Cryptographic means of information protection are the basis of the information system protection system. They realise secure data transmission via VPN, reliable storage of data in encrypted form on computing devices, secure transmission of letters with encryption. And also allow you to put a digital signature, which will confirm the integrity and authenticity of transmitted data.
One such solution is GPG or GNU Privacy Guard, which is an open implementation of a cryptosystem. A set of modules that allow to perform cryptographic transformations: encryption, signature, storage of public and private keys. It is the last two modules are an integral part of any tool. In GPG it is called a key ring!
What is a GPG key ring?
GPG key ring or literally keyring, is a set of public and private keys, information about which is stored in files. For more convenient and secure interaction, public and secret keys are separated into two different storage locations, a base with public keys and a folder with private keys:
- pubring.kbx
- private-keys-v1.d
Given the specifics of how public keys are used, they constantly need to be accessed, so they are not stored in encrypted form, unlike secret keys. However, the ability to spoof a public key provides a new attack vector and sensitive data can be sent to the attacker.
Private keys require strong security measures, so each key is stored separately and encrypted with a password set by the user. Security is based on a complex password, encrypted key and the same access delimitation.
To view the list of public and private key mappings, use the command for secret and public keys:
gpg -K && gpg -k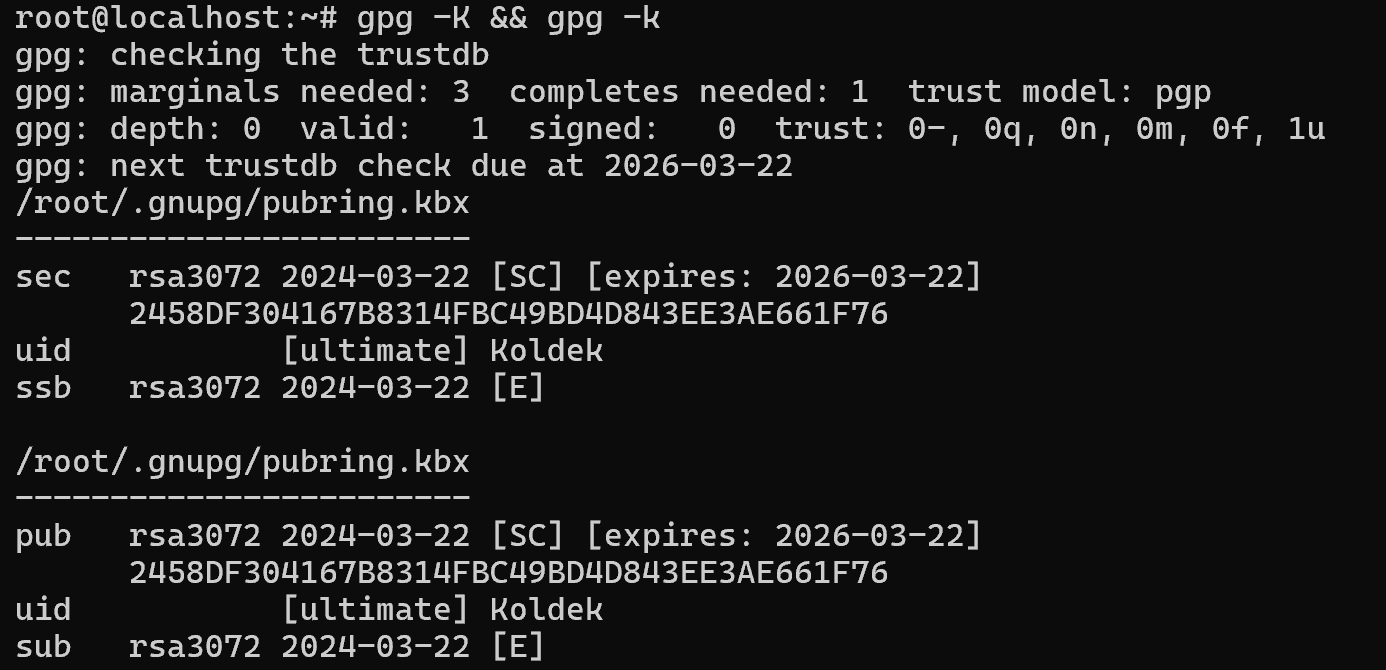
On the image you can see that the information about mappings was obtained from pubring.kbx, because it stores public keys and information related to them, which allows you to determine the ownership of the key. Including secret keys, their hash values and UIDs of users who own them.
