One of the most important steps in infrastructure protection is an audit, which helps identify weaknesses at the initial or final stages, during the design and implementation of defence systems. Intruders use similar tactics and procedures to damage an organisation's assets, actively scanning networks, ports through which to attack and gain initial access to the infrastructure.
Today let's take a look at one of the tools that both hackers and IS specialists use to identify weaknesses in network infrastructure.
What is Nmap?
Nmap or network mapping is a multifunctional utility that allows you to scan networks to identify hosts, ports, as well as check services for vulnerabilities. The utility can scan both in passive and active mode, aggressively but quickly identifying services or machines. To install it in Linux distributions, just write the command:
apt install nmap -y And for Windows users, use an alternative package manager:
winget install Insecure.Nmap 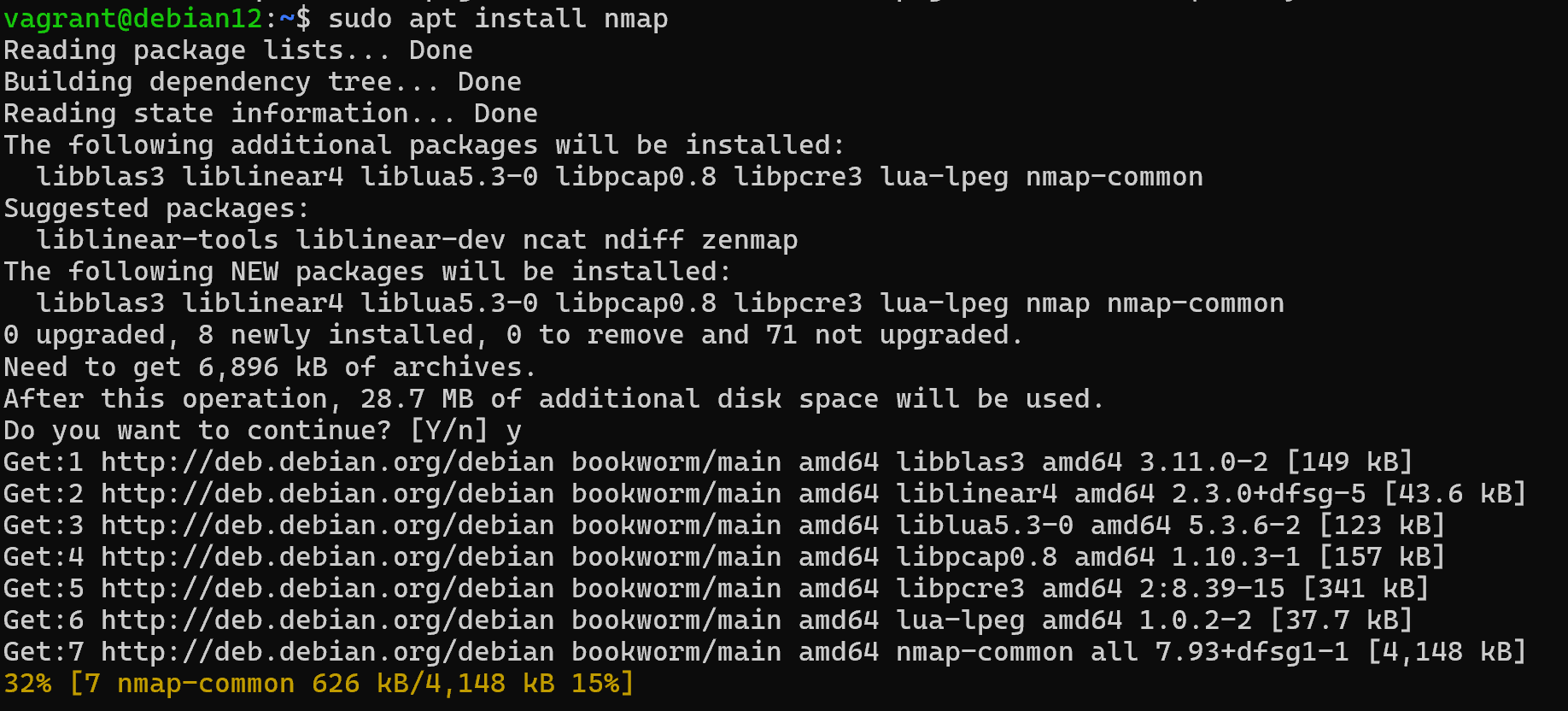
After that packages will be available on the device and environment variables will write the path to the executable file. So when you restart the terminal the nmap command will be available, check it by typing it:
