The main entities when working with an operating system are processes and threads. They determine the execution context of the software and what actions should be performed. In this article we will answer the questions in detail.
What is a process and a thread? Why do we need an initialisation system like systemd in an OS? What tools can be used to work with processes? And how can intruders exploit them?
What is a process and a thread in Linux?
A process is an abstract, passive entity or object that lives in the kernel of the operating system and has attributes necessary for software operation. Basically, these are fields such as:
- PID - process id;
- PPID - id of the parent process;
- CMD - name of the running software;
- Current Working Directory - working directory of the software;
- Signals - signals processed by the software.
When a user runs a utility, the shell it is in sends a request to the kernel, going from user space to kernel space using a system call.
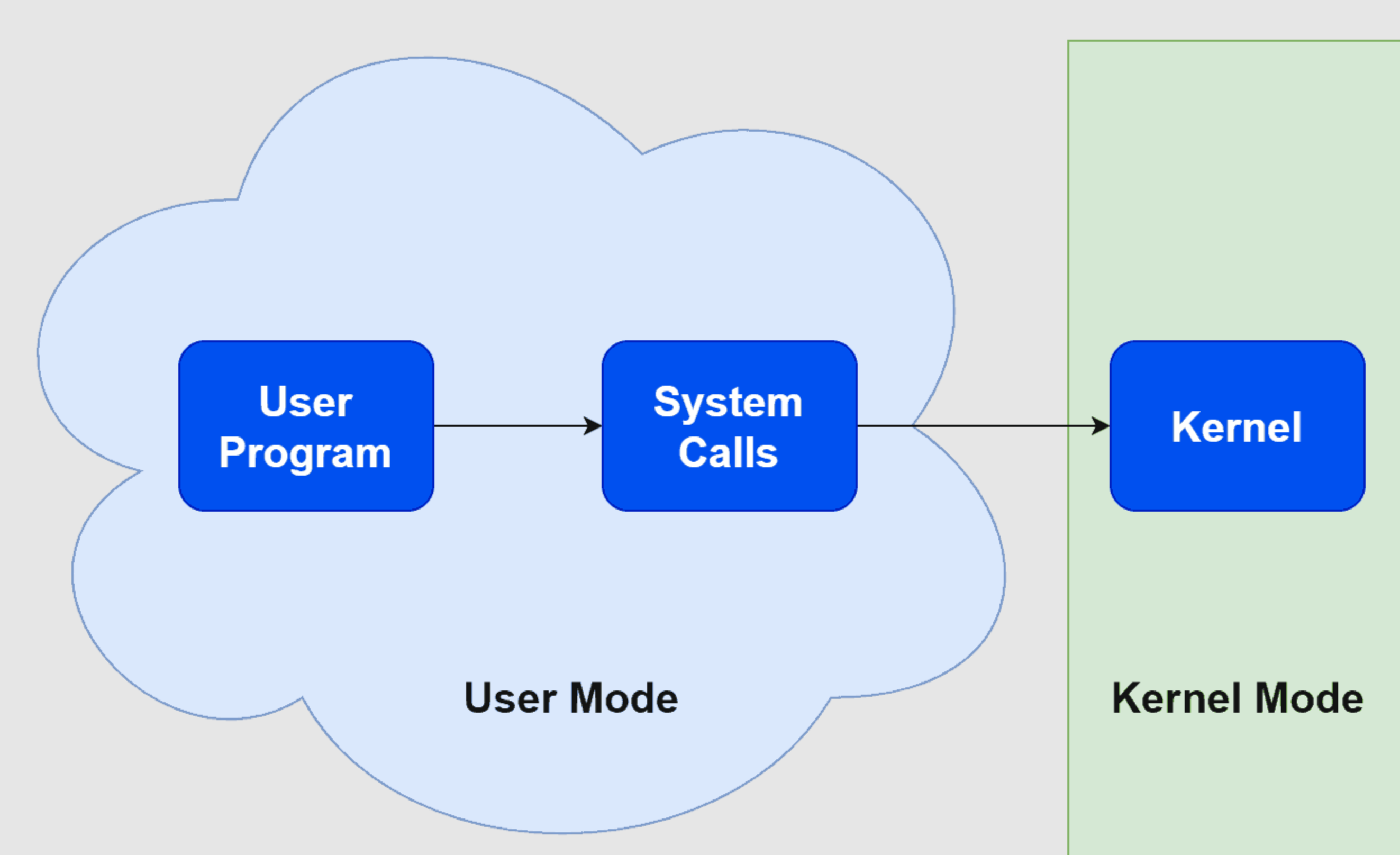
For example, to write data to a new file, the shell calls the appropriate system call. After the kernel receives this call, it processes it and determines which process it belongs to and launches the appropriate execution actions or threads. Threads are the active entities of the process and are engaged in executing the instructions passed by the system call.
