When securing an organisation's information system, it is necessary to pay equal attention to all parts and subsystems. In this tutorial we will touch upon the topic of the functional part of the IS, which is responsible for supporting the functioning of the network infrastructure, services and subsystems, and more precisely we will take a small piece of it - the hardware part.
The first step to protect any computing device or group is a basic security configuration or hardening. Depending on the type of software being used, there are different ways to attack the hardware, and vendors are innovating, making the security testing of the devices being used an increasingly complex process. However, there are basic principles that determine the security level of a system. Abstract Machine Test Utility exists to automate this kind of testing!
What is the process of testing a PC?
Amtu is an administrative utility that tests basic measures of security mechanisms at the hardware level. The testing process includes working with RAM, persistent memory for information corruption, storage. Integrity and confidentiality of data transfer through network interfaces, as well as execution of privileged instructions in supervisor mode.
Please note! This utility is mostly found in Red Hat or RedOS repositories, you can find suitable repositories or utilities in alternative sources! To install the testing software tool, you need root or a user with sudo privileges to install it. Let's update the indexes and install new dependencies:
dnf update && dnf upgrade -y 
If you don't have a server or you want a separate environment where you can test the utility. You can use the example of Serverspace cloud server to build your own server on either of the two platforms vStack cloud or VMware cloud. Click on the Create Server button and choose a configuration that suits our needs, then click Order.
