There are many strategies and tactics used by IS specialists, which describe the principles and algorithms of asset protection. A key link in this scheme are also tools that allow to automate and speed up the work of the specialist. One of them is the Kali Linux distribution, an operating system with grouped sets of utilities that perform Mittre Attack techniques.
What is Kali Linux?
Kali Linux is a *nix family operating system based on the Linux kernel of the same name, containing infrastructure pentest software kits. However, although the OS has a reputation for being ‘hacker-ish’, the toolkits allow SOC, TI, Incident response personnel to investigate hacker infrastructure that is typically built to support attack chains and much more.
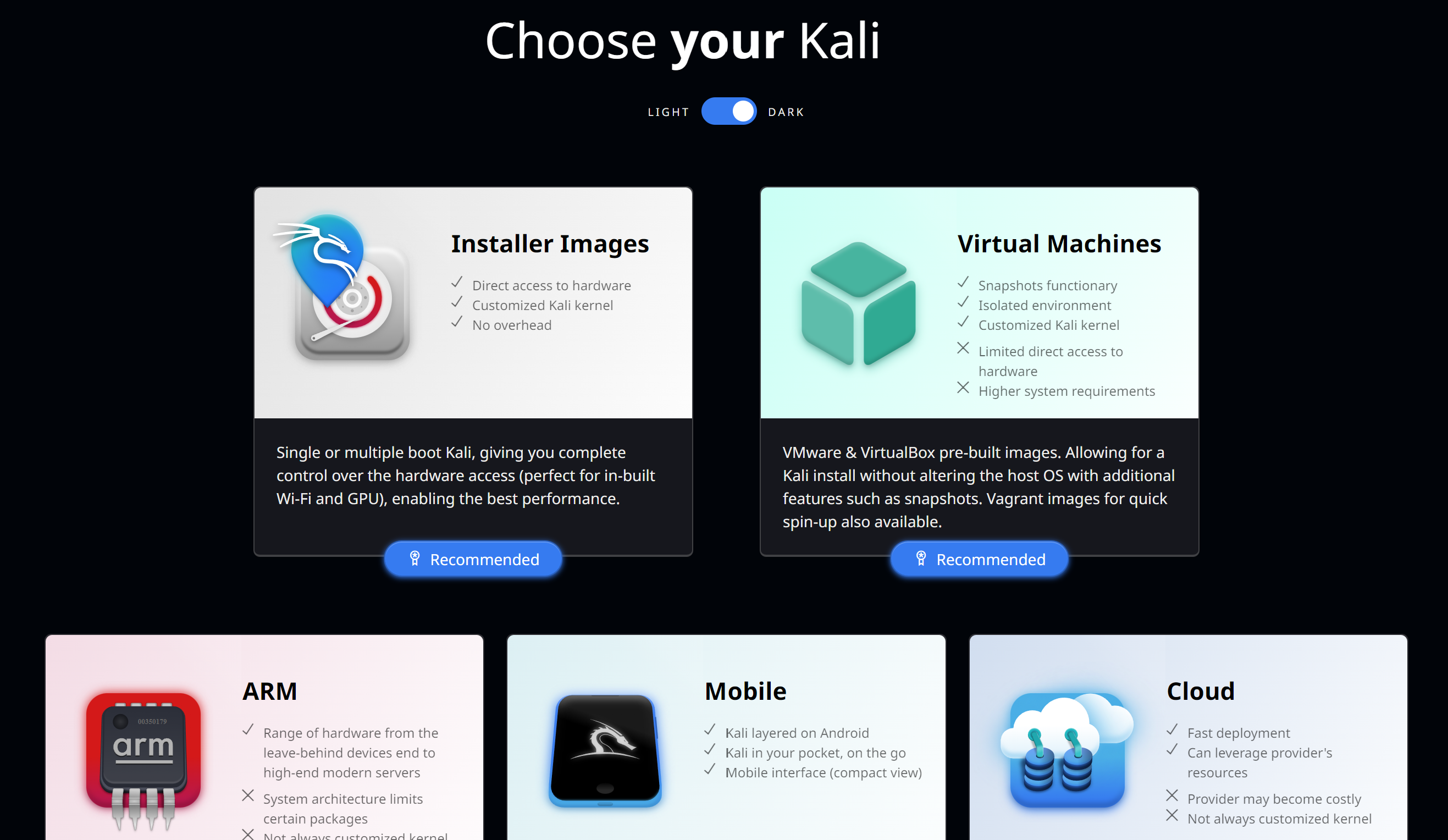
Let's start small and go to the official Kali Linux website, where we will choose the appropriate way to install the image.
