In the era of virtualisation of processes and resources, the issue of security of executable environments is quite acute. Pre-prepared images may contain virus and various exploits that can damage both the system locally and the infrastructure globally.
They are distributed through such platforms as Docker Hub, GitHub, which allow you to install software that is not checked for various kinds of software bookmarks and the very same VPO. How to check if a container is safe to use?
Scanning and analysing layers in Dockerfile
Let us remind you that the container itself is just an isolated environment where the base OS image is rolled out and a Dockerfile is executed on top of it, which can be rather malicious. Let's take for example a pre-infected container filled with miners and other VPO. Let's download it to our machine with Docker pre-installed:
sudo docker pull quay.io/petr_ruzicka/malware-cryptominer-container:1.4.0
Note that we only downloaded the image to our local repository, but did not run it on the OS! You don't need to do that, the file itself will be sufficient for analysis! If you don't have Docker pre-installed, do it with the following command:
sudo apt install docker.io docker-compose -y After that, we need to understand what exactly we want to investigate and where we are going to detect malicious activity. An image is a collection of a minimally basic OS, the Dockerfile executed on it, and the metadata that is used when deploying it. So let's pay attention to it, first we need to understand what actions are performed in the image, for this we will use the dive inspection utility. To install deb we will run the command:
DIVE_VERSION=$(curl -sL "https://api.github.com/repos/wagoodman/dive/releases/latest" | grep '"tag_name":' | sed -E 's/.*"v([^"]+)".*/\1/')
curl -OL https://github.com/wagoodman/dive/releases/download/v${DIVE_VERSION}/dive_${DIVE_VERSION}_linux_amd64.deb
sudo apt install ./dive_${DIVE_VERSION}_linux_amd64.deb It will allow you to find the latest version of the software in the repository, as well as put it in the download paths to then install it.
