It is hard to imagine a secure infrastructure without AAA solutions that enable basic processes such as identification, authentication and authorisation of subjects. In most cases, in-built operating system technologies called domains are used. They are a logical group of devices, accounts and objects that are under the control of management servers. They logically perform the same function of accounting, authentication and authorisation.
However, unlike classic AAA solutions, which operate at the network level, data interacts at the transport level and above. This approach allows you to control the actions and configuration of the user's device. For this purpose, domains use the mechanism of group policies or GPO!
What is a GPO?
GPOs or Group Policy Objects are objects in AD that consist of a set of device and user rules that apply to areas such as domains, sites, and organisational units. In other words, policies that define the rules for how different areas of AD work. Classically, we have a tree of realms that have a nested structure. This means that if we apply a policy to a domain, then all devices and accounts that are nested will have to obey it.
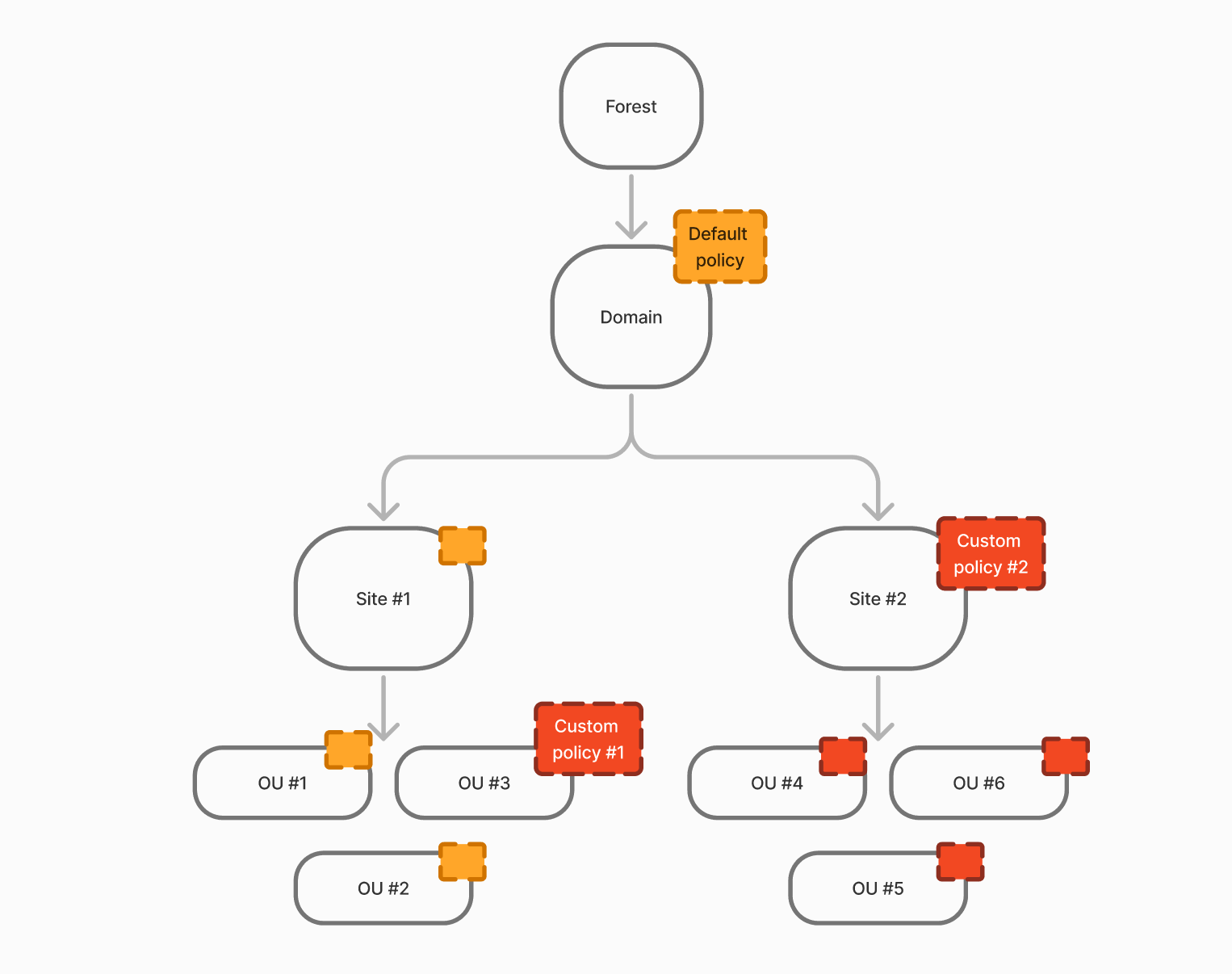 Screenshot №1 — Schema of work
Screenshot №1 — Schema of work
However, if it is necessary to move away from domain-wide rules, to a specific unit of machines/users or to a site, then a new policy can be applied which will overwrite the old policy. This creates the policy logic that the closer the new policy is to the object, the higher the priority.
