Chroot is a Unix command that can help you to change the apparent root directory of your file system. The advantages of this utility exceed all possible norms and indicators, such as running programs or utilities on a different version of the operating system without affecting the rest system.
Chroot
When you run chroot, you are making a fresh shell environment with its root directory, separate from the central system's root directory. This means that any commands or actions you take within the chroot environment will only affect files and directories within the chroot environment, not the primary system.
For example, if you wanted to test out a new version of a program that requires different libraries than what is installed on your main system, you could create a chroot environment with the necessary libraries and then run the program within that environment.
This way, you can ensure that the program will work properly without having to modify your main system.
It's important to note: chroot should only be used by experienced users, as it can potentially cause system instability if not used correctly.
Chroot: isolation and root permission
The main features of chroot are:
- Process isolation: chroot can run processes in an isolated file system namespace to prevent access to sensitive data and resources;
- Program testing: chroot can be used for testing programs in a safe environment where they cannot damage the host system;
- System recovery: chroot can be used for system recovery after a crash or malicious attack;
- Permission management: chroot can be used to restrict user access to specific files and directories on the server.
In that article, we will consider only process isolation and root permission, another function of this utility will be described in a new episode instruction.
At the beginning write this command to update the index of the package :
sudo apt update -y && sudo apt upgrade -y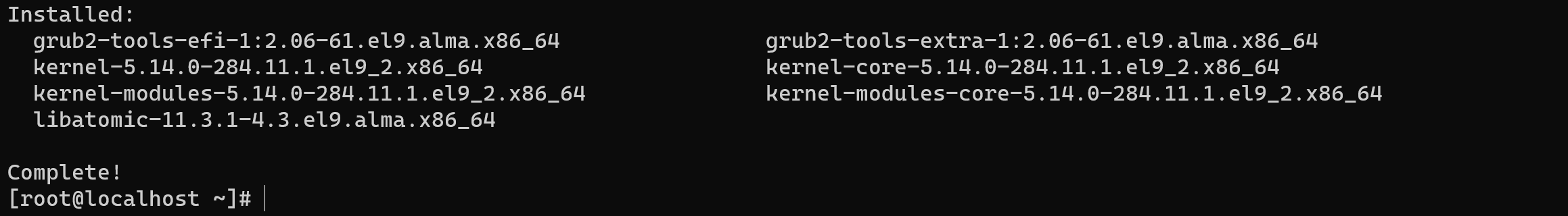
Check the installation chroot on your system via the command. For most Linux distributions, they are called "chroot" or "util-linux":
chroot --version || util-linux --version
After we have made sure that all files and packets have the right installation, make a directory where will new environment for our system:
cd / && mkdir env0
For example, we isolate utility process ls:
cp -R /bin /lib /lib64 /usr /etc /env0/chroot /env0 /bin/ls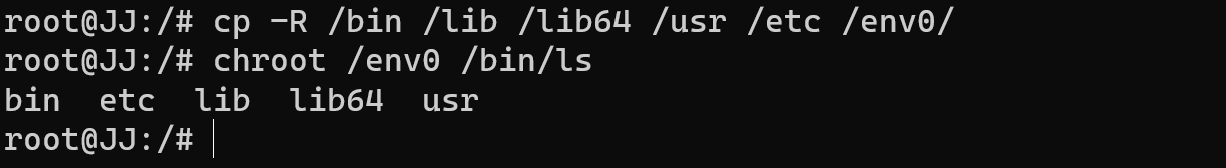
Via these commands, we copy and start the isolated environment, which in turn boot ls process. But how can we give or get access to this utility, all process is quite simple.
сhroot --userspec=<user:group> <directory>
Sets the user and group on whose behalf the command will be run in an isolated environment.
Conclusion
Overall, chroot is a powerful utility that offers a wide range of benefits, including process isolation, program testing, system recovery, and permission management. In this article, we have focused on process isolation and root permission management, but in the next episode of instructions, we will explore another function of this utility.
By following these steps, you can take advantage of chroot's capabilities to create safe environments for testing programs and recovering systems after crashes or malicious attacks. Stay tuned for our upcoming article on “Isolated recovery Linux via chroot”!