Among the various installation methods we will choose the classic one via ISO-installer, which we can install on a USB stick and boot via BIOS, or use a virtual machine.
After all the preparatory steps, let's launch!
Installing Kali Linux
If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

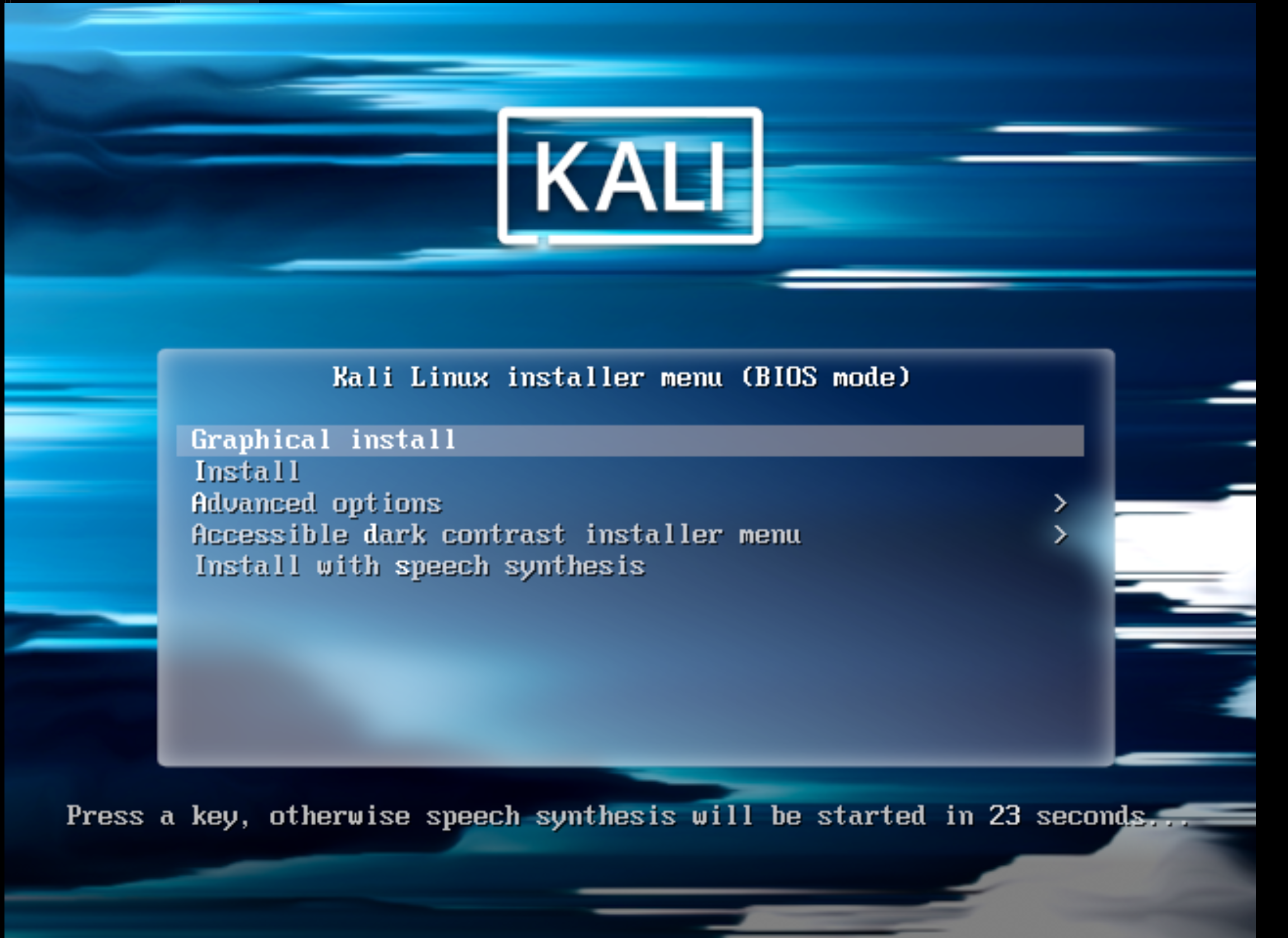
We are greeted by the bootloader window, where you can choose between graphical and CLI installation. If the first one is intuitive and easy to understand, the second option will be