Almost the entire business segment moved into the environment of information systems and technologies, which made it possible to automate routine tasks, build a complex chain of communications, and increase profits. They have built their own secure corporate infrastructure loops, as well as services that are inside, but accept connections from outside as well.
Many intruders are targeting them, so it is important enough to understand what tools can be used and what OSINT techniques they use.
What is OSINT?
OSINT or Open-source Intellegence is a direction of searching and analysing information on open data. Usually the volume of data is chaotic and unstructured, but we can conditionally divide the information into technical and applied data.
In this article we will consider only technical aspects of OSINT intelligence. Many of the machines that are used to build the company's loop infrastructure store sensitive information that can be used to attack it.
.
One method of analytics is to examine the outer perimeter of the infrastructure and look for all possible entry points. The algorithm is a step-by-step checklist:
- Finding the organisation's domain and identifying its main characteristics (CDN usage, NS records, organisation's ASN, SSL certificate, IP address) that will allow to generate a lead, when investigating the infrastructure;
- Based on the artefacts found, investigate all possible subdomains of the organisation;
- Find alternative domains;
- Investigate the organisation's certificate against the open crt.sh databases;
- Perform a query to the NS server and attempt to collect records.
Let's look at the steps in more detail and learn how to use the tools for each of them.
A study of the domain record
If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

Let's imagine that the target of the research is a certain company with the domain hackeru.com, which we found through a regular search query. Let's analyse the domain record using a whois utility or a web service, paying attention to the main attributes of the domain. The utility can be installed through the package manager:
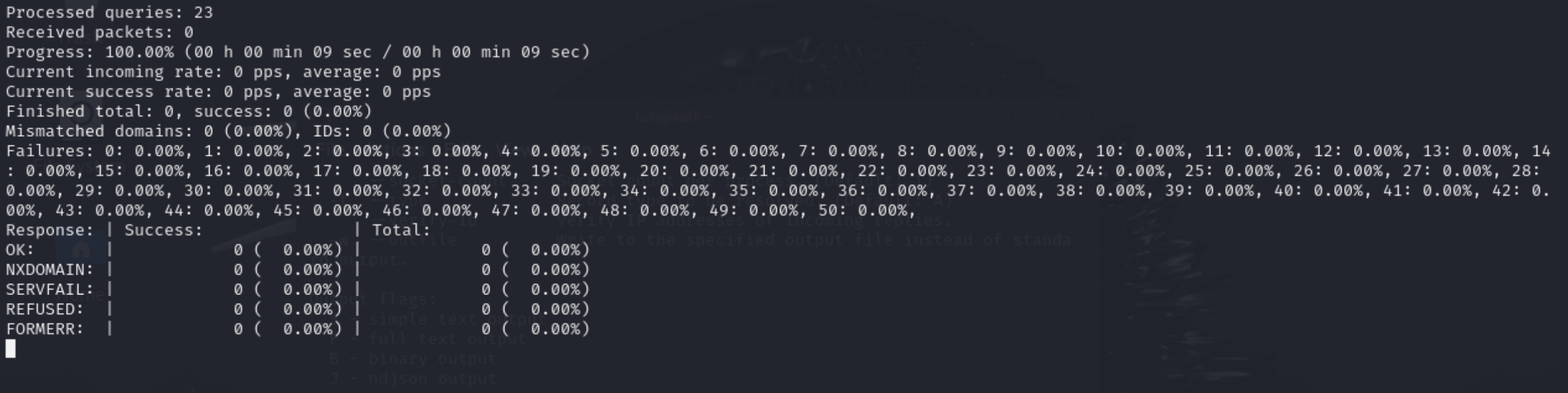
apt install whois -y && whois hackeru.com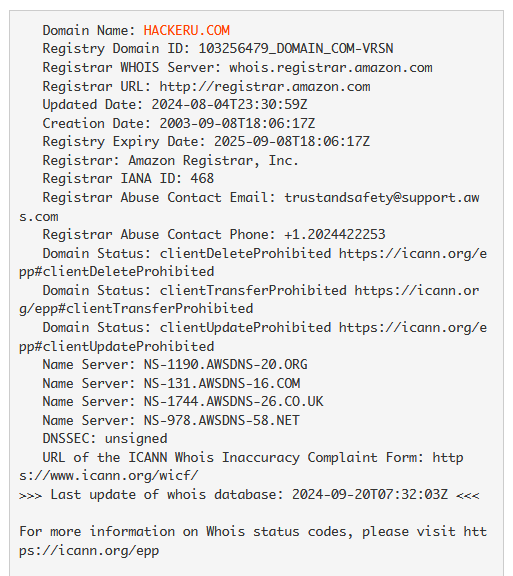
Immediately we see the necessary artefacts worth highlighting - a few NS records. Unfortunately, there is more information about the registrar than about the registrant. Let's perform a classic query to the DNS server and resolve the domain record hackeru.com:
dig hackeru.com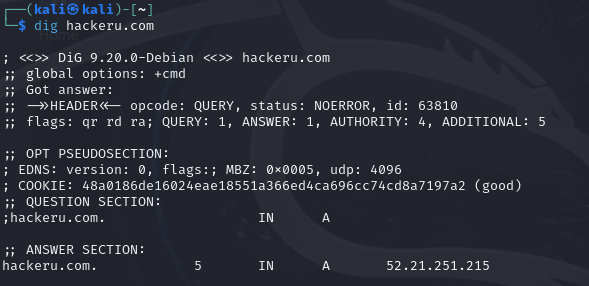
The server has a type A record that hackeru.com resolves to 52.21.251.215. It often happens that one organisation may have several white addresses in the same grid. Let's request PTR records of all addresses in the 52.21.251.0/24 grid. The expected result will be resolved subdomains or similar records that belong to the DNS server.
#!/bin/bash
for i in {1..254}; do
dig @NS-1744.AWSDNS-26.CO.UK -x 51.21.251.$i +short
done
Let's try to make a record transfer request to the DNS server, this is a fairly popular configuration issue that allows you to offload all server records:
dig axfr @NS-1744.AWSDNS-26.CO.UK hackeru.com 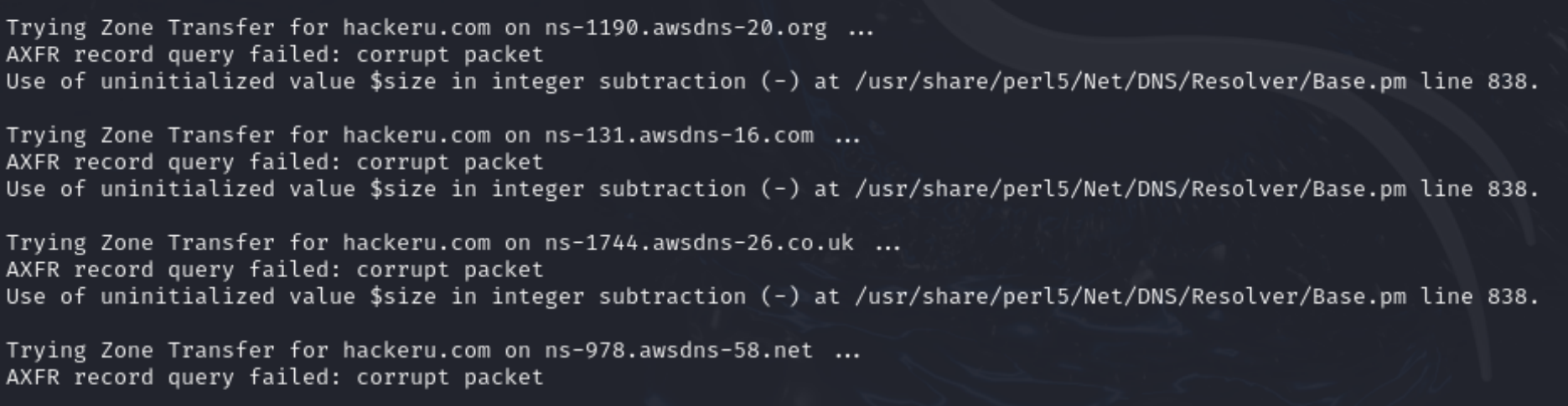
The server is configured correctly so it was not possible to query records directly, however, for some servers this is available and usually looks like this:
dig axfr @nsztm1.digi.ninja zonetransfer.me 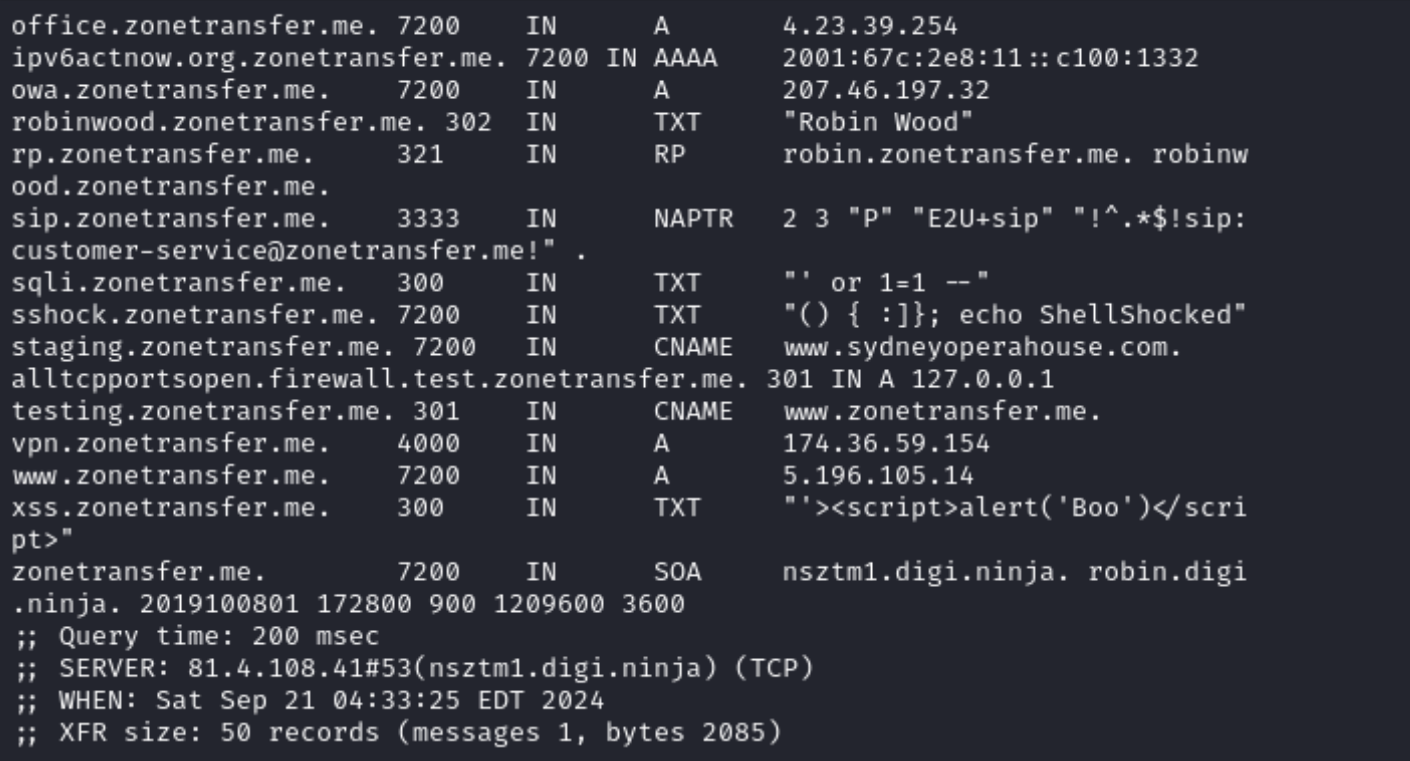
This allows you to learn sensitive information about the domain owner, as well as stored records, which can be excellent entry points for infringers.
