Then the encryption algorithm or Ciphers starts its work, which already allows to confidentially exchange information between servers, having previously announced a common session key. The symmetric algorithm is predominantly used, as the channel is already protected and it is possible to use a more efficient solution.
In our case, ssh-keygen allows you to create keys for the first step - authentication. In that article we consider keygen for windows 10 and another versions of OS include Linux!
How do I create SSH keys?
The scheme for Linux and Windows is typical, but differs only in the directories used. After going to the terminal you need to call the ssh-keygen utility, if you do not specify parameters, the keys will be created with default parameters.
ssh-keygen && ls –la ~/.ssh/ 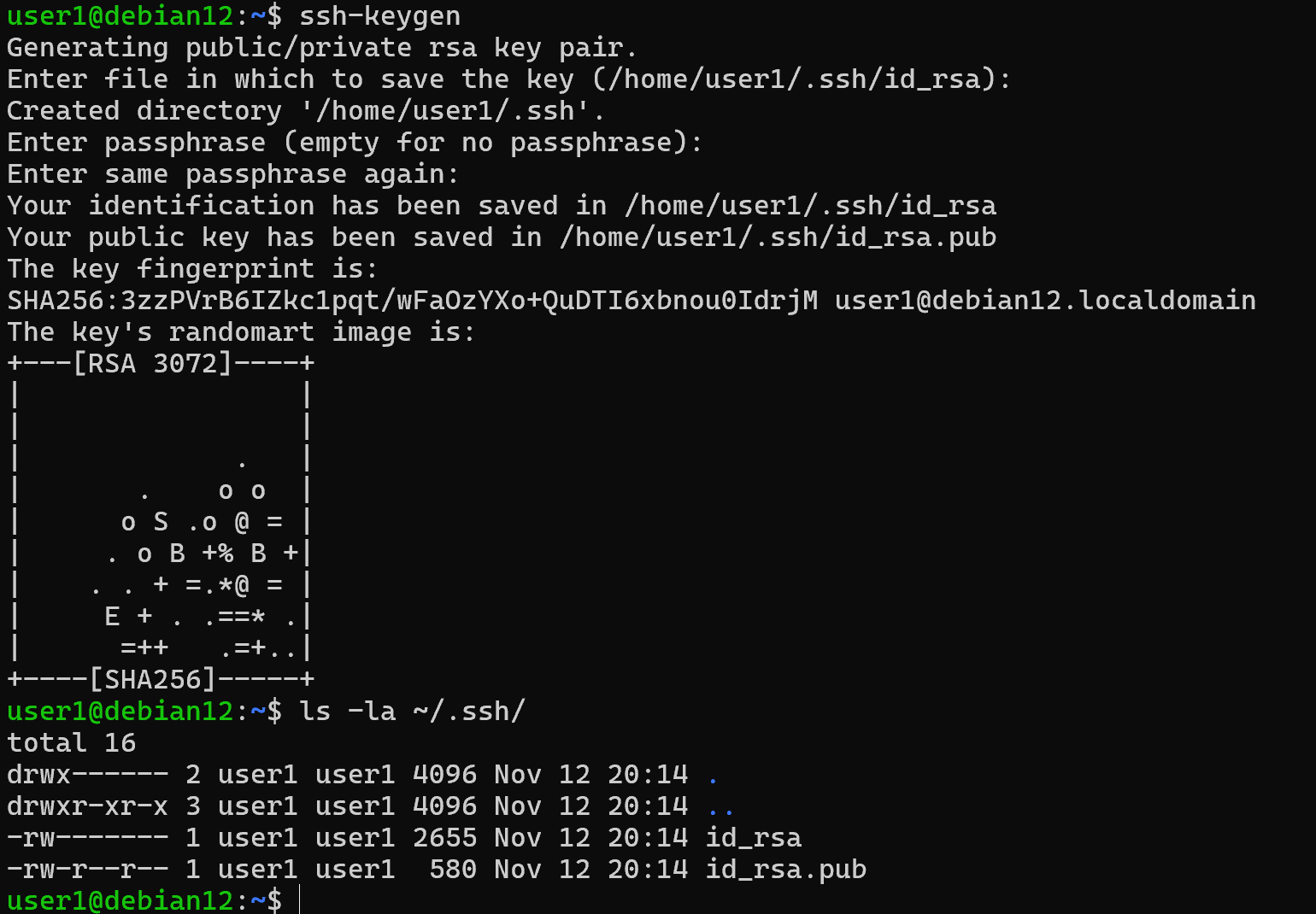
For an ssh server, this would be the /etc/ssh directory:
ssh-keygen -f /etc/ssh/ssh_host_rsa_key The authentication algorithm will be RSA, the key length is 3076, the comment is username@host of your machine. It is preferable to specify a master password when creating the key, it will keep the private key encrypted. However, if you want to access the target server via an intermediate server with your key, then do not forget to allow redirection of ssh agent in the configuration of servers. We can also use alternative algorithms, specify the -t parameter and the name of the desired one when creating it:
ssh-keygen –t Ed25519 –b 256 –a 24 –C “user1@host.com”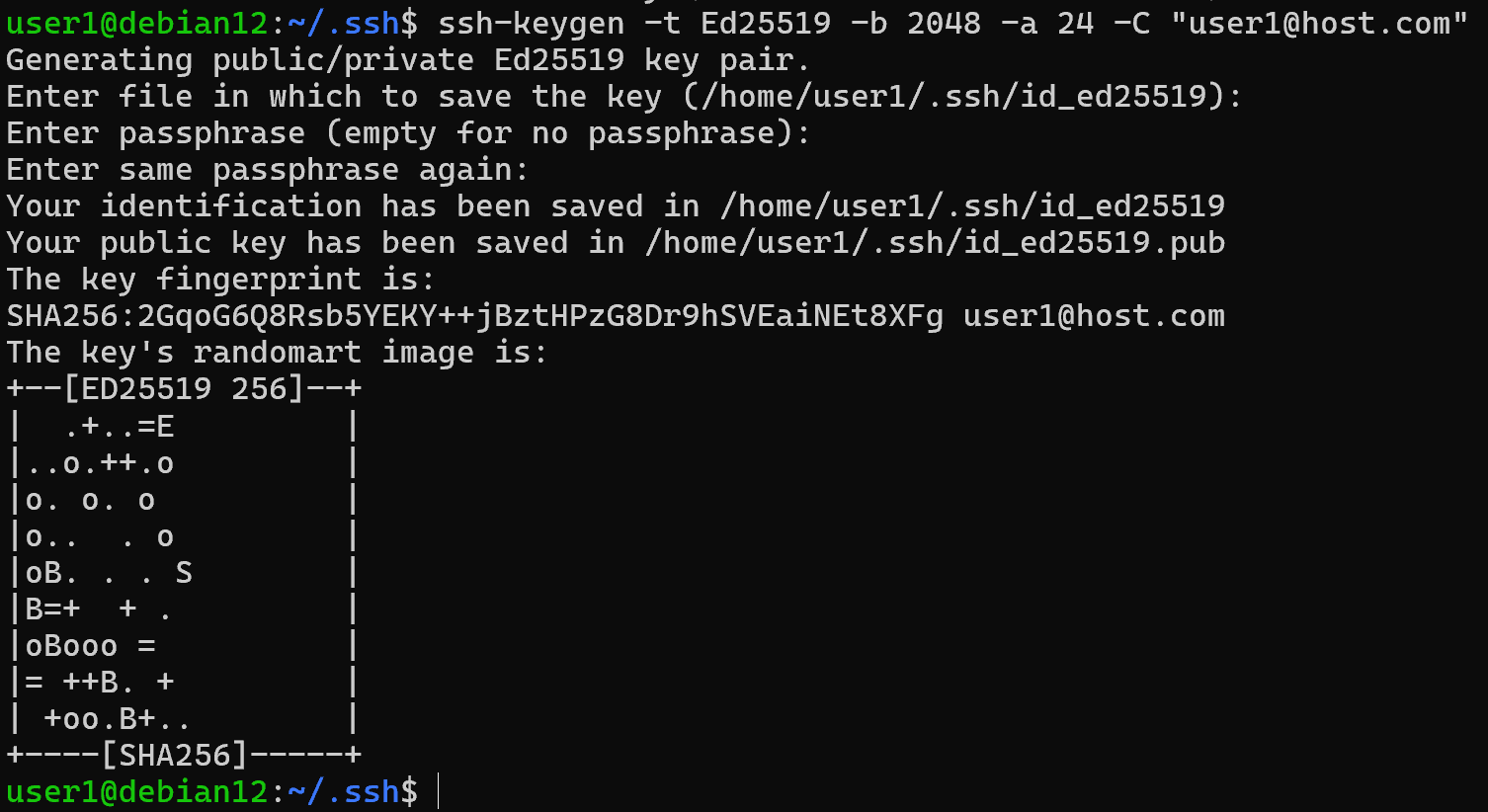
Optionally, you can also specify the key length -b, the number of encryption rounds -a, and a comment with -C. Note that the case is case sensitive in this case. The more you choose the key length and encryption rounds, the more time it will take to enumerate it, but also the more resources. It is recommended to choose classical values from 3072 bits in RSA, from 256 bits for Ed25519.