What is the birth cycle of processes in Linux?
If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

It is important to understand the Linux process birth cycle. There is only one process that is started by the kernel at boot - systemd. The rest of the processes are started in the parent-descendant process format. This means that at software initialisation, systemd creates a fork(2) system call, which literally tells the kernel to create a copy of systemd. With the same resources as it has, so as long as the memory allocated to work remains the same. Once created, the new process is assigned a PID and PPID or the id of the parent process.
To make a copy of the running parent process into a ‘different utility’, an exec() system call is made inside the child process, which requires the kernel to replace the files in memory with the executable files of the new software. You can see the sequence more schematically in the figure below.
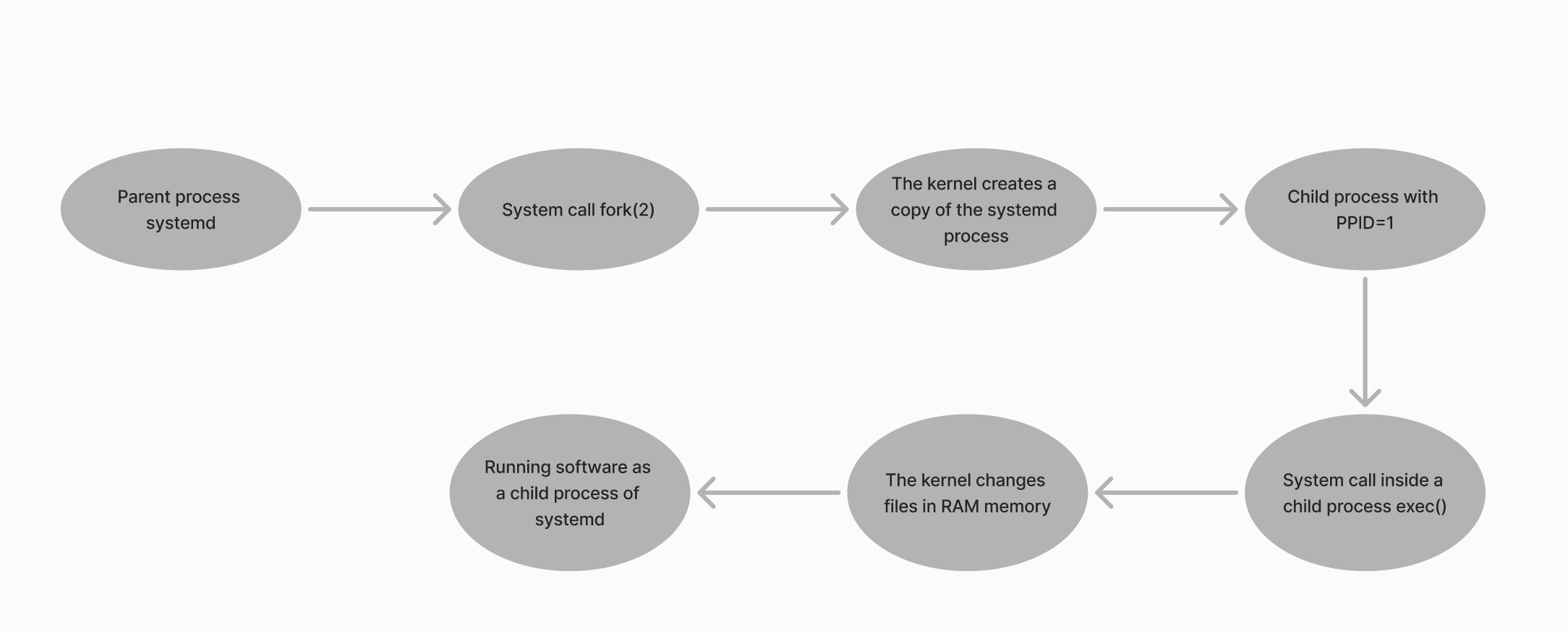
