The size of company infrastructures grows hyperbolically with the increase in projects, services and services provided, which means that the issue of monitoring their performance/security is becoming more and more acute. After all, it is necessary to collect the required telemetry in time to respond to incidents among multiple nodes.
Windows has its own logging subsystem, which provides normalised events about what happened, understanding of its work, allows you to automate the collection process, expand/narrow the pool of collected events. In this article we will consider the basic concepts of the subsystem's operation and its settings!
What is Eventlog?
Eventlog is an operating system event logging subsystem that allows for trabshooting, incident investigation, activity monitoring, and more. By default, the device has a certain list of collected events, which can be viewed through Event Viewer - a snap-in for working with logs.
Win + R → eventvwr 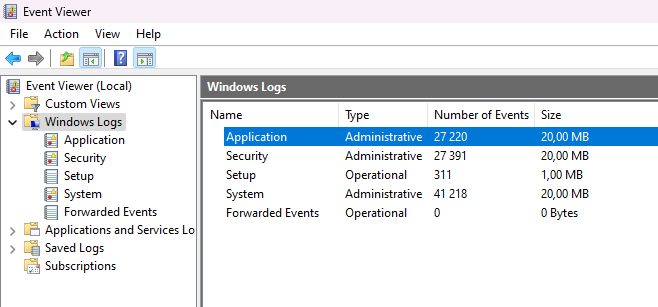
All logs are divided into two global groups Windows Logs and App/Services Logs, where the former are generated by the OS kernel and its modules and then normalised into events with numbers. And the latter are generated by applications and have their own IDs, but add context to the machine's operation. Internally, they are also broken down by functions that log their subsystems!
You can find them in log format under the path C:\Windows\System32\winevt\Logs.
How to configure event collection?
To increase or reduce the set of collected events from the device, you need to go to the policies, for a local PC - these are local policies, for a domain PC, respectively, policies on the domain controller. In fact, the key difference is only in the scope of audit and destination policies, some will be suitable for an APM, some only for a domain controller, etc.
Let's move on to local policies, here the audit settings are divided into regular and advanced:
secpol.msc 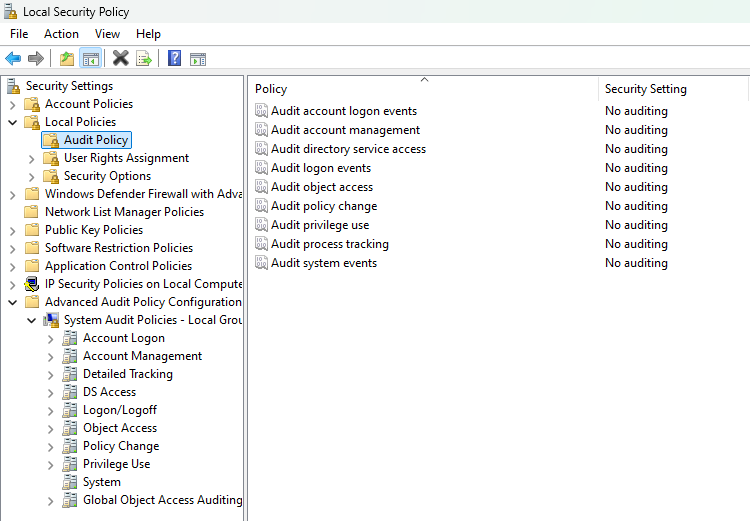
Among all those listed, we can highlight the top events that are important to log for security subsystems at the moment:
- 4663(S): An attempt was made to access an object;
- 4656(S, F): A handle to an object was requested;
- 4720(S): A user account was created;
- 4731(S): A security-enabled local group was created.
- 4732(S): A member was added to a security-enabled local group.
- 4733(S): A member was removed from a security-enabled local group.
When configuring the event policy, you can set key metrics that you want to track:
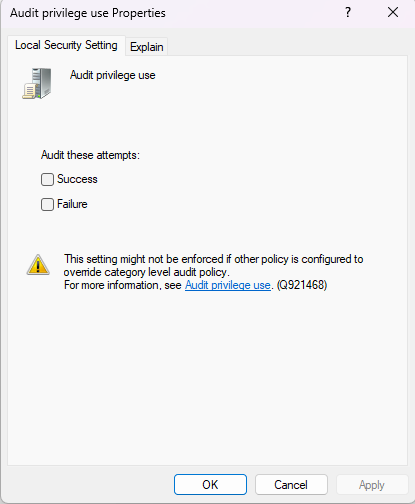
For example, only failed promotion attempts that are more likely to have a lower false positive rate. Once the policies are scheduled it is necessary to apply them:
gpupdate /force 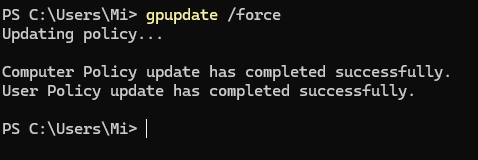
After that, new events will be logged already in the log, after the settings are enforced! For domains, you need to specify the scope or area that you want the group policy to be applied.
Audit data enrichment
You may notice that not all data collected from applications, kernels in Event Log format is complete. This is because the kernel performs many other tasks and full logging would lead to system degradation and performance degradation. Therefore, the ETW or Event Tracing for Windows mechanism is implemented, which uses ring buffers to store data and logs many times more information.
Usually, its logs are stored in the path: C:Windows\System32\WDI. To view them you need to convert the .etl format to .xml.
tracerpt -lr ‘C:\Windows\System32\WDI\LogFiles\NAME.etl’ 
After that the search and work can be done through a text editor or you can load the original format into Event Viewer.
These OS protection mechanisms allow you to expand the ability to monitor, respond to events and incidents occurring in information systems. If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

It will take some time to deploy the server capacity. After that you can connect in any of the convenient ways. This infrastructure service is an integral part of the corporate network and security subsystem, allowing to implement authorisation, content filtering, as well as being a gateway for users to control visited resources.