more interesting to consider, although it presents almost the same interface only pseudo. Let's run through the standard settings and choose the country and keyboard language layouts. The whole installation process will consist of basic menu blocks, each of which can be returned to during the installation process:
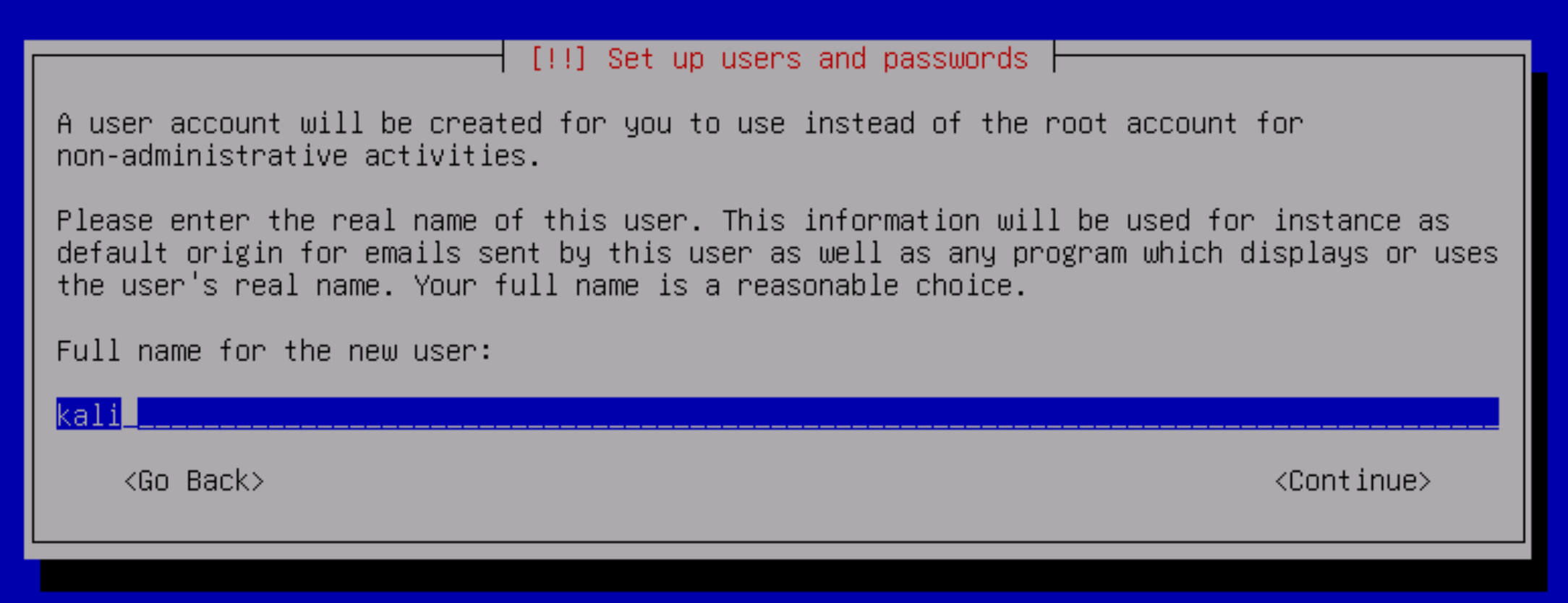
The first thing to be done from the configuration of the future OS is user configuration. Let's set a name, login and password to be remembered for authentication.