After successful installation of the package we can write a command where we specify dive to start the inspection software and specify the name of the image:
sudo dive quay.io/petr_ruzicka/malware-cryptominer-container:1.4.0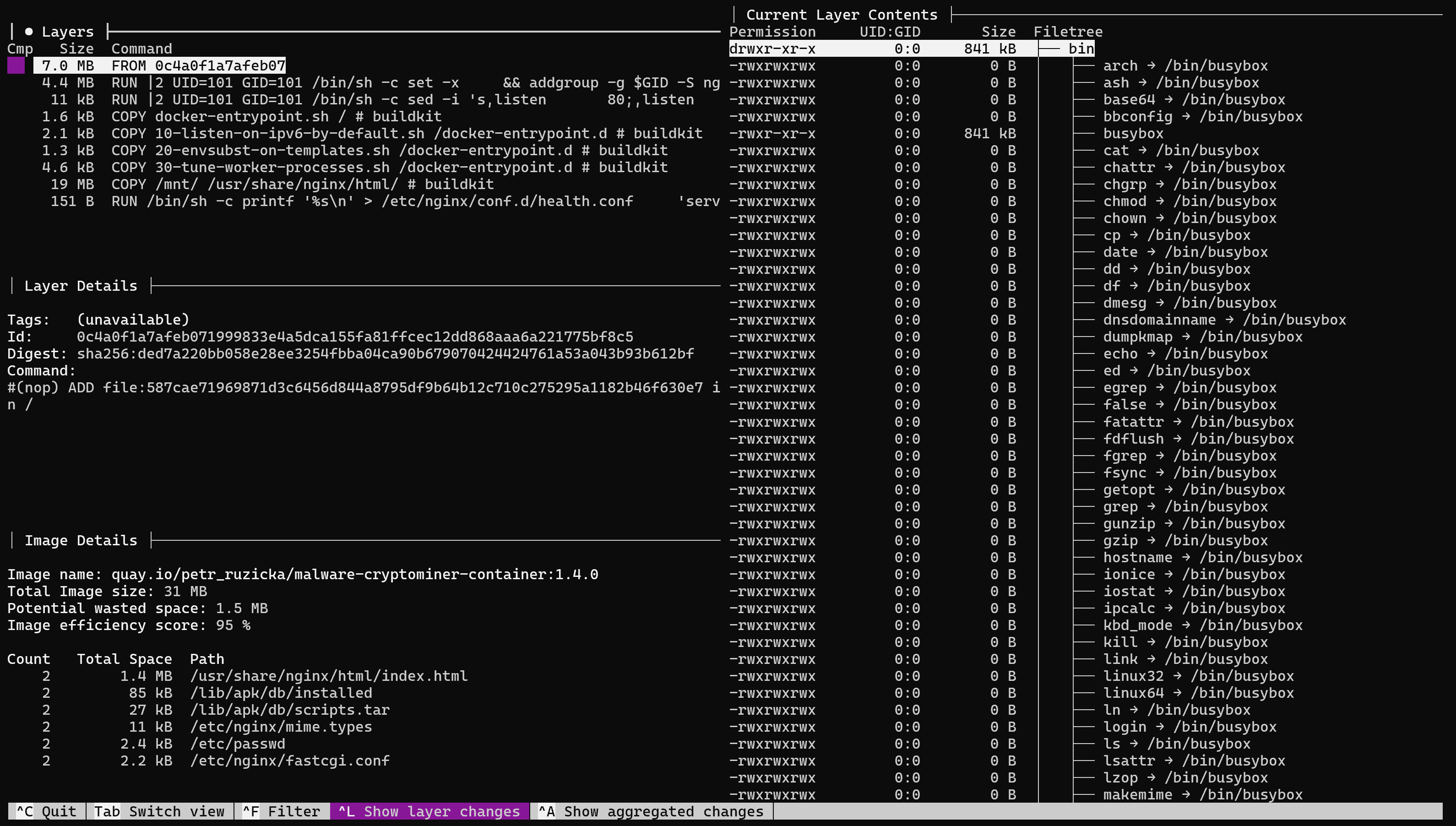
The control panel has four main fields, where Layers is the Docker File, or rather its layers. Below are the details of each layer and the meta information about the image, where you can already see that you have interacted with the web directories. Let's parse each layer and try to find something illegitimate:
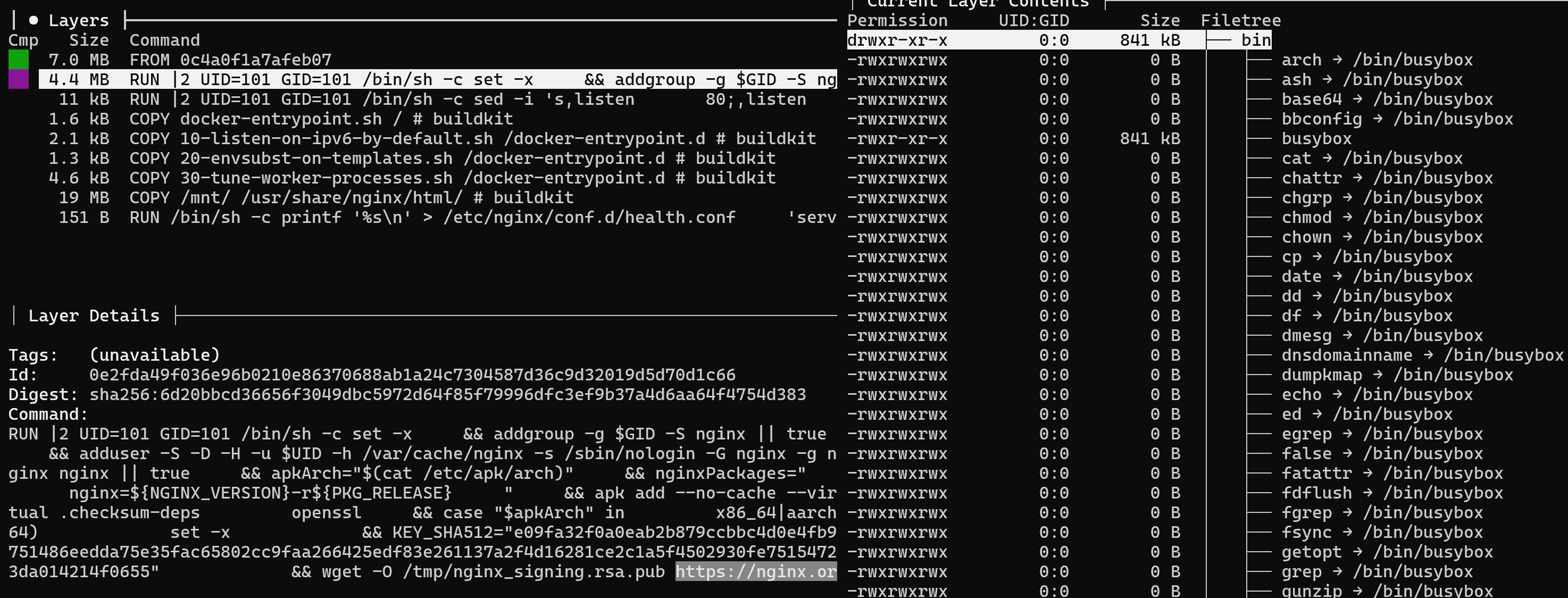
In this case we can see that the installation is performed from the suspicious domain nginx[.]so, then use TAB to switch to the file system on the right and see the changes made by Dockerfile. Additionally, filter the changes with the Ctrl+A key combination and we will see a cluster of previously copied files with suspicious names:
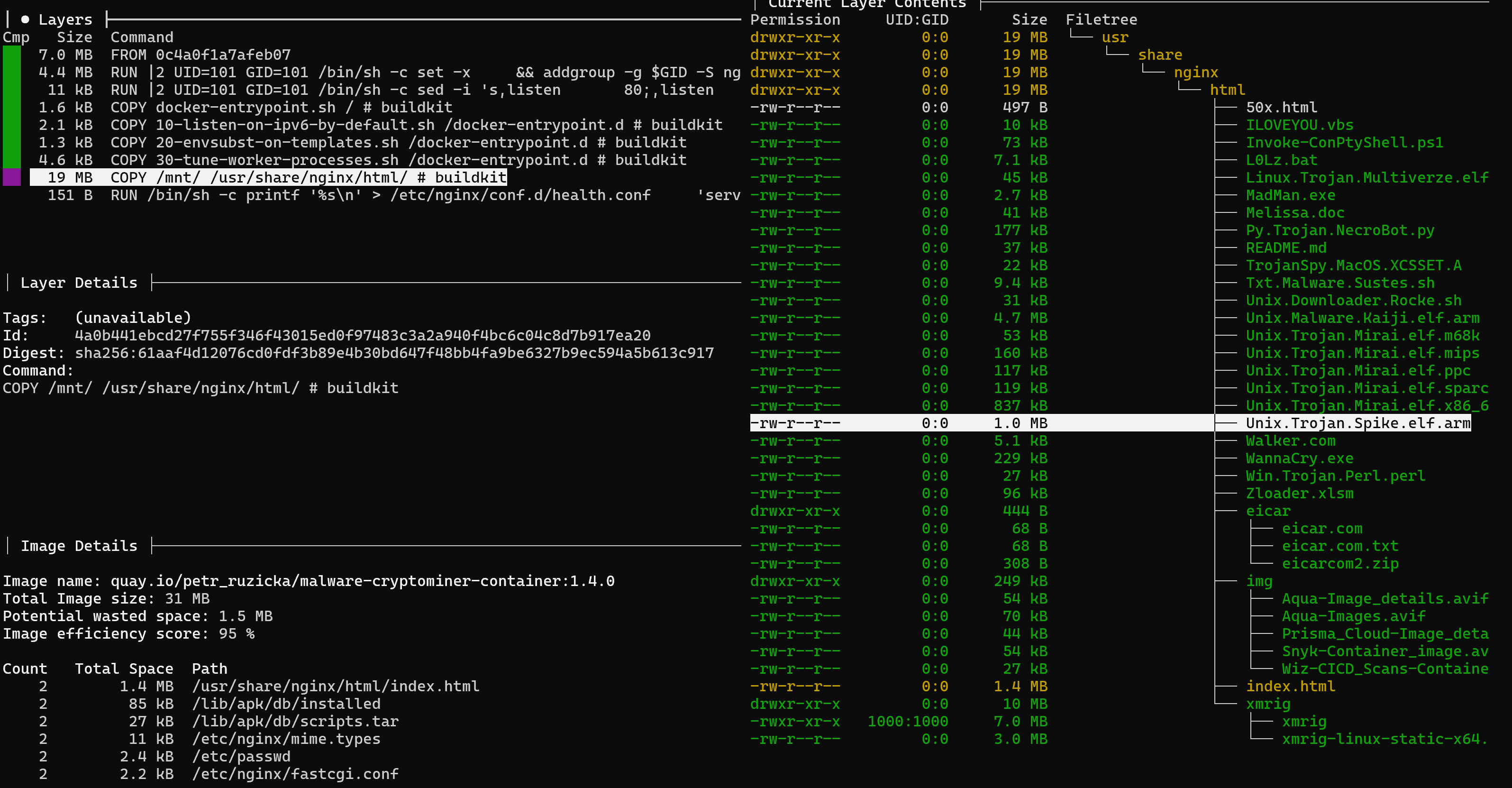
