Just recently, the developers of the Kali Linux distribution have released a new release with version 2024.4, which has a lot of innovations. Find the distro already available on the official website in different formats, both online and offline versions.
Kali 2024.4 Deployment and Upgrade
Select the appropriate processor architecture for your device, usually on Linux similar systems it can be viewed via the command:
uname -aIn Windows this is realized by a similar solution, where we are interested in the CsSystemType line:
Get-ComputerInfo 
After that, the selected distribution must be downloaded and burned on the installation media via dd or rufus, and then run from it via BIOS.
In our materials you can also find details about installing Kali Linux from the installation media!
But you can go the easier way, for your test environment or network loop you can deploy VPS on Serverspace in the cloud. To do this, let's go to the control panel. In the left menu select vStack or VMware platform → Create Server → Select Distribution → Rest of VPS Settings.
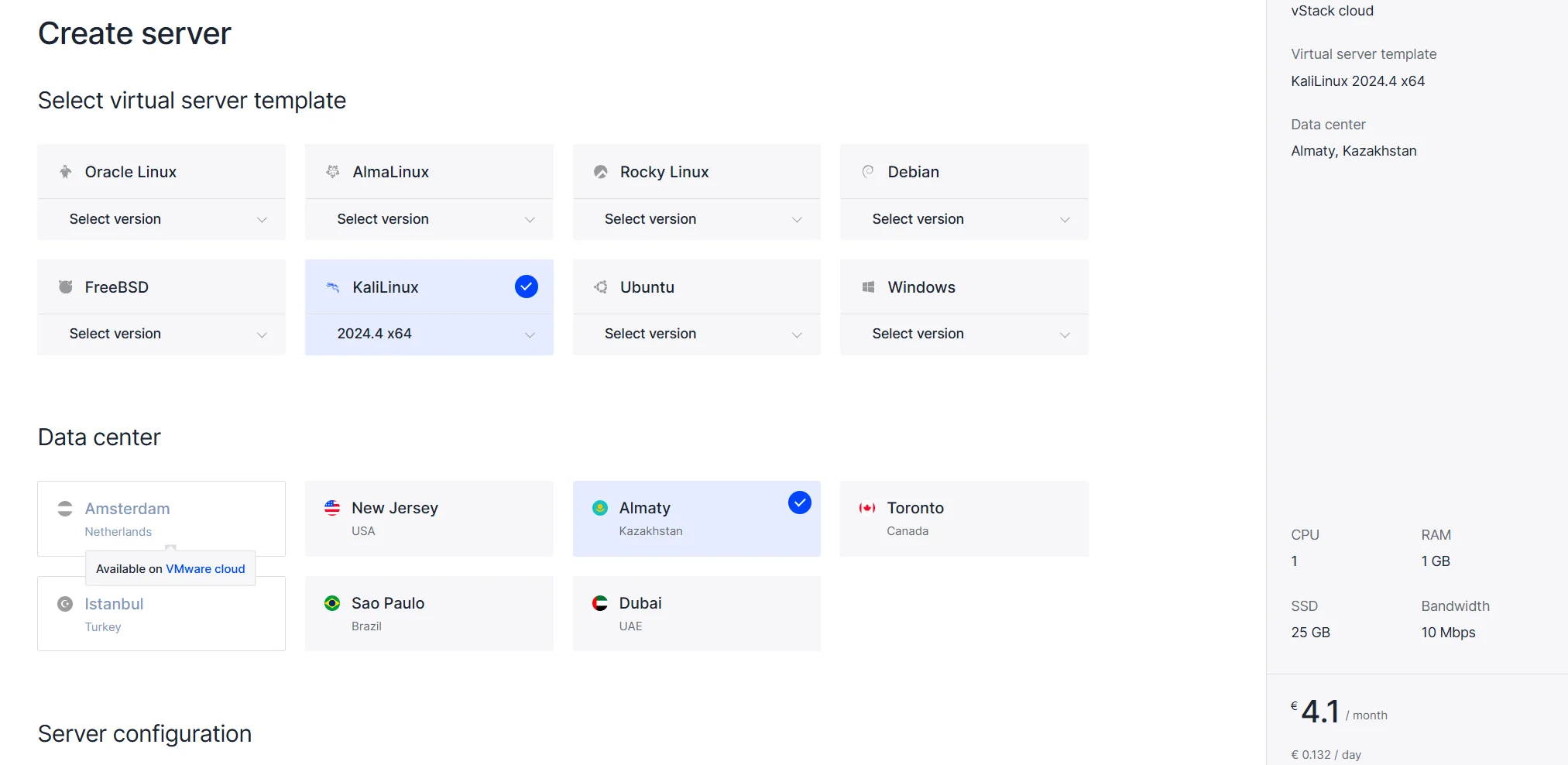
After that, within a minute, the server will be deployed and ready to use!
If you are already using Kali on your resources and want to upgrade, then follow some commands to download the available packages and upgrade the system:
echo “deb http://http.kali.org/kali kali-rolling main contrib non-free non-free-firmware”
sudo tee /etc/apt/sources.list
sudo apt update && sudo apt -y full-upgrade
cp -vrbi /etc/skel/. ~/
[ -f /var/run/reboot-required ] && sudo reboot -f Let's run through the major changes in the OS!
History of changes in the new version:
- Old 32-bit systems are becoming an atavism of modern solutions, so following Debian/Ubuntu, Kali developers are dropping support for i368 architecture for their distributions, but leaving packages in repositories;
- Updated the Linux kernel to version 6.11;
- A known vulnerability issue with the DSA cryptographic algorithms used to generate keys was fixed by installing OpenSSH (9.8p1), the default. OpenSSH (7.5) with the command name ssh1 was left in place to support legacy systems. Take these changes into account in your automated solutions!
- The default version of Python is now 3.12, which means that the user is currently unable to install software via pip, even with a pre-created virtual space. You must now use pipx to work, as it will automate the process of creating virtualenv.
- There are new tools to perform security auditing of servers and endpoints.
Checked for malicious activity in this release and published them in their repositories:
- Mssqlpwner - interact with and gain control over MSSQL servers.
- Sara - RouterOS security inspector (provided by casterbyte).
- Hexwalk - hexadecimal data analyzer, editor and viewer.
- Web-cache-vulnerability-scanner - Go command-line tool for testing for web cache poisoning (provided by Arszilla).
- Chainsaw - rapid forensic search and analysis of Windows artifacts (provided by Arszilla).
- Openssh-ssh1 - Secure SHell (SSH) client for the legacy SSH1 protocol.
- Xsrfprobe - An advanced toolkit for auditing and exploiting Cross Site Request
- Forgery (CSRF/XSRF).
- Bloodyad - a tool for privilege escalation in Active Directory (provided by Arszilla).
- Python-pipx - execute binary files from Python packages in isolated environments.
- Certi - allows you to request certificates from ADCS and discover patterns (provided by Arszilla).
- Findomain - fast and comprehensive domain recognition solution (provided by Arszilla).
- Proximoth - a tool for detecting vulnerabilities related to control frame attacks (provided by TechnicalUserX).
- Linkedin2username - creating lists of company usernames on LinkedIn.
- Zenmap - GUI for Network Mapper (nmap) (no longer required!).
This summary covers the major changes in the new release that could significantly affect your work with this distribution!