However, one of the most effective ways is to search for a subdomain from open sources and bruteforce. There are a number of utilities that can be used to do this:
- subfinder - a utility to search open source Shodan, Censys and search engines;
- assetfinder - a utility, also for searching through open data, but using the crt.sh database. This is where all information about domains,
- certificates and their public keys is stored;
- altdns - a utility for bruteforce, which allows you to search for alternative records by adding different characters to the list of existing ones;
- massdns - a utility for fast resolving;
- gau - URL aggregator via search engines.
For efficient work, we will combine the result of each solution into one file and exclude duplicates, after which we will resolve and collect the list of public IP addresses. Let's collect data from the engines:
subfinder -nW -oI -o ~/subfinder.log -d hackeru.com && \
assetfinder -- subs-only hackeru.com > ~/assetfinder && \
cat ~/subfinder. log ~/assetfinder | cut -f1 -d , | sort -u > unique-subdomain.txt 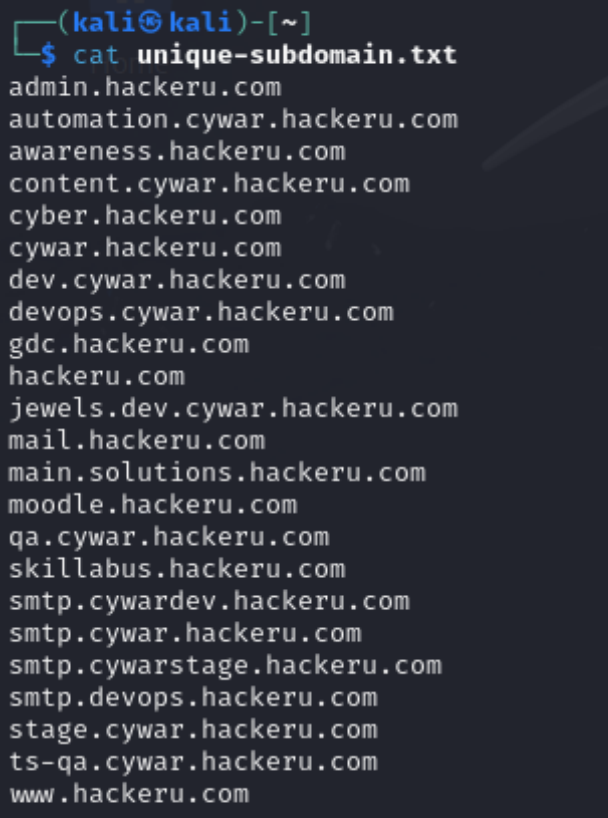
We got a list of 23 unique subdomains, which can be resolved and the corresponding addresses can be found. But perhaps there is not enough information about new domains in public sources or they do not have services that require SSL. For this we will use altdns and massdns.
The utility requires a dictionary to be used for enumeration:
altdns -i unique-subdomain.txt -o out.txt -w words.txt -r -s new_unique.txtWhere -i is the domain source, -o is the mutation output file, -w is the mutation dictionary, -r will allow all records to be resolved, and -s will record mutations that have been resolved.
You can then put all the domain names into a single file and massdns will do the resolving:
massdns -r ~/res ~/unique-subdomain.txtThe set of IP addresses is a list that can be used in penetration testing.
massdns -r res.txt -t A -o S -w fin.txt subdomain_file.txt