It is often necessary to protect the device from various modifications and changes at a lower level. Whether it's loading recovery images that can work with the host file system on behalf of root, or editing kernel options at boot!
In this article we will look at one of the solutions to this problem, such as setting a password on Grub!
What is Grub?
Grub is a programme that takes control first after the BIOS/UEFI boot and allows you to define the image and settings that you want to run next. For example, this solution is useful when you have two or more operating systems or images on your device that can allow you to perform recovery work on the OS.
Bootloader loading depends on which partition table disc is used to store it. For example, from an MBR partition table, the boot order is as follows:
BIOS → Selects the first 512 bytes of the boot area and transfers control (Stage 1) → Before bootloader configuration files are loaded (Stage 2) → Loads the kernel
With GPT partitions (refers more often to UEFI) booting is different:
UEFI → Search on EFI partition (usually /boot/efi) → Directly load bootloader.efi → Load kernel
An intruder can exploit the features and functionality of this solution to gain access to bypass security measures! As a countermeasure, consider installing a password on grub, which will close some of the vulnerabilities at its level.
How to set a password on Grub?
Authentication data for Grub is stored in the /etc/grub.d/ directory file and is a combination of login and hashed password. So to make a new one, we need to create an entry in the file. Beforehand, let's prepare the password with the grub-mkpasswd-pbkdf2 utility:
grub-mkpasswd-pbkdf2 | sudo tee -a /etc/grub.d/40_custom 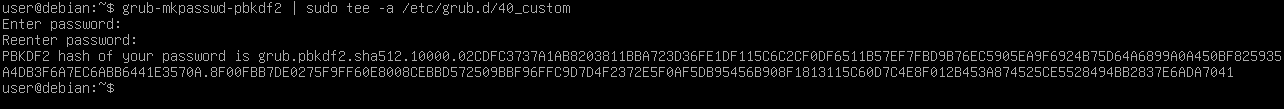
Let's go to the /etc/grub.d/ file and delete the extra lines that are left due to output redirection, and add a couple of lines about the user. As a result, we will get the following line at the end of the configuration file:
set superusers="username"
password_pbkdf2 username grub.pbkdf2.sha512.<long_hash>
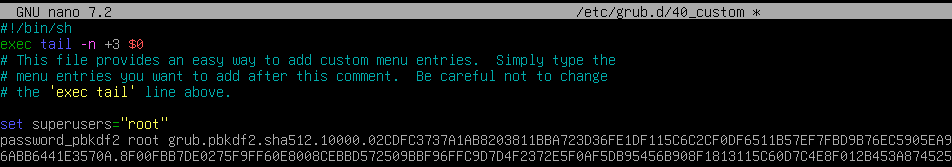
Let's explain each of the items in this context:
- set superusers - sets the username to be considered superuser in the context of GRUB;
- username - this is the username for which you set the password;
- password_pbkdf2 - specifies that you should use PBKDF2 hash to verify the password;
- username is the username for which you set the password;
- grub.pbkdf2.sha512.<long_hash> is the password hash generated with grub-mkpasswd-pbkdf2. GRUB will compare the password entered by the user with this hash.
Then exit and save the file and compile the bootloader config from it:
sudo update-grub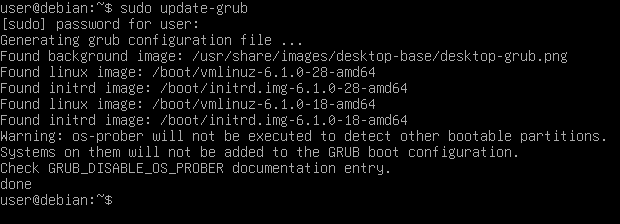
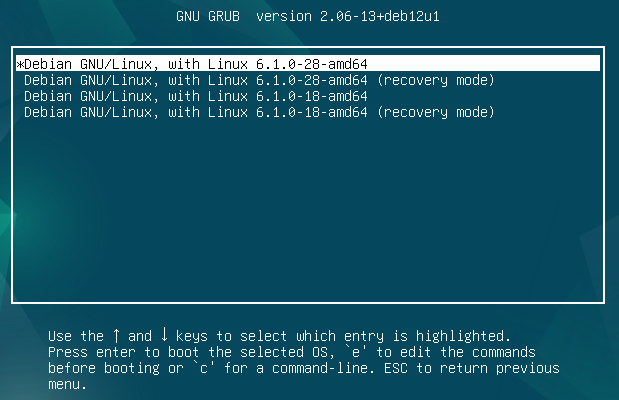
Restart the device and wait for the bootloader, then select one of the images:

Great, the password protection works and will not let you boot into the OS without knowing the bootloader password. As a result of executing these commands you should get a list of parameters of the requested objects. If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

Conclusion
Setting a password on GRUB is an effective way to secure your system’s bootloader from unauthorized access and potential tampering. By using grub-mkpasswd-pbkdf2 to generate a hashed password and updating the GRUB configuration, you ensure that only authorized users can modify boot parameters or access recovery images. This simple step enhances system security at a low level, protecting your operating systems and sensitive data from intruders. Once configured correctly, GRUB password protection works seamlessly without affecting normal boot operations.
FAQ
- Q1: Why should I set a password on GRUB?
A: Setting a GRUB password prevents unauthorized users from editing boot parameters, loading alternative OS images, or accessing recovery modes, which could compromise system security. - Q2: Can I use any username for GRUB password protection?
A: Yes, you can define any username as a superuser in GRUB. This username will be associated with the password used for authentication. - Q3: What happens if I forget the GRUB password?
A: If you forget the password, you won’t be able to access the bootloader options. In such cases, you may need physical access to the system to reset the password or edit the GRUB configuration from a live Linux environment. - Q4: Does this work on both MBR and GPT/UEFI systems?
A: Yes, GRUB password protection works on both legacy BIOS/MBR systems and modern UEFI/GPT systems. - Q5: Is the password stored securely?
A: Yes, the password is stored as a PBKDF2 hash in the GRUB configuration, which ensures it is not saved in plain text and is resistant to basic attacks.