After some time the servers will be available via any of the main connection methods, for the current tasks RedOS with a data centre in Istanbul has been chosen.
Installation and use
To install it, we will write the command:
dnf install amtu -y 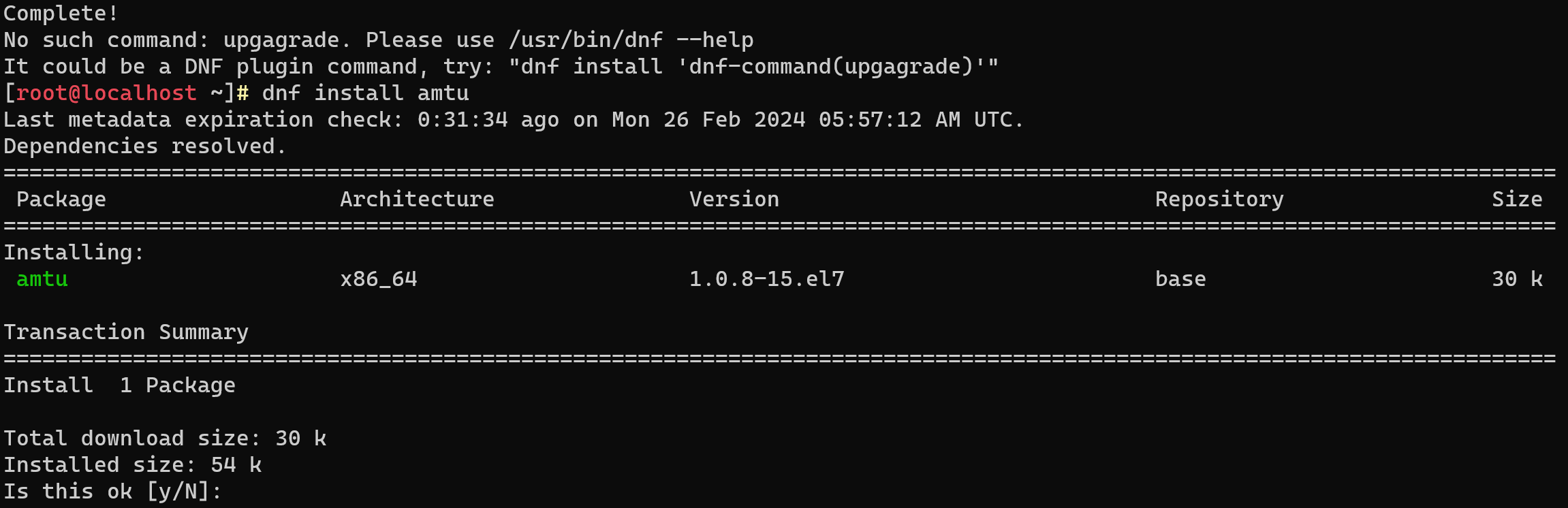
Let's familiarise ourselves with the utility's capabilities by calling its -h option:
amtu -h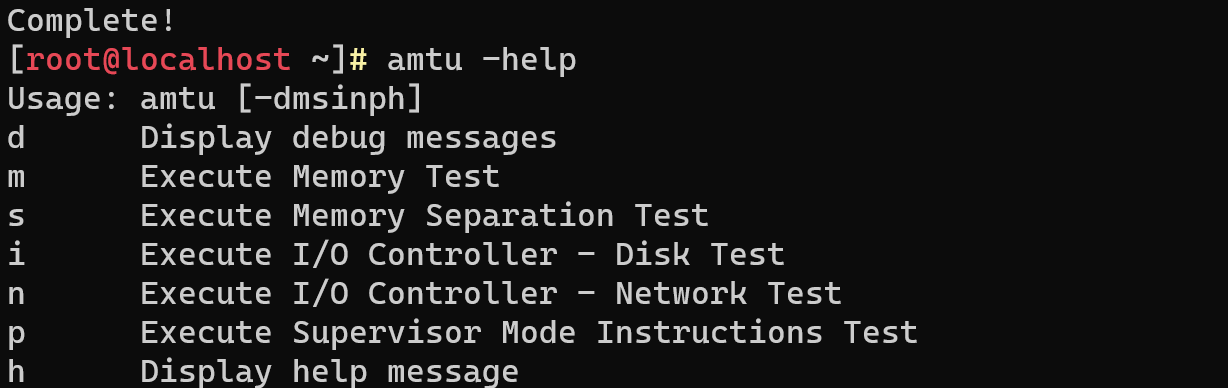
Let's describe each of the presented options:
- -d - displays debug messages.
- -m - writes and reads data in memory to check compliance.
- -s - prevents user programs from accessing memory occupied by video memory and the OS kernel.
- -i - verifies that data on discs remains unchanged for IDE and SCI controllers associated with file systems. Tests disc controllers without checking if file systems are read-only.
- -n - Verifies that the transmitted and received data of each network device match. The check applies only to Ethernet and Token Ring devices, not affecting asynchronous devices.
- -p - verifies that the use of privileged supervisor instructions remains valid. The instruction set used depends on the architecture ( -h - help).
All of these commands are designed to verify that the data and operation of the equipment match. They may be useful when testing or diagnosing problems with the equipment. For detailed information about each command, please refer to the documentation or reference information.
Let's test the operation of privileged instructions with full event output;
amtu -dp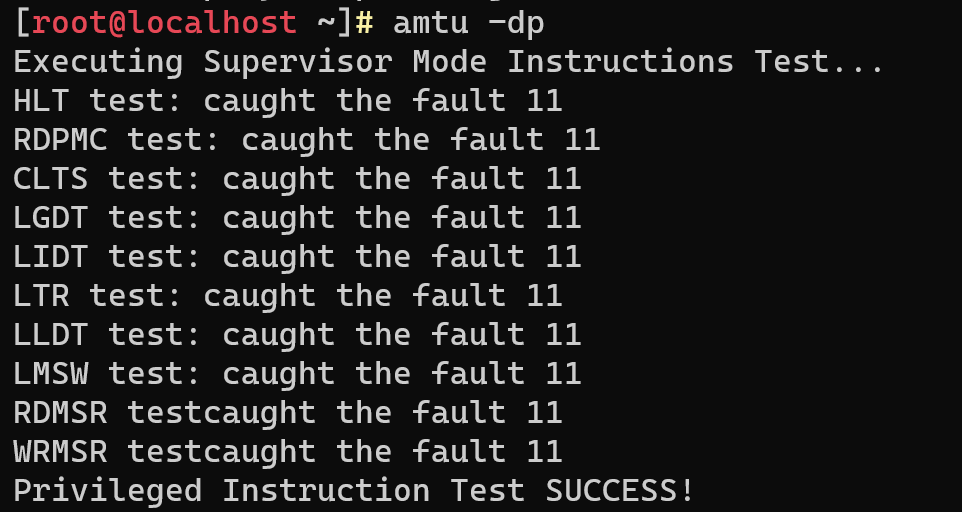
Access was not obtained, this is evidenced by the errors caught and at the end of the test we see the result SUCCESS, which means that the test was successful. Also the result can be a numerical designation, with 0 successful execution and slow execution with -1 output.