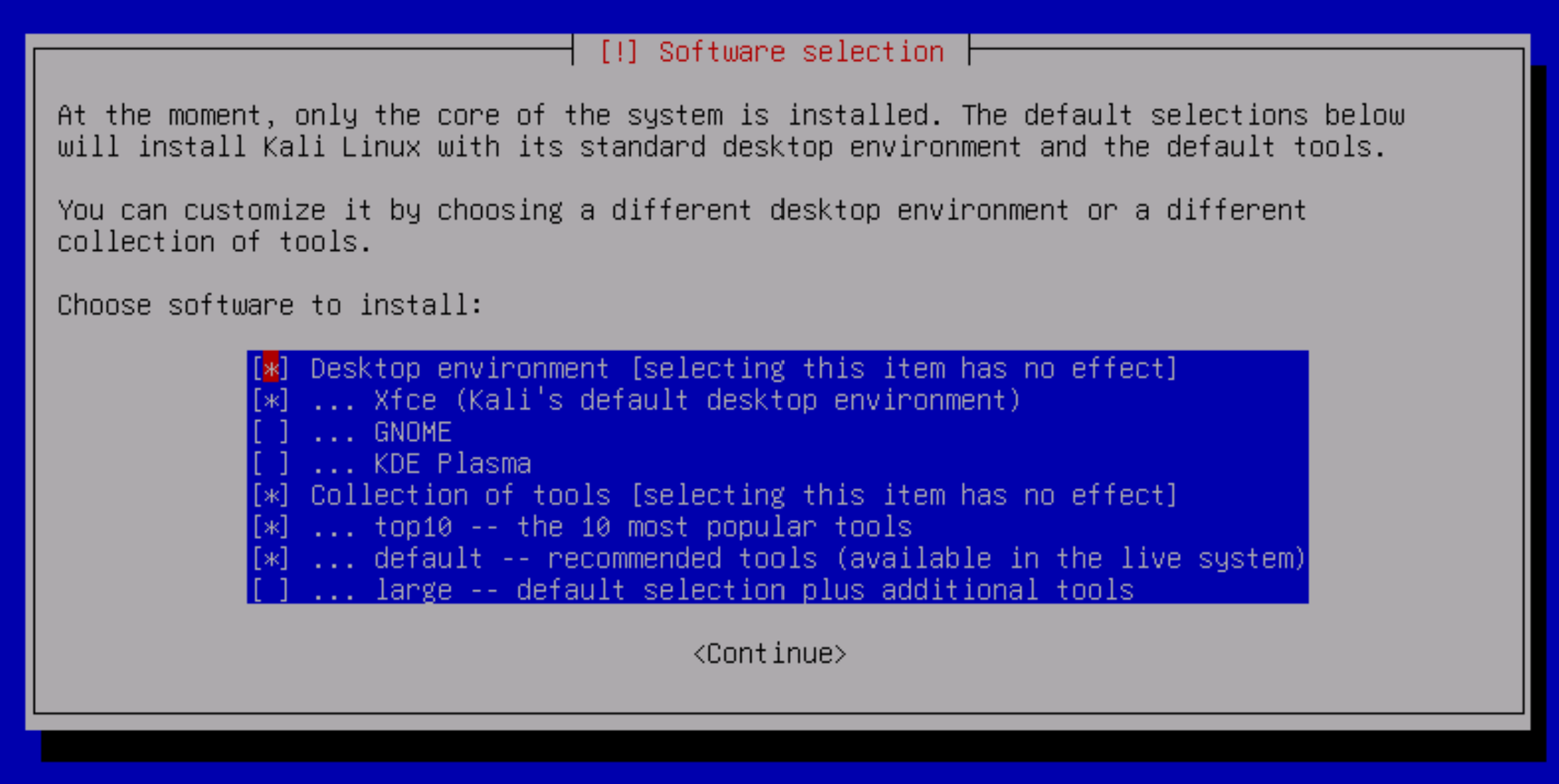
Choose a time zone, as well as the shell in which the user will work and a set of packages. There are 3 options to choose from: top 10 utilities, regular and advanced. The installation speed will depend on your internet speed.