How do I import a GPG keyring?
To do this, you can use the command:
gpg --import <file>But it is necessary to download the key itself beforehand, and a new difficulty arises in this. How to do it safely? After all, by spoofing the connection to the Mitm server with an attack, the intruder will send the malware and a different key, under the guise of a genuine one. There are two distribution methods for this:
- Web of Trust;
- a third party or a certification centre.
In these types of transfer there are trusted and untrusted objects, in the Web of Trust method we trust the official site of the company or its intermediaries. Let's consider the secure key import on the example of MySql database. To do this, let's go to the company's site and make sure that the https protocol used and the certificate belongs to the organisation:
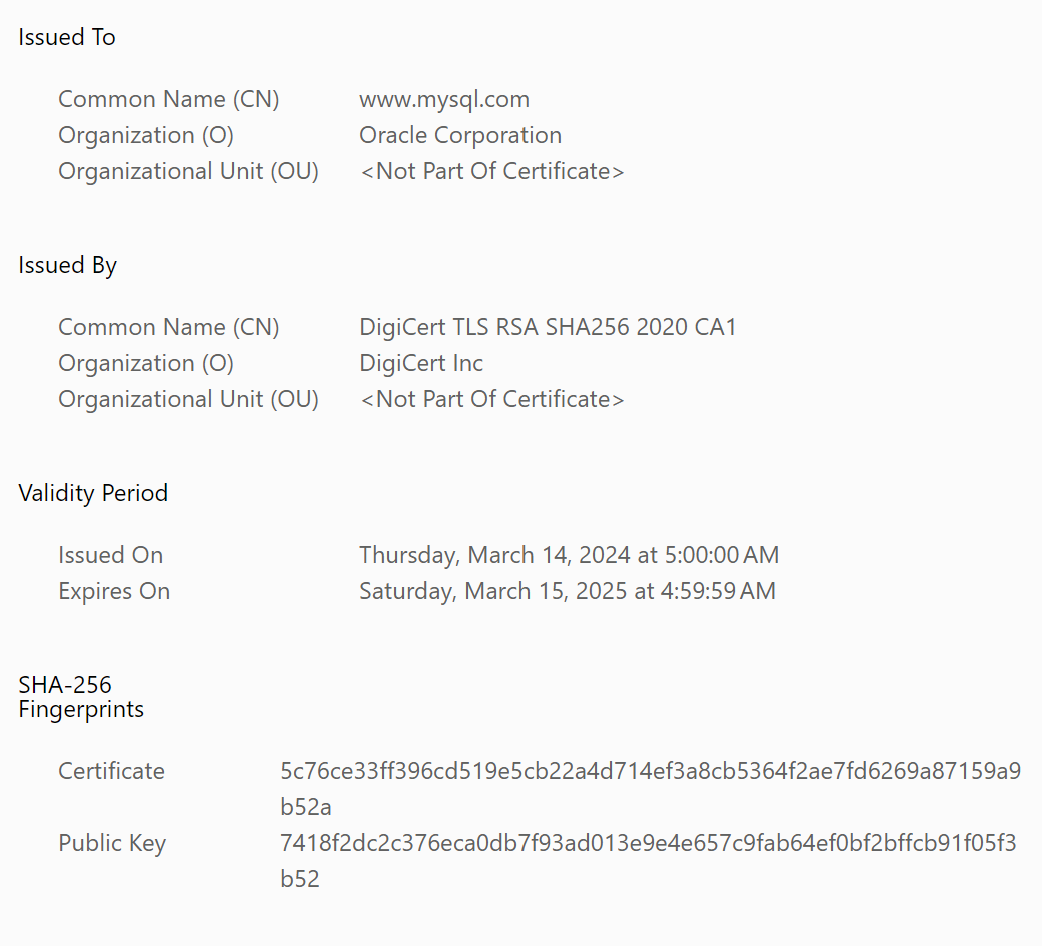
Great, Oracle owns MySQL, so if we trust the certificate authority where the verification was performed, we can continue. Let's go to the tab that offers several ways to use the public key. There are usually three options:
Copy from the site, in order to eliminate additional transmission over an untrusted communication channel and to avoid new attack vectors with file spoofing on the host. The MySQL website provides an example:
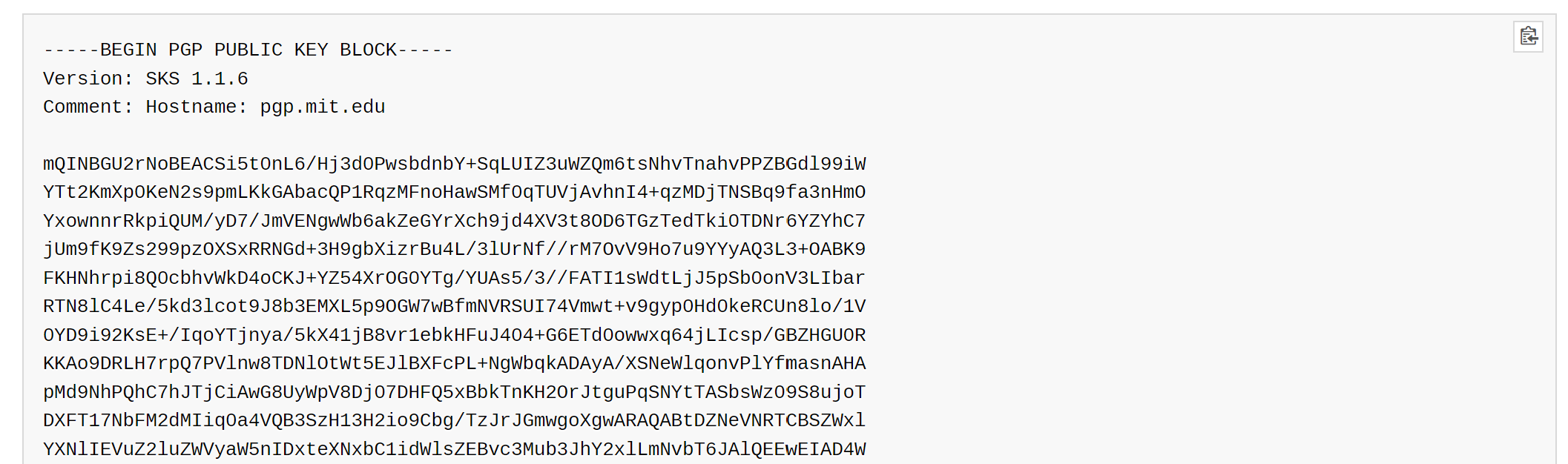
Usually, one unique key is formed and all necessary files and packages are signed with it. In this case, let's copy the key and go to our device where we need to add it. For more clear demonstration all steps in the tutorial can be performed on powerful cloud servers.