nmap 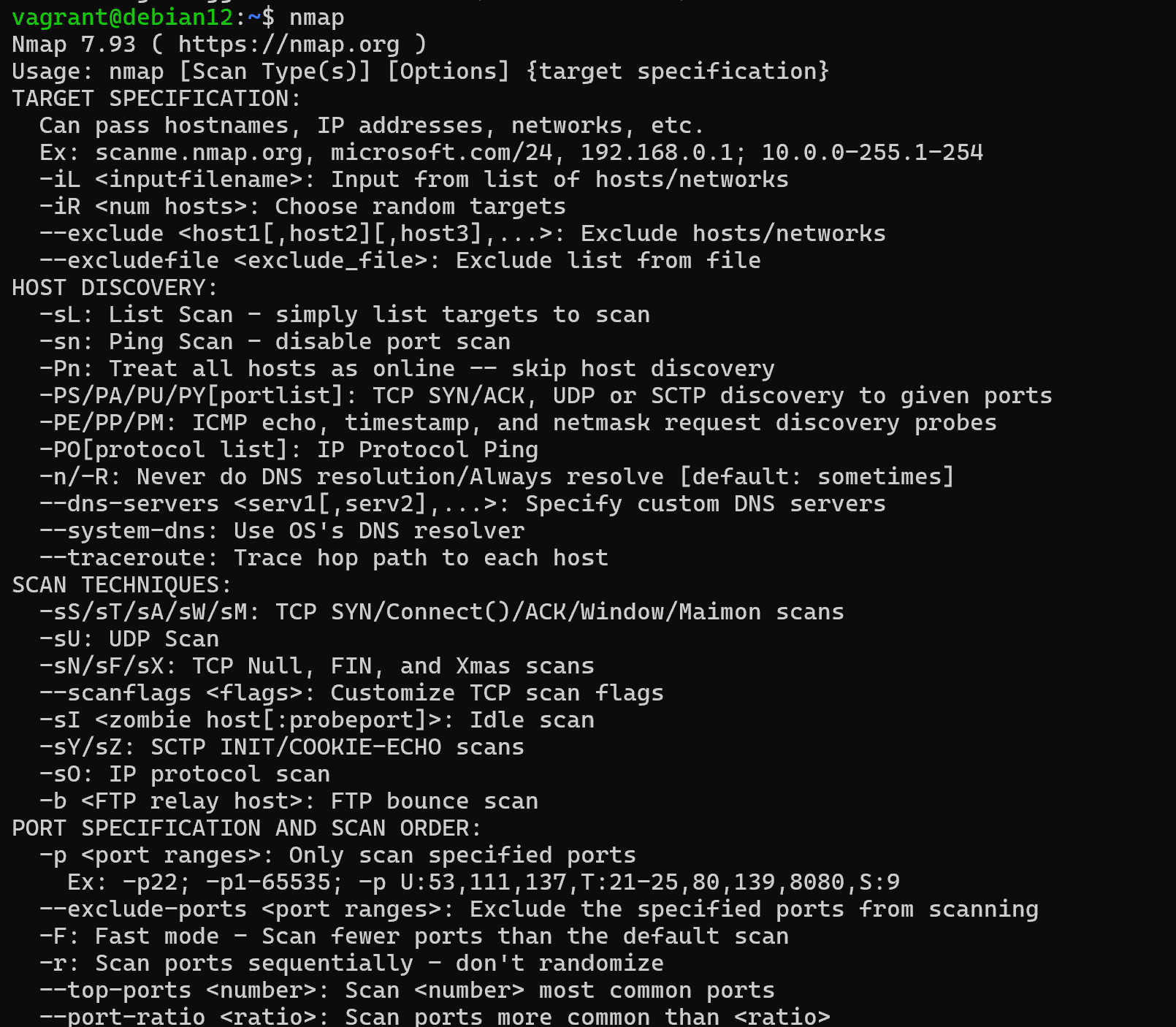
If the conclusion is that the installation was successful, just in this huge conclusion you can see several steps that are fundamental to the exploration of your infrastructure. To make it clearer, let's depict this in a diagram format:
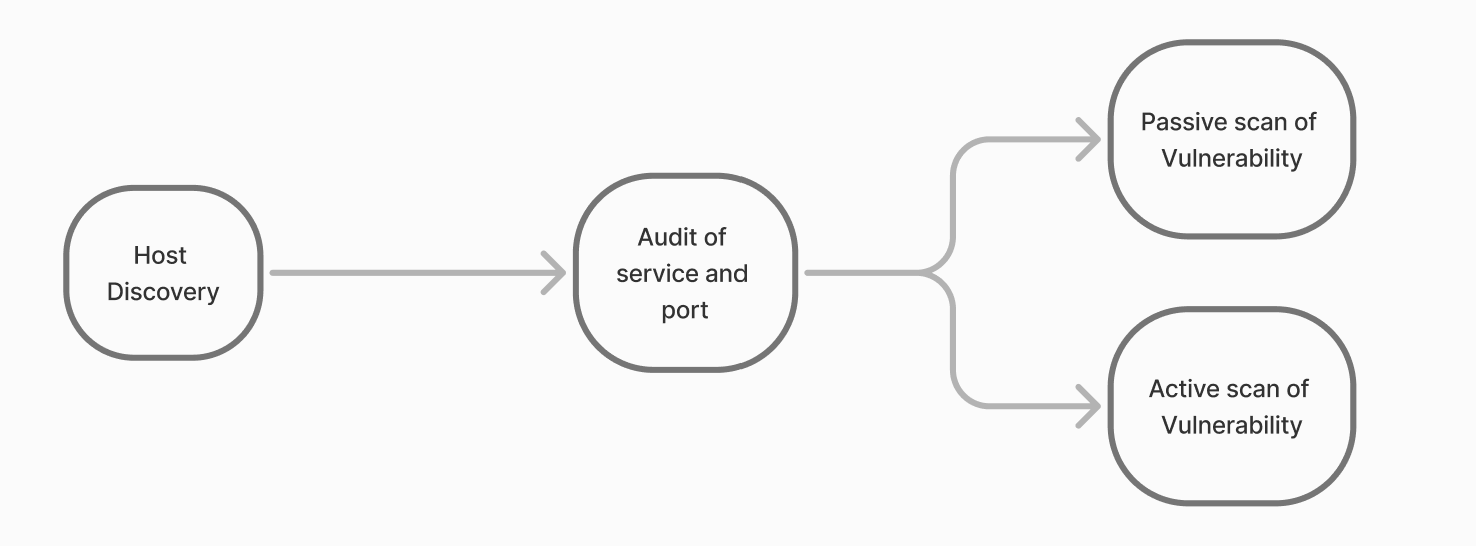
First, the array of devices is searched, this process is called Host Discovery. It allows you to determine the list of available devices on the network using various methods.
If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

How to scan hosts via Nmap?