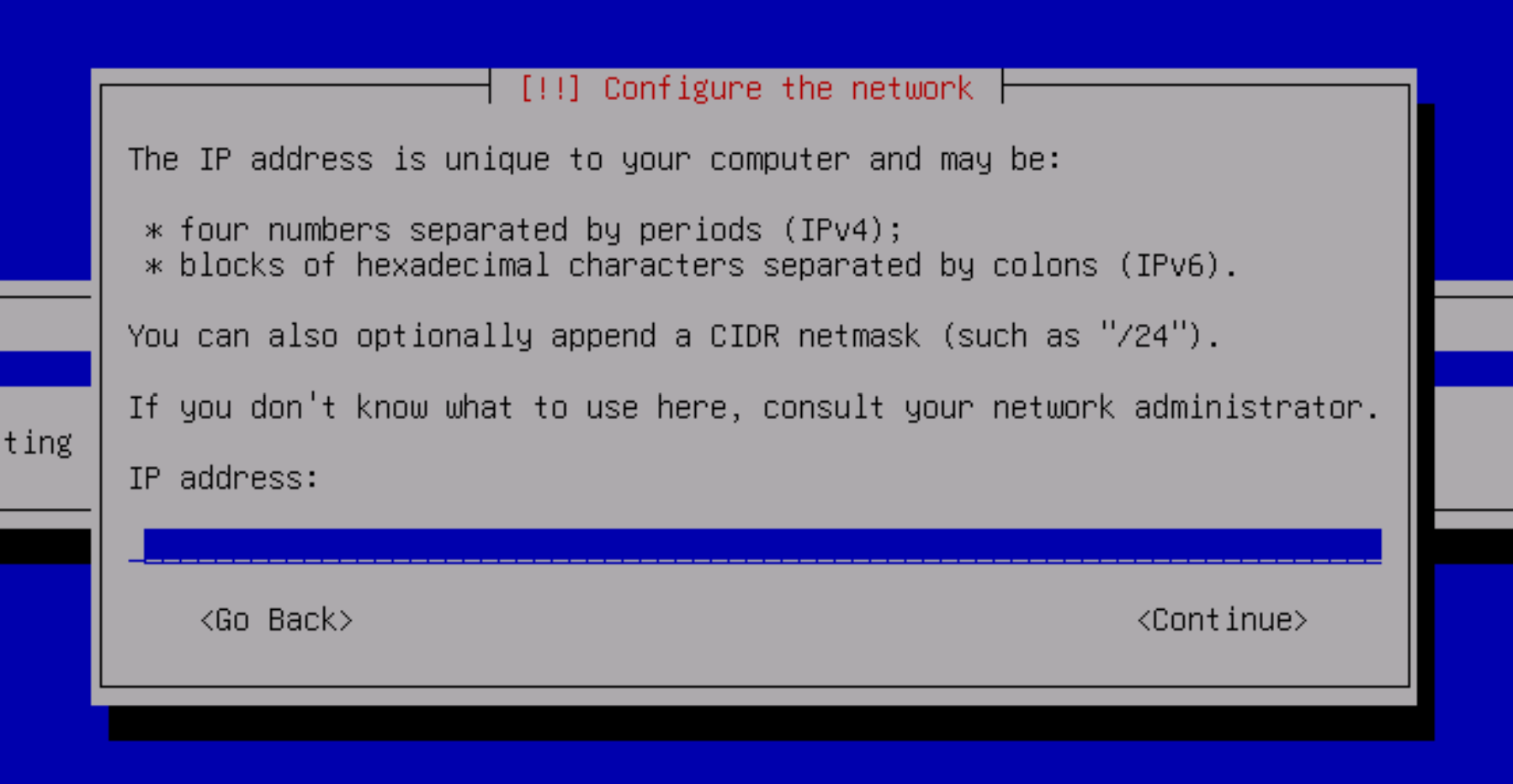
Before doing so, if you have not configured a network connection, by pressing the Esc key several times - go to the menu and select network configuration. There are two options, automatic via DHCP service and manual. For the first one, the configuration will take place without any additional requirements for the user, while the manual mode will ask for an IP address, mask and gateway.