At least basic configuration for domain objects and sub-objects is important! One of them is the password policy, which allows you to set the rules for user authentication on the device. To do this, let's go to the machine and do a quick configuration!
Configuring GPOs in AD
If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

First, open a search with the Win command key, type group policy and open the policy module. Or you can use Win+R to enter the command:
gpedit.msc
When we open the snap-in, a menu will open in front of us, with the very attachments on the left that we looked at in the diagram. In this context, orb.lol is a domain, and the Default Domain Policy applies to all of its members and entities below.
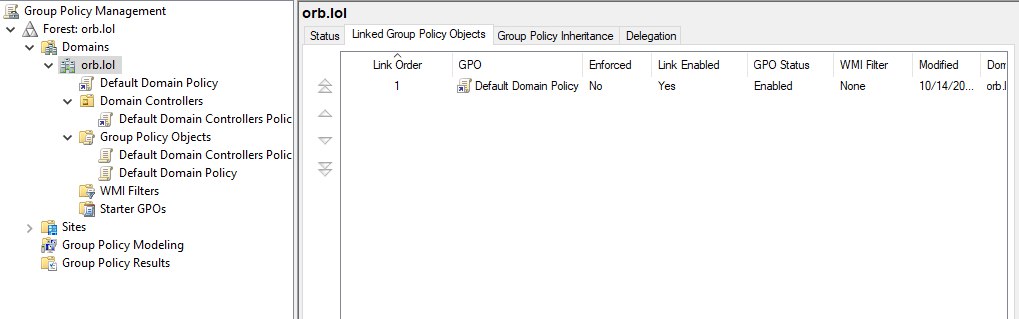
Note that the Domain Controllers organisational unit has its own policy, which will overwrite those items defined in it. Those that are not explicitly specified will be inherited from the default domain policy. This is because the domain controller may have its own custom settings that may be different from the rest of the objects in the system.
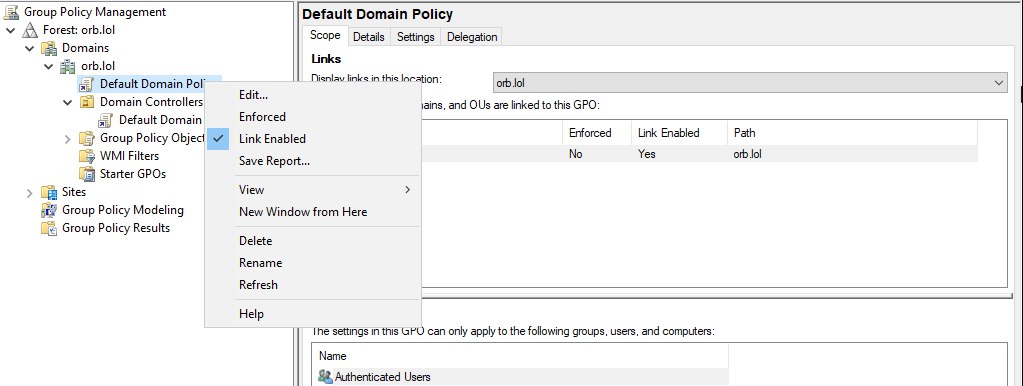
For example, let's configure a domain-wide password policy, go to Default Domain Policy and right-click it. From the context menu select Edit, by default, the rule set is already bound to the domain, so no additional action is required. However, if there is a need to do so, select the domain and associate it with the policy via the context menu. Back to the configuration, the policy is now open:
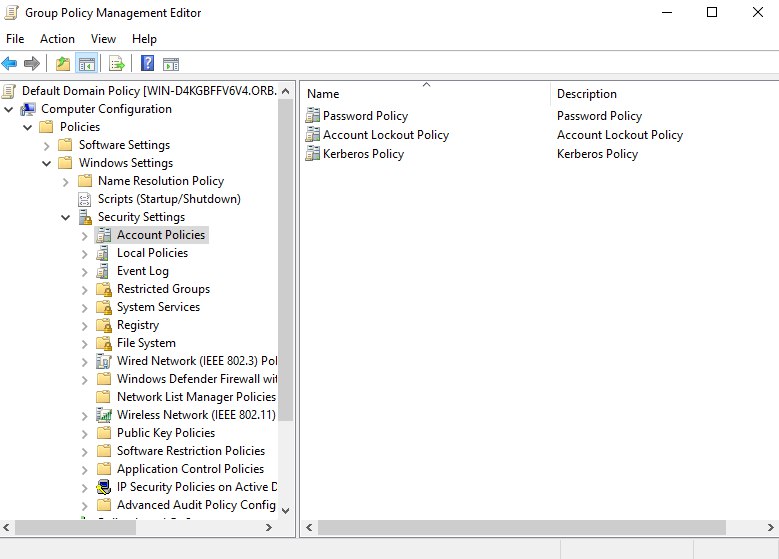
To get to the password settings you need to go through the objects in the following order: Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies. This setting will allow hardening of passwords on all PCs belonging to the domain. Let's select the first Password Policy and configure it:
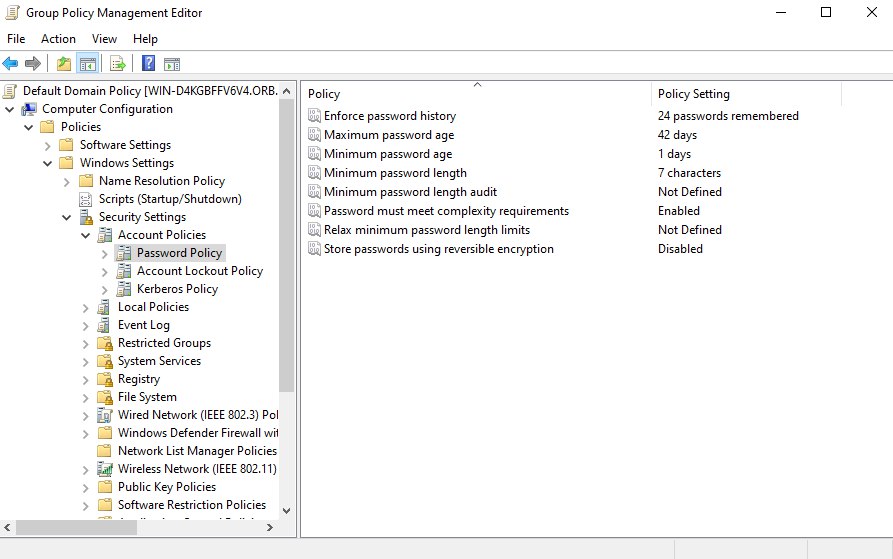
By default, not all settings fit the concept of secure usage. Just seven mandatory characters in a password has long been brute-force in small amounts of time. Change the length fields from 7 to 15 characters minimum, disable Relax Minimum password, this will disallow passwords less than 15 characters. And set the maximum password lifetime to 90 days. Go to the second tab Account Lockout Policy, which defines the conditions of account lockout in case of unsuccessful connections:
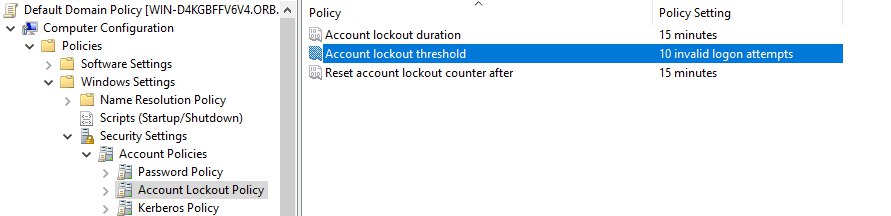
The first parameter is responsible for the blocking time, the second for the number of unsuccessful login attempts to block the account, and the third after how long the counter of unsuccessful attempts will be reset. Next you need to save all the applied policies and open the terminal via Win+X. After that you should write the command of forced policy update:
gpupdate /force This will allow you to apply policies immediately and not wait for devices to request updates from the controller domain! Fine, we have already configured our policy. For the next user log in, the old password will still work. However, for the new period of password change, they will need to use a more complex password.