In a real attack, the files may be named quite innocuously, so you need to pay attention to the directories and the format of the files that are added to the container. Since the files look suspicious, you need to make sure they are virus. Let's exit the inspector panel and create a file system container without launching it:
sudo docker create -- name temp_container quay. io/petr_ruzicka/malware-cryptominer-container :1.4.0 && \
sudo docker export temp_container -o filesystem.tar && \
sudo docker rm temp_container && \
ls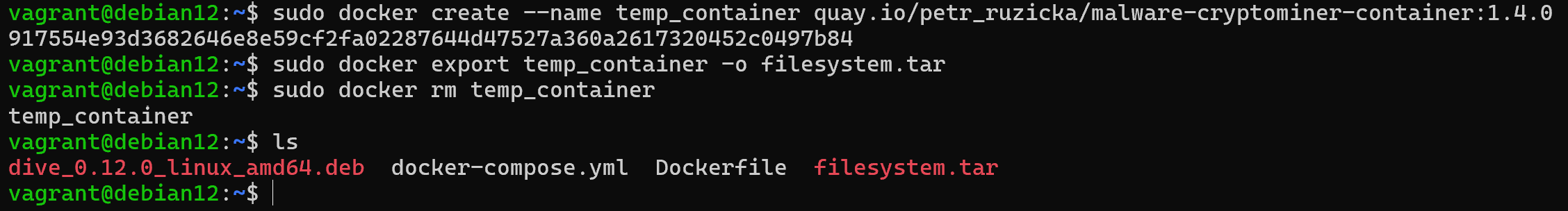
Now we have a container file system with already applied Dockerfile in our home directory! It remains to unpack it and check all files for VPO, for this purpose we will write a command, having previously created a new folder and navigating to it:
sudo tar -xf ~/filesystem.tar 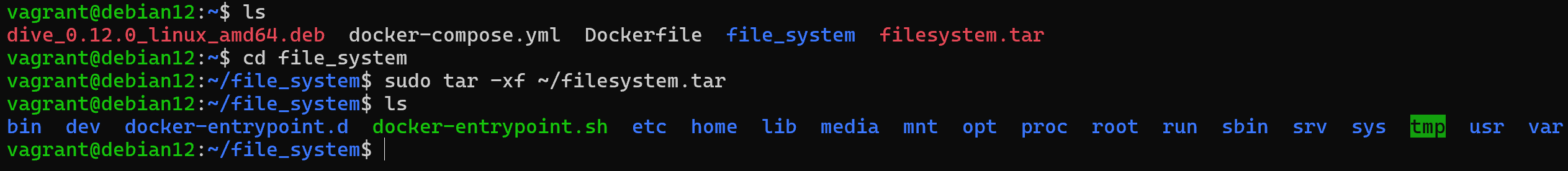
Remember that the malware has potentially affected several directories, so we will scan them with ClamAV antivirus, and then we will see the result, where virus are detected!