It will take some time to deploy server capacity. After that you can connect in any of the convenient ways. And let's move to the terminal with our OS!
Let's create a file called key.gpg, it's up to you to choose how to name the file, but the format should be .gpg. This is what is used when importing:
nano key.pgp 
A text editor will open, paste the public key and import with the command:
gpg --import <file> De-arming as the process of converting from source format to target format:
gpg --dearmor <filename.pgp> -o /usr/share/key.gpg && gpg --import\
/usr/share/key.gpg
After which the key import will take place:
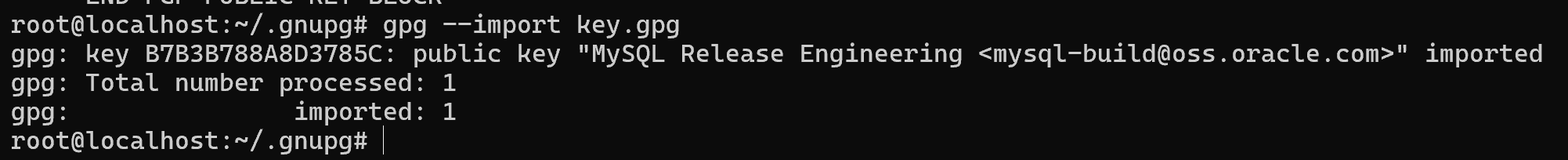
After that, we can use it!
How do I remove GPG keyring?
In order to remove a key from a keychain you need to specify the owner or the key ID in the command:
gpg --delete-secrete-key <key-id>.
And for public keys:
gpg --delete-key <key-id>All key information can be viewed with the command in the instructions above!
How do I export my GPG keyring?
To export keys we need two commands, for public keys:
gpg -a --export <key-id> > pub_key.ascThe -a option allows you to arm the key in ASCII and transmit it in mail, messenger or post it on your website.
gpg -a --export-secret-keys <key-id> > secret_key.ascNote that in most cases the secret key will almost always remain on the machine, except when you need to delegate your signature or decryption of cipher messages to a trusted object.