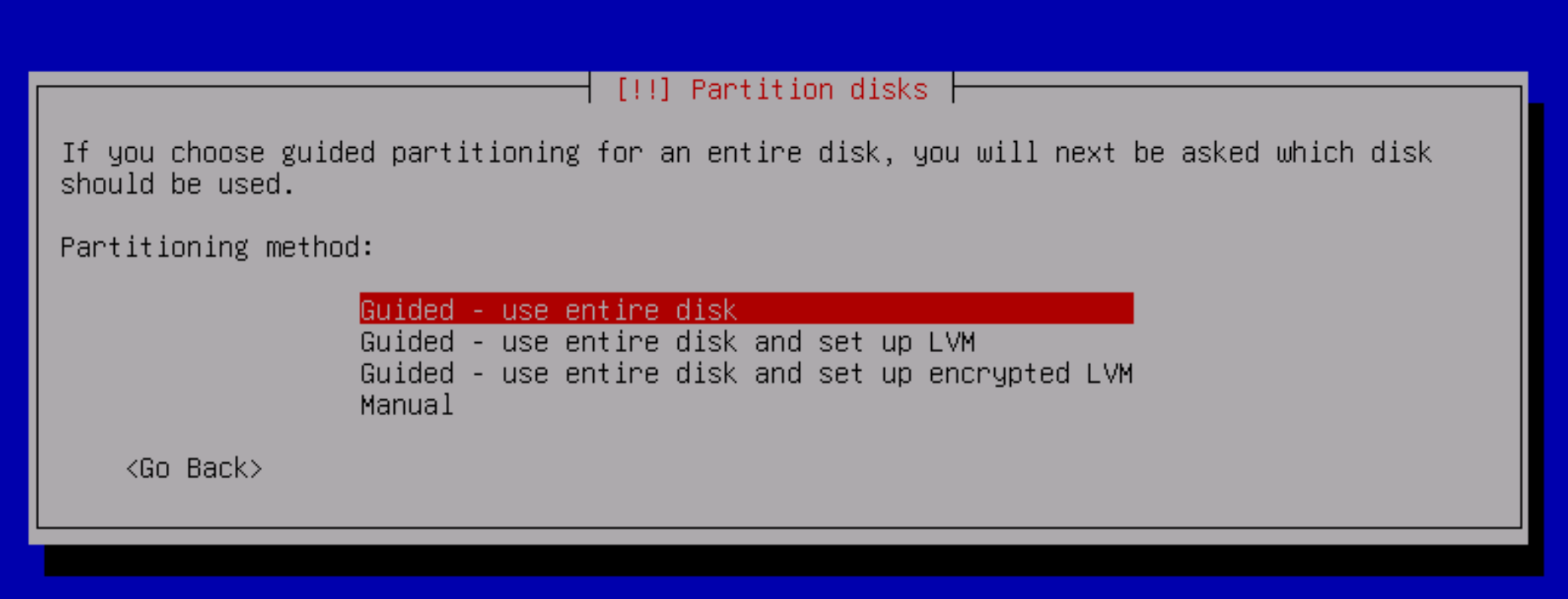
After that we can configure the disc space and choose how to configure it. By default, there are several schemes that allow you to deploy regular logical volumes, volumes + lvm, volumes + encrypted lvm.