To view the created key hashes, specify the -l option and the key path:
ssh-keygen –l [path-to-key] 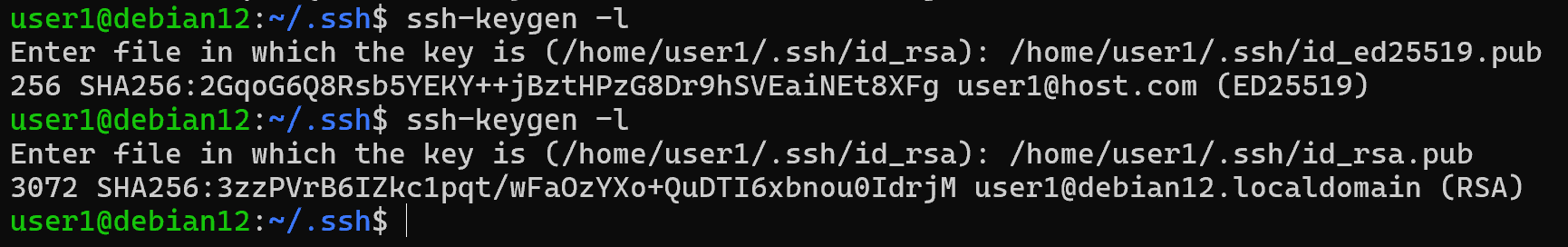
This function is useful when it is necessary to check the fingerprint values when connecting to the server for the first time to avoid MitM. This is important because this is the only stage where spoofing is possible when connecting.
To export public keys, you can use the command:
ssh-keygen –e [path-to-key] 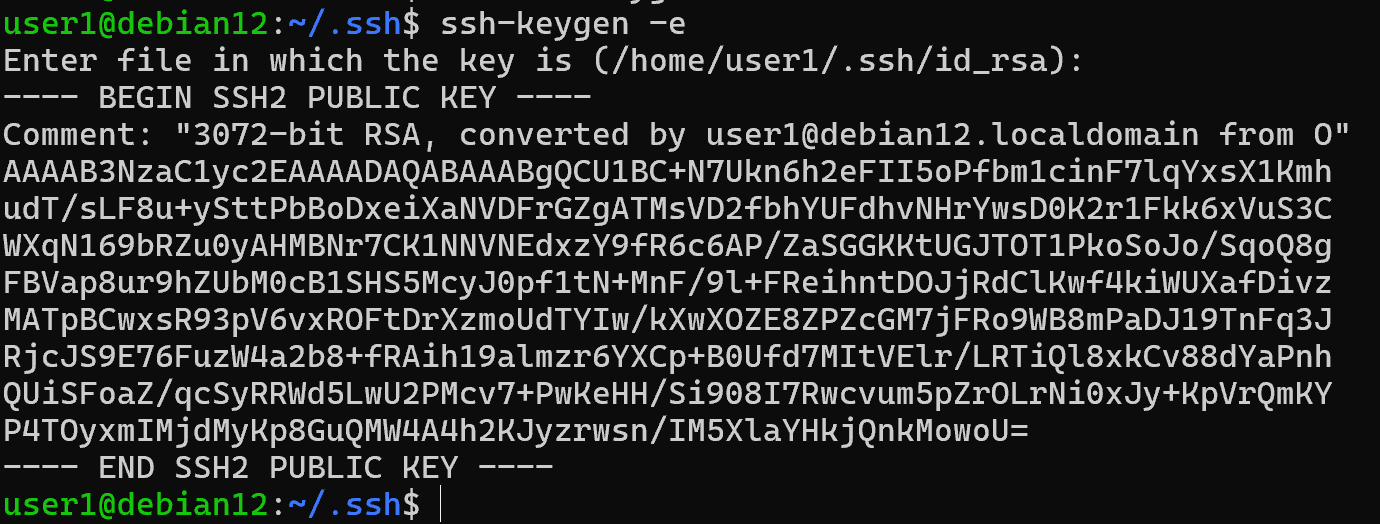
This data can be used to authenticate to third-party servers by adding it to the authorised _keys folder.
How do I change the master password on SSH keys?