For example, we can scan the network and determine by pinging which devices are currently available:
nmap -sn 127.0.0.0/24 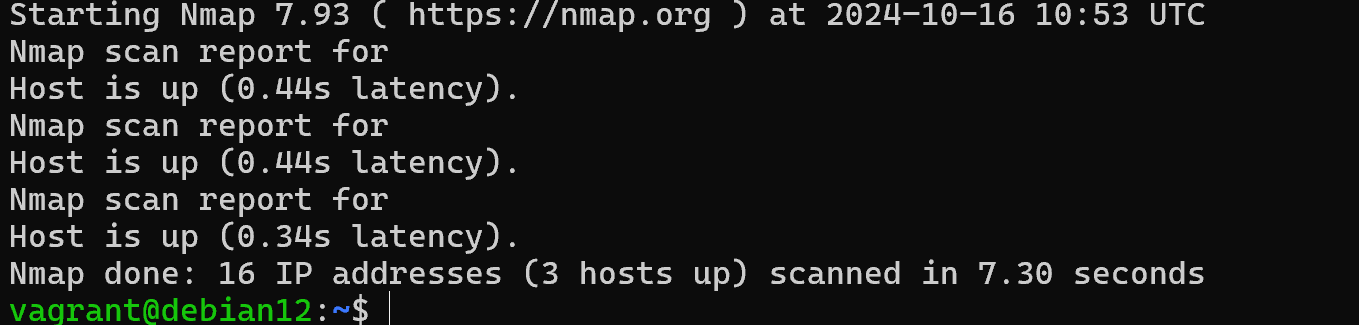
However, often the ping response can be blocked and the researcher mistakenly forms the opinion that there are no machines in the segment. For such cases, the segment is repeatedly scanned by ports to determine whether the host is up or down. The principle is based on the fact that if the service is available, then the host is also up:
nmap -PA -PS -T3 127.0.0.0/24 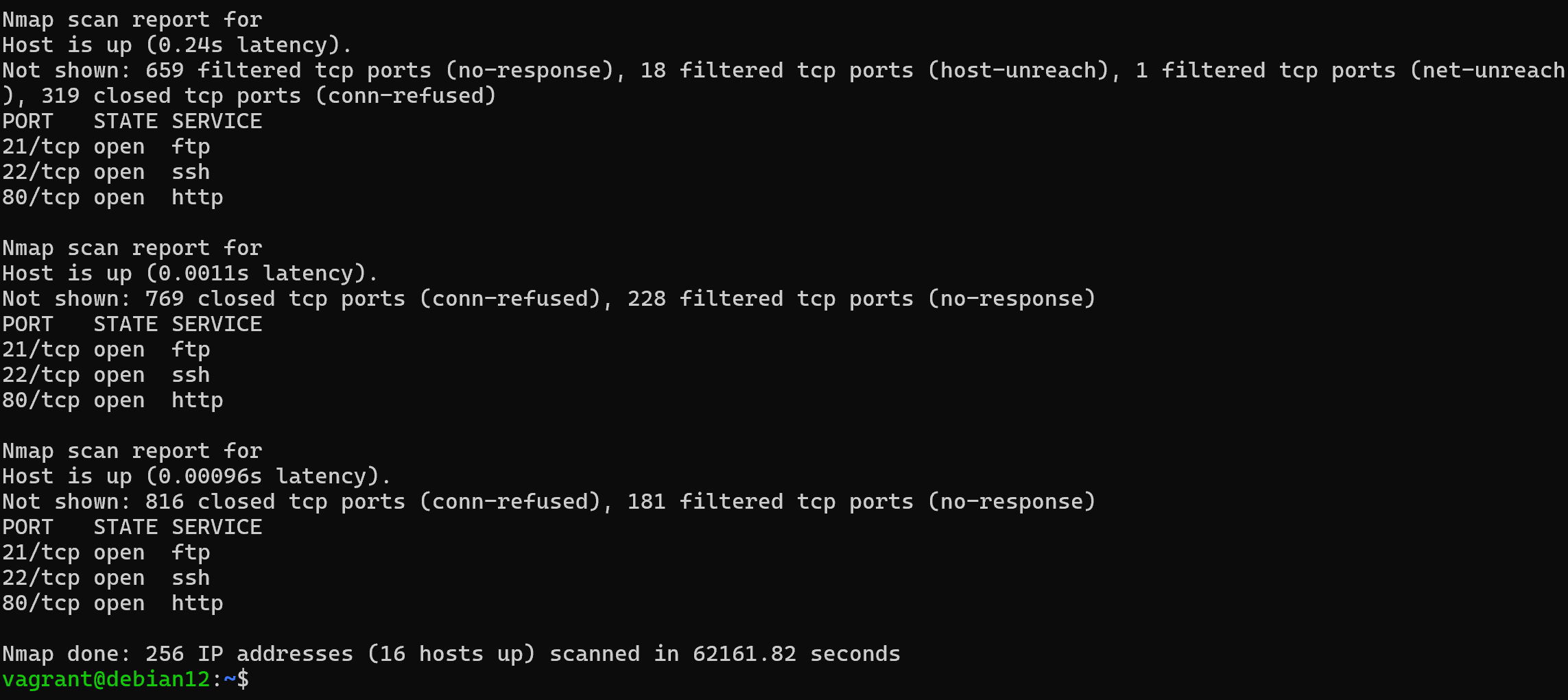
The -PA/PS option means that TCP handling of SYN/ACK packets will be used, and the -T3 flag will set a time interval that will allow a slow scan of the network. This option is great for testing your IPS and its ability to detect such reconnaissance. Also don't forget to add the -PU option, which will allow you to detect UDP services as well.