Thus, it turns out that the branch of running software will look hierarchical: one process started another. But how will this look, when connecting a client to an SSH server to manage Linux? Or how can we figure out who is the malicious process that ran the script? Let's look at this using the htop utility, which can be installed via the package manager:
apt install htop
Let's start and browse the existing process tree by pressing F5:
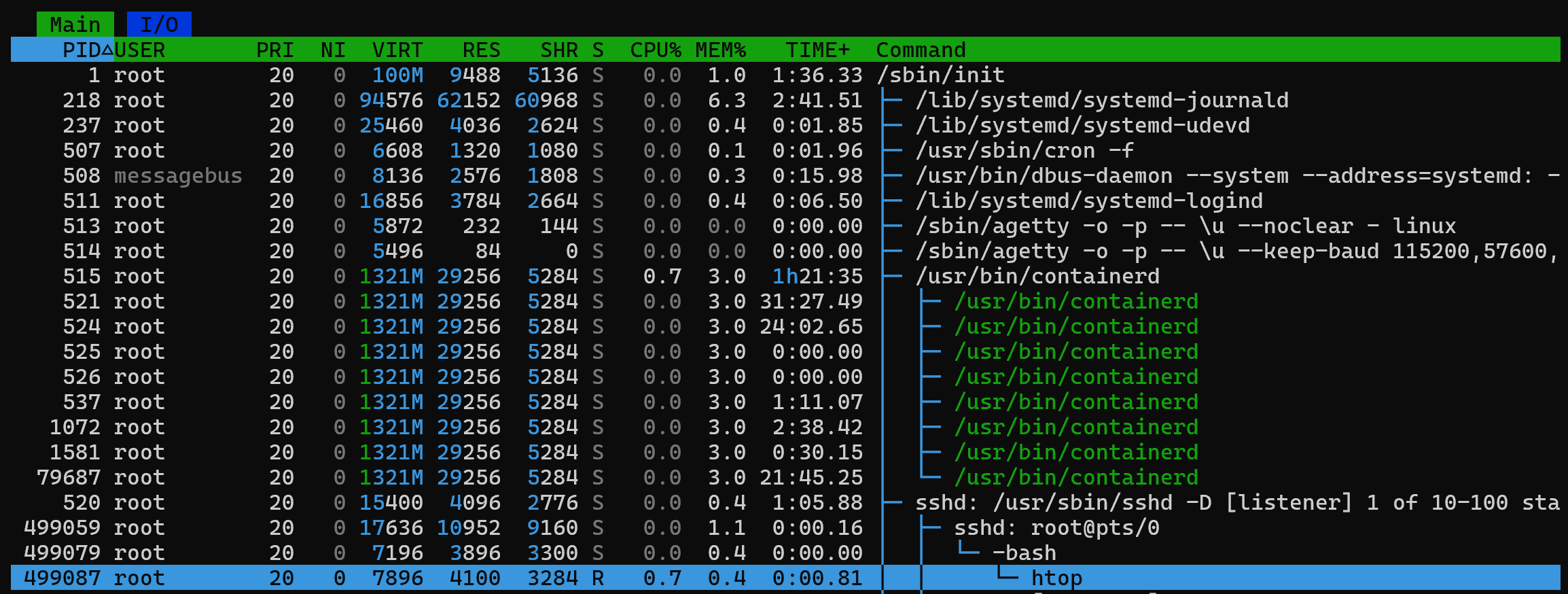
Note the first line, where the process PID=1 is specified - this is the systemd initialisation system, from which the other child processes are started. On the right, the Command column shows the running software and branches, where one of the child processes of systemd is sshd. And already its child process manages the remote SSH session root@pts/0, where a bash shell has been launched to manage the system, where the user is sitting. And just below we can see the htop utility with PID 499087 running.