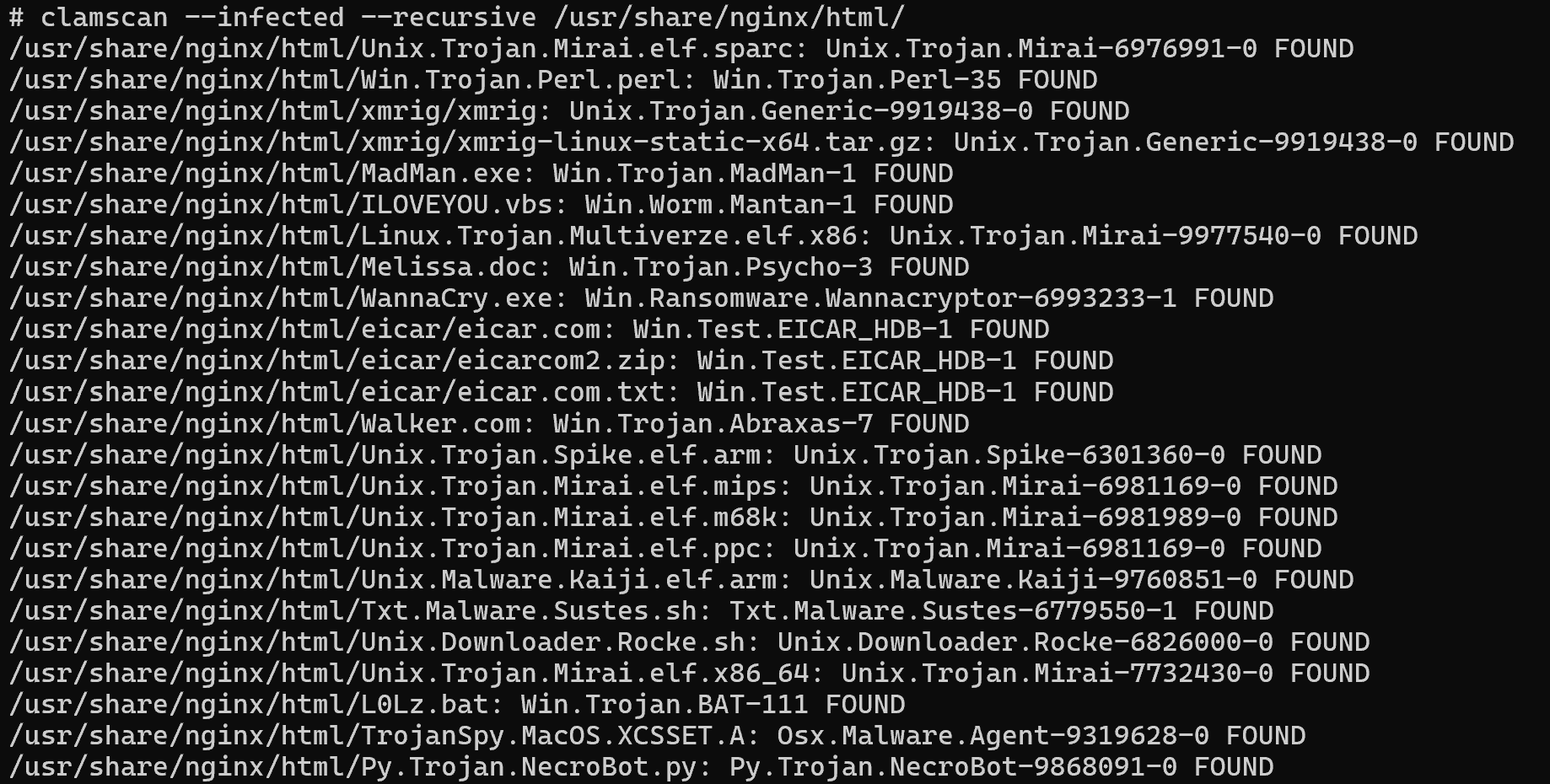
With the inspection tool it is possible to perform such manual analyses at a deeper level and already use Yara rules engines in addition, which will allow to detect other types and variants of VPO. This solution is not a replacement for automated tools, but just a way to manually look at the package details inside, based on manual/static analyses.
If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

Conclusion
Securing Docker images before deployment is essential to protect both local systems and broader infrastructure. By analyzing image layers, inspecting Dockerfiles, and checking metadata, administrators can identify malicious actions or suspicious files. Tools like Dive allow for detailed layer-by-layer inspection, while extracting the container filesystem and scanning with antivirus solutions such as ClamAV helps detect malware and potentially unwanted software. Regularly auditing container images ensures safer deployments and reduces the risk of infecting your infrastructure with pre-packaged threats.
FAQ
- Q1: Why should I scan Docker images before running them?
A: Pre-built images can contain malware, cryptominers, or vulnerabilities. Scanning ensures the image is safe and prevents compromising your system or network. - Q2: Can I run a Docker container without risking infection for analysis?
A: Yes, you can download or create the container without starting it. Tools like Dive allow you to inspect layers and files safely before running the container. - Q3: What tools are recommended for Docker image analysis?
A: Dive is a popular tool for inspecting image layers and metadata. For deeper malware detection, you can export the filesystem and scan with antivirus software like ClamAV, or use Yara rules. - Q4: Is manual inspection enough to secure images?
A: Manual inspection helps understand the image contents, but it should be combined with automated vulnerability scanning and antivirus checks for comprehensive security. - Q5: Can this process be used on all Docker images?
A: Yes, any local Docker image can be inspected. Always use trusted sources and regularly audit images before deployment in production environments.