How to scan ports via Nmap?
The result should be a list of hosts with open ports that are available on the given network. Now we need to go through it and find all the services on them, if any. To do this, use the following command:
nmap -v -sV -sA -sS -sU -T3 -p U:53,T:80,21-22 4 127.0.1.1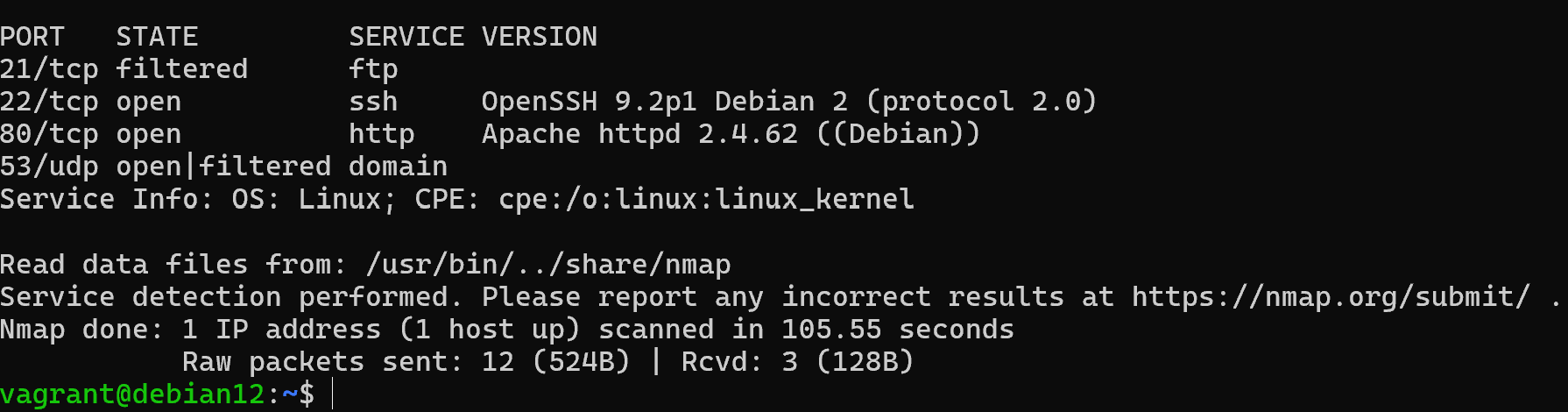
According to the results we get a list of service versions that are available by port, this approach is more delicate and allows hackers to leave less traces for the NWI. In this case we have specified only one target, but you may have more. The -sV option allows you to determine the software version that occupies the port, T3 the scanning speed parameter. And specific UDP and TCP ports with targets on which to detect them.
If you conducted Host Discovery by ICPM or the -sn parameter, you can scan ports from scratch with the command:
nmap -v -sV -sA -sS -sU -T3 127.0.1.1 --openGreat, from a network intelligence perspective we've done a machine scan of their ports and also recognised services with versions that occupy them.