How do I check for malicious activity in Linux?
As we have learnt above, any connection to the device will be accompanied by a running terminal real or virtual as a process. Therefore, it is possible to track them with the utility:
wSimply w will allow you to display the connections to the machine at the current time, and the utility:
last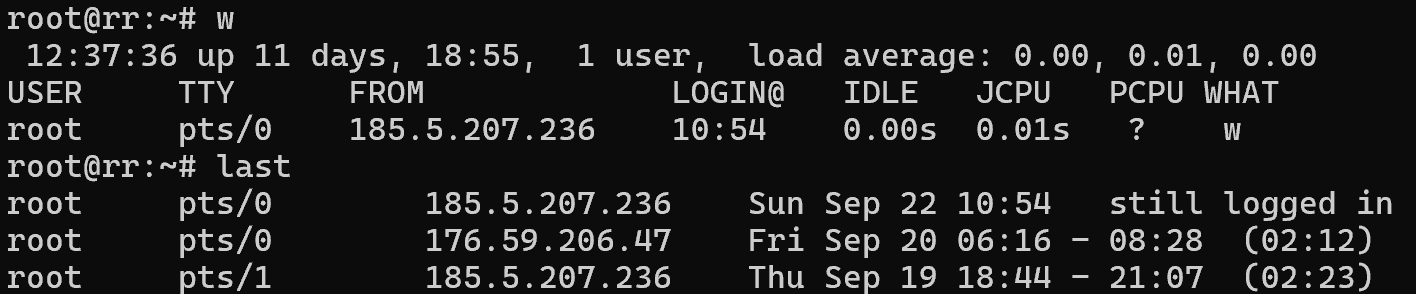
Shows the history of logging into the operating system, restarting it, and starting it from specific addresses. It is from this history that you can determine what connections were made during the entire period of the machine's operation. Pay attention to the logs of your system and the processes launched by applications, because usually a red flag, when the OS is running are software calls to the shell. A hacker needs to access the OS through the shell in order to perform a hardening or privilege escalation.
If you detect such activity, you should terminate the relevant processes, isolate the machine on the network, and investigate. The first action is solved by the kill utility:
kill -SIGKILL (pid)Instead of (pid), specify the process to be terminated, after which you can collect logs and RAM dumps from the device. Understanding how to work with processes forms a complete picture of how to manage and protect yourself with OS tools.
Conclusion
Processes and threads form the foundation of how Linux executes software and manages system resources. By understanding their lifecycle, from systemd initialization to child process creation, administrators gain powerful insights into system behavior. Tools like htop, w, and last not only simplify process monitoring but also help in detecting suspicious activity. Mastering these concepts is essential both for efficient administration and for ensuring system security.
FAQ
- Q: What is the difference between a process and a thread in Linux?
A: A process is a passive container with attributes like PID, PPID, and CMD, while threads are active execution units within a process that carry out instructions. - Q: What role does systemd play in Linux?
A: systemd is the first process started by the kernel (PID=1). It initializes the system and spawns all subsequent processes in a parent-child hierarchy. - Q: How can I view running processes in Linux?
A: You can use commands like ps, top, and htop. The htop utility is especially useful for viewing a hierarchical process tree. - Q: How can I detect malicious activity in Linux processes?
A: Check active sessions with w, review login history with last, and monitor process trees with htop. Unusual shells or unexpected processes may indicate compromise. - Q: How do I stop a suspicious process?
A: Use the kill command with the process ID (PID), for example: kill -SIGKILL <pid>. Always investigate logs before and after termination. - Q: Why is process management important for security?
A: Attackers often exploit processes to escalate privileges or persist in the system. Proper monitoring and timely response help mitigate these risks.