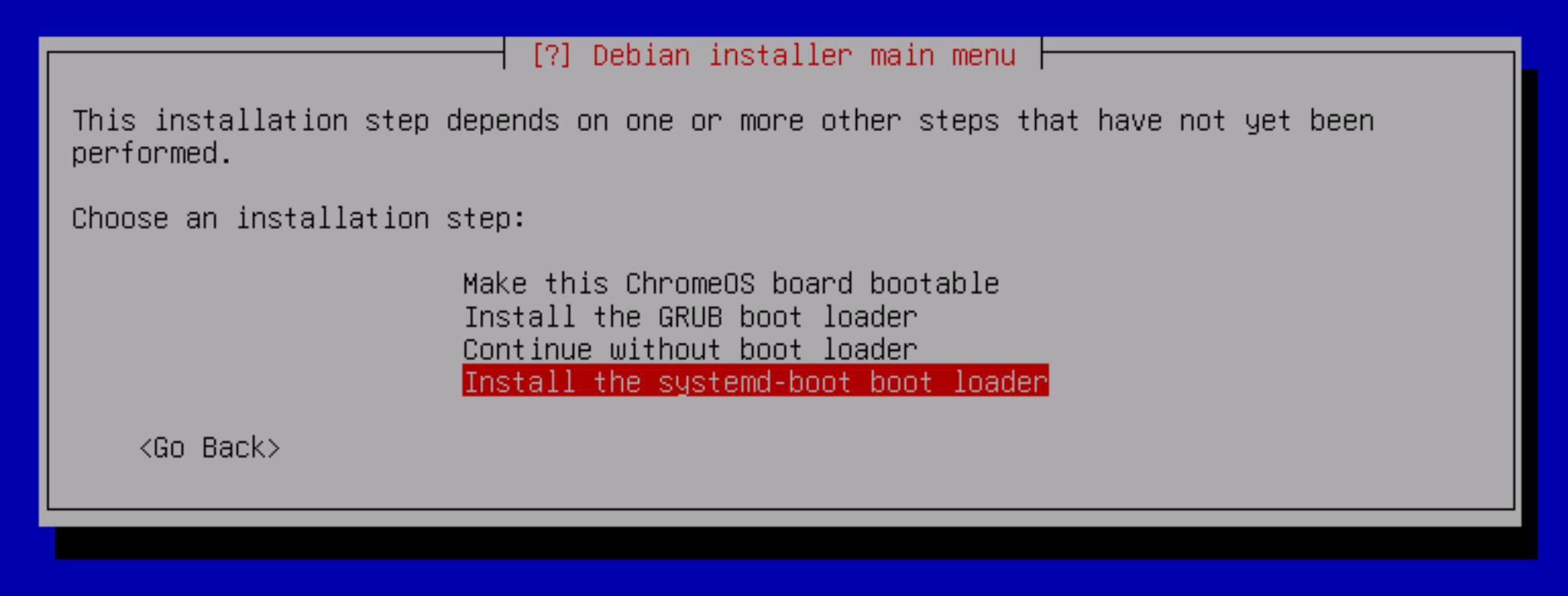
It is advisable to choose the second option with Lvm, as this solution will allow you to flexibly change the size of the disc and manage free space. The OS boot loader plays an important role, as it is the one that loads the operating system after BIOS startup. You can choose any boot loader you like, however, the stable Grub is recommended.
Let's wait until all the necessary dependencies are fully installed.
 Screenshot №9 — Software installation
Screenshot №9 — Software installation
After that the machine will reboot and the shell will be launched. We recorded the account data earlier, after entering them the OS is available for use.