Vulnerability scanning
Let's imagine that a regulator's ticket with vulnerabilities has arrived and it is necessary to check them, for this purpose we use a vulnerability scanner. This is the same nmap scanner, but with selected nse modules, which extends the functionality. To do this, go to the scripts folder and download the necessary NSE instructions in Lua:
cd /usr/share/nmap/scripts && \
apt update && apt upgrade && \
sudo git clone git@github.com:vulnersCom/nmap-vulners.git 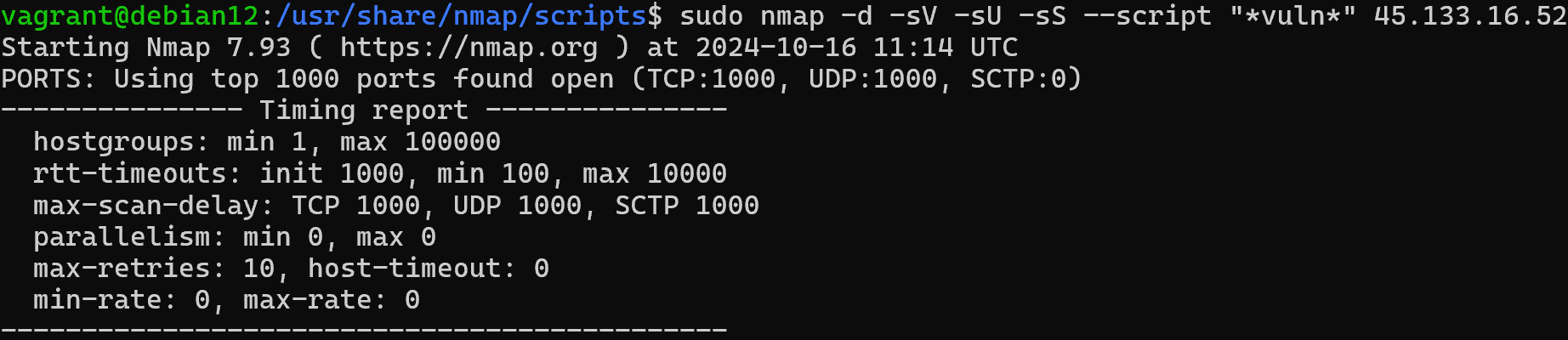
After downloading the scripts they can be called into the utility from anywhere, let's scan our ports, either completely or in a range using the -p option. Let's write the command:
sudo nmap -d -sV -sU -sS --script "*vuln*" 127.0.1.1 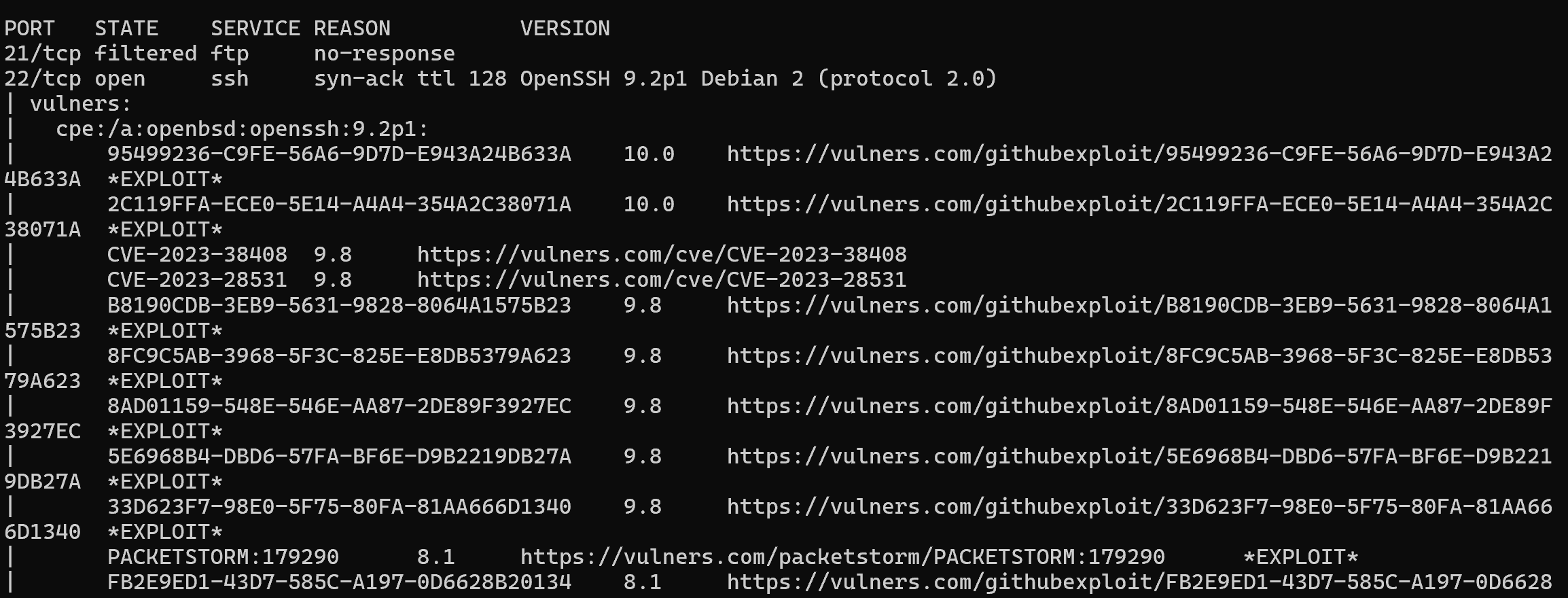
After that, the results will show all possible CVEs, which are presented according to the version of the detected software. This method of vulnerability scanning is considered passive, as it reads and compares the versions with the vulnerability database. Software developers may close a gap within one version or the employees themselves may come up with a way to patch the vulnerability. Therefore, not always what is found corresponds to what is actually found, pay attention to this! Once the list of vulnerabilities has been obtained, it is necessary to go through the infrastructure manually and check if the service is vulnerable.
Conclusion
Nmap remains one of the most powerful and flexible tools for network reconnaissance and security auditing. With just a few commands, administrators and security specialists can discover hosts, detect open ports, identify running services, and even check for known vulnerabilities using NSE scripts. While attackers may use Nmap for malicious purposes, IT professionals can employ it to strengthen infrastructure and eliminate weak points before they are exploited. Always remember to scan only authorized targets, and use the results as part of a broader cybersecurity strategy.
