For correct work with files file systems were developed, which allow to set a single standard of data storage. It allowed to solve the problems of large size of stored data, long indexing, as well as deduplication and integrity control.
A file system is a set of rules or an algorithm by which data is organised and stored in a certain form so that it can be accessed by the OS. It also regulates the behaviour of files by its attributes and allows you to set certain parameters that can prohibit the deletion of files even to the root user! Let's consider their operation and management in this article.
How does the file system work?
A data storage device stores information as a long set of ones and zeros in a binary system, where they are organised into groups, thanks to a logical abstraction - the file system. Each file has its own headers, metadata, attributes and payload - the information itself.
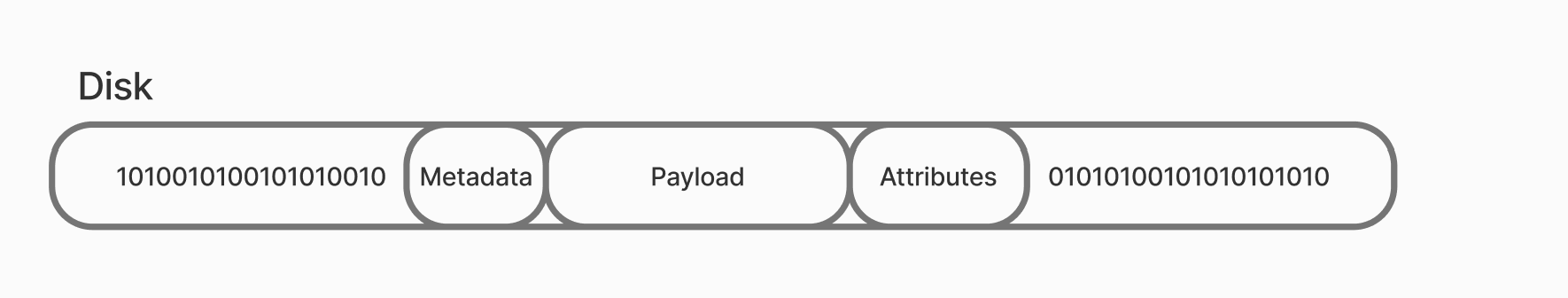
When accessing files, the user creates a system call, which is sent to the OS kernel. The kernel interacts with the file system itself, where it reads the attributes it needs. There are two types of attributes: access rights and behaviour flags. These are still attributes or properties of the file, but each of them has its own function.
The standard rwx access rights, which you have seen everywhere, define the rules for accessing sub objects to objects and are used in higher-level modes of operation. And behaviour flags define options for how files will be handled and they work at a lower level. So root, when working with a file that has the -i or immutable flag, will not be able to delete or modify it. The entire list of attributes is listed in the table below:
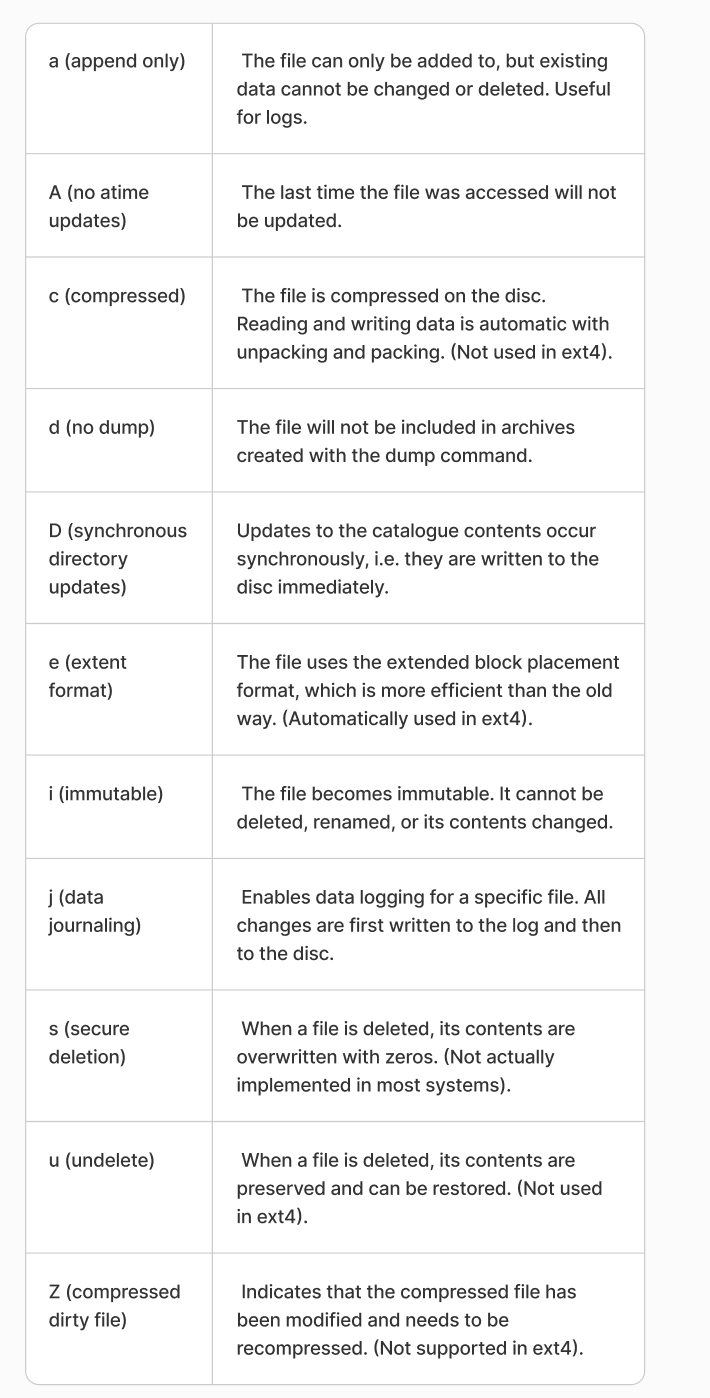
The list is quite impressive, so let's look at the main ways flags can be used in practice!
Attribute management