If you have forgotten your master key, unfortunately there are no measures to recover it. Therefore, you will have to create a new one and distribute it. To change an existing one, specify the -p, -N option with the new password and the path to the file:
ssh-keygen –p –N 123321 –f ~/.ssh/id_rsa 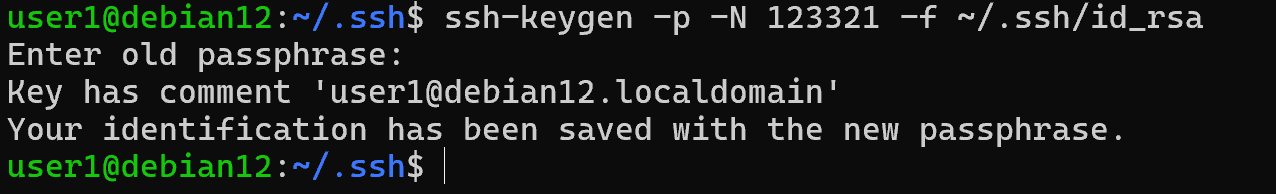
How do I quietly create an SSH key without displaying the output?
This method may be required when you need to create the required keys using a script without output:
ssh-keygen –q –N 123321 –f /home/user1/.ssh/ 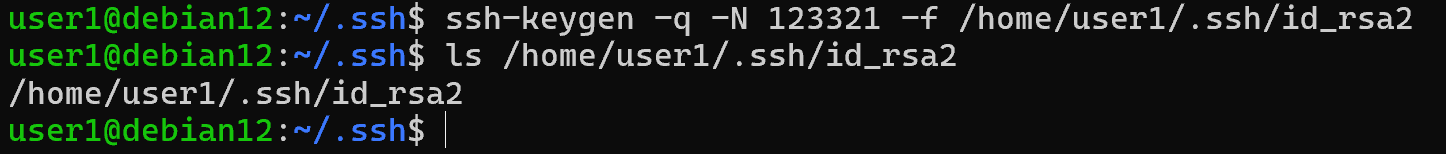
As a result, they will lie in the user's folder and be used by the SSH client/agent when authenticating.
How to remove SSH server key fingerprints?
This can help when the server decided to change keys and we haven't updated our know_host entries. SSH client will simply deny the connection and we will not be able to access the machine, to reset the records write the command:
ssh-keygen –R 127.0.0.1 If a specific port has been specified for the connection, it must also be marked:
ssh-keygen –R [127.0.0.1]:2222 Such a combination will delete the required records, after which it is necessary to reconnect and verify the key fingerprints. This utility allows you to effectively manage keys, records of authorised servers and organise service operation. In that article we consider openssh pack of utility, that you can download for Linux:
apt install openssh-server And for Windows you can use Terminal with command:
winget install Microsoft.OpenSSH.Preview If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

Conclusion
SSH keygen is an essential tool for securely managing authentication between clients and servers. By generating SSH keys, you establish a robust method for verifying identities and preventing unauthorized access. Understanding how to create, export, and manage keys—whether on Linux or Windows—ensures your connections remain secure. Additionally, features like changing passphrases, quiet key creation, and removing old server fingerprints help maintain smooth and safe SSH operations. Mastering ssh-keygen is a fundamental skill for system administrators and anyone working with secure remote access.
FAQ
- Q1: What is the purpose of ssh-keygen?
A: ssh-keygen is used to generate SSH keys for secure authentication, manage existing keys, and handle fingerprints of servers to prevent unauthorized access. - Q2: How do I create a new SSH key?
A: Use the command:ssh-keygen -t RSA -b 3072 -C "user@host"You can also specify different algorithms, key lengths, and comments as needed.
- Q3: How can I view the fingerprint of an SSH key?
A: Use the -l option:ssh-keygen -l -f [path-to-key] - Q4: How do I change the passphrase of an existing key?
A: Use:ssh-keygen -p -N new_passphrase -f [path-to-key]This will update the master password for the private key.
- Q5: Can I create SSH keys silently without output?
A: Yes, with the -q option:ssh-keygen -q -N "passphrase" -f /home/user/.ssh/id_rsa - Q6: How do I remove old server fingerprints from known_hosts?
A: Use the -R option:ssh-keygen -R 127.0.0.1For non-standard ports:
ssh-keygen -R [127.0.0.1]:2222 - Q7: Which software packages are needed for SSH key management?
A: On Linux, install OpenSSH:apt install openssh-serverOn Windows, use:
winget install Microsoft.OpenSSH.Preview - Q8: Can SSH keys be used across multiple servers?
A: Yes, export the public key using ssh-keygen -e and add it to the authorized_keys file on target servers for authentication. - Q9: What if I forget my SSH key passphrase?
A: Unfortunately, the original passphrase cannot be recovered. You must generate a new key and distribute it to the servers. - Q10: Is ssh-keygen secure for modern authentication needs?
A: Yes, it uses strong asymmetric encryption and supports multiple algorithms, making it reliable for secure remote server access.