FAQ
- 1. What is Nmap used for?
Nmap is a network scanning tool that helps discover hosts, open ports, running services, and potential vulnerabilities in IT infrastructure. - 2. Is Nmap legal to use?
Yes, but only if you scan systems you own or have explicit permission to test. Unauthorized scanning of third-party networks can be illegal and may be considered an attack. - 3. Can Nmap run on both Linux and Windows?
Yes. On Linux, it can be installed via apt install nmap, and on Windows via winget install Insecure.Nmap. - 4. What’s the difference between host discovery and port scanning?
Host discovery checks which devices are online in a network segment, while port scanning identifies open communication channels and the services running on them. - 5. How can I detect vulnerabilities with Nmap?
By using NSE (Nmap Scripting Engine) modules such as --script "*vuln*", Nmap can compare detected software versions against known CVEs from vulnerability databases. - 6. Does Nmap scanning affect network performance?
Yes, aggressive scans can consume bandwidth and trigger alerts in IDS/IPS systems. Use slower timing options (e.g., -T3) for less intrusive scanning. - 7. Can attackers use Nmap in the same way as security specialists?
Yes. Hackers use Nmap for reconnaissance before launching attacks. This is why organizations should also use it proactively for defense and auditing. - 8. How accurate are Nmap vulnerability scan results?
They are indicative but not always 100% accurate. A found CVE may not apply if the service is patched. Manual verification is required to confirm real risks.