If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

Let's imagine that we are collecting logs from a machine and it is important that no one can tamper with them in order to preserve data integrity. For this purpose, the file system has an attribute that we can assign to a file:
sudo chattr +a /var/log/auth.log 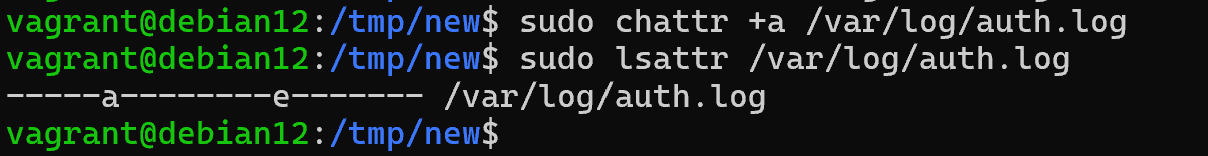
You can view whether the attribute has been applied via the command:
lsattr /var/log/auth.log After that, it will not be possible to change the data until a user with administrative rights removes this attribute with the opposite command:
sudo chattr -a /var/log/auth.log 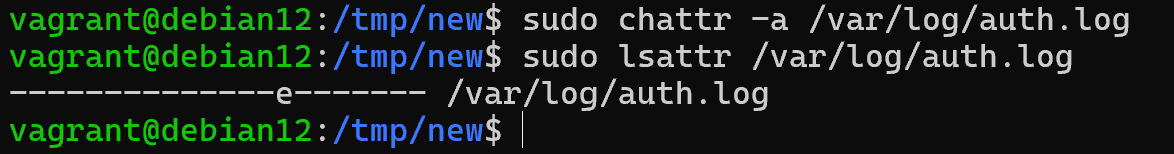
In order to prohibit file deletion or modification, let's write the command and check its operability:
sudo chattr +i /var/log/auth.log && sudo rm /var/log/auth.log 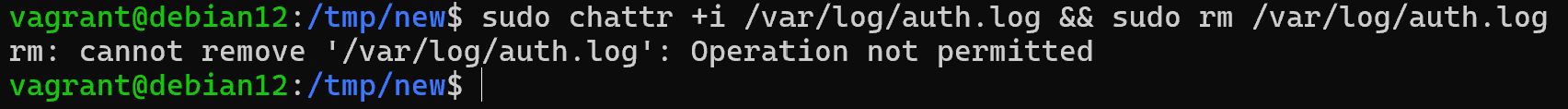
Immediately after the attribute has been given, when the file system is accessed, it will refuse to perform actions to modify the file. It can be used as a protection against accidental deletion for admins or as an additional work rule for ordinary users who already have access to files.
Also for files it is possible to switch on journaling, it will allow to save the list of actions with files in a separate log. This will help when restoring the integrity of the system itself. However, this function is usually specified directly when installing the file system.
These attributes allow you to add low-level functionality to change, which only the administrator can. They override the standard access differentiation system by making changes globally for all users of the system. Such a solution is useful when an intruder has gained access to an account. Which has the ability by permissions to modify files, but this is forbidden by the file system attribute, only if it is not root.



