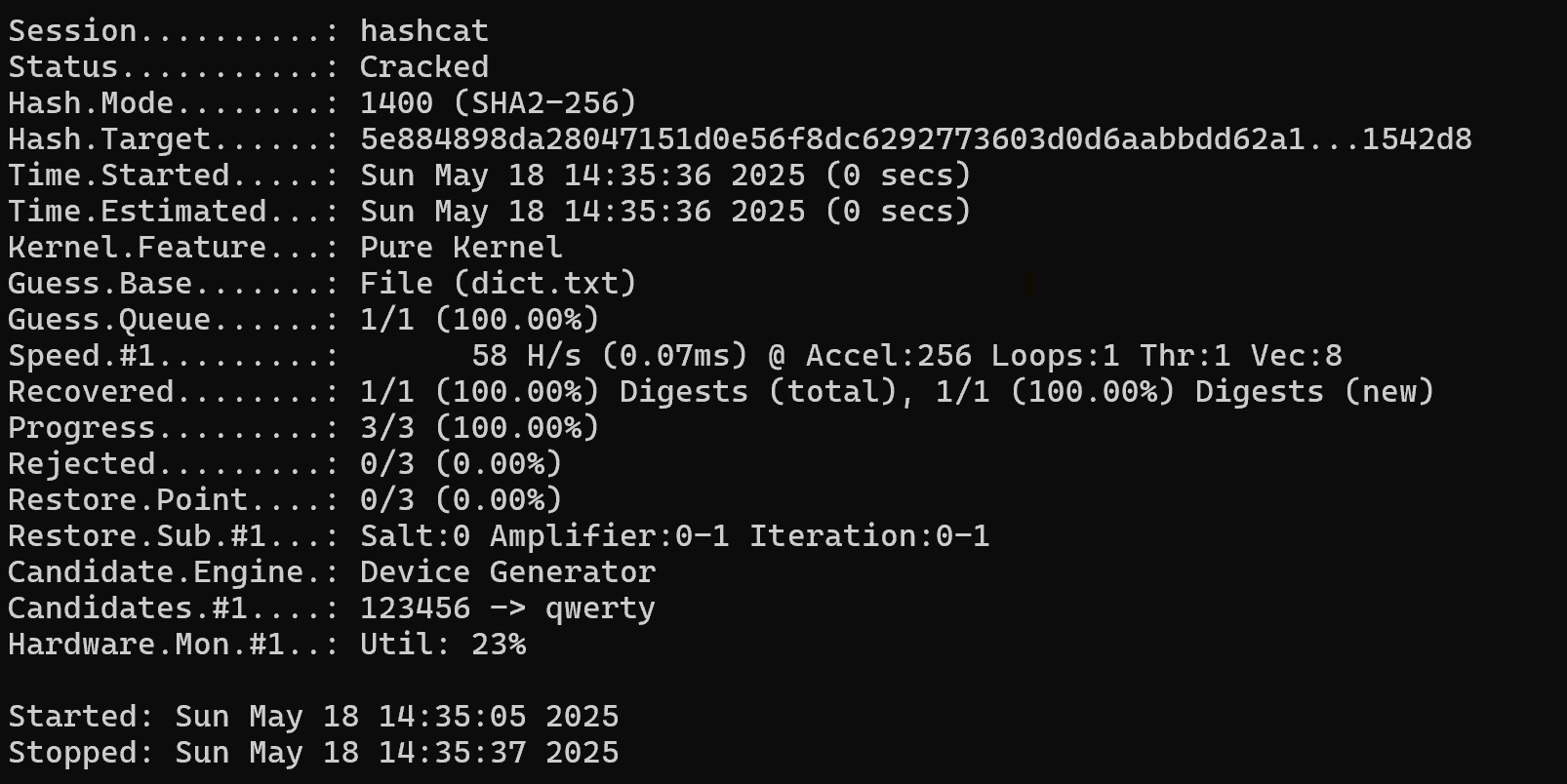
Useful parameters for iterating over values:
- --force — use even if incompatible with hardware
- --status — display process status
- -w 3 — set performance (from 1 to 4)
If you no longer plan to use the files:
rm hash.txt dict.txt found.txt Options for customizing the search
In addition to the standard attack method, you can also use masks, their combinations with dictionaries:
| Code | Attack type | Description |
|---|---|---|
| 0 | Dictionary | Dictionary attack (password file) |
| 1 | Combination | Combination of two dictionaries |
| 3 | Brute-force | Mask/pattern attack |
| 6 | Hybrid Dictionary + Mask | Dictionary + mask (example: password123) |
| 7 | Hybrid Mask + Dictionary | Mask + dictionary (example: 123password) |
The table below shows possible masks for composing template:
| Mask | Value |
|---|---|
| ?l | lowercase letter |
| ?u | capital letter |
| ?d | digit |
| ?s | special character |
| ?a | any character |
For example, you can brute force an 8-character password using a mask:
hashcat -a 3 -m 0 hash.txt ?d?d?d?d?d?d?d?d Or use combined options:
hashcat -a 6 -m 0 hash.txt dict.txt ?d?d Hashcat is an indispensable tool for testing password strength. Use it for legitimate tasks: security audit, training, or recovering your own data. Violating the law using hashcat is unacceptable.



