Recently, some users have experienced difficulties accessing content from video hosting and online services due to network traffic inspection mechanisms based on Deep Packet Inspection (DPI). In certain cases, DPI systems detect specific traffic patterns and restrict connections, which can lead to slow performance or complete loss of access.
In this article, we take a technical look at DPI, explain how anti-DPI approaches work, and review practical methods for restoring connectivity on Windows and Linux systems.
What is DPI and anti-DPI?
DPI or Deep Packet Inspection is software that records all network traffic from an interface, converts it into a structured file format and analyses the contents. Based on patterns, it blocks traffic, and anti-DPI approaches attempt to modify traffic characteristics in order to reduce false positives and avoid unintended blocking.
If you have found that your connection has become much slower or access to a necessary service has disappeared altogether, you should try installing SpoofDPI. This is a similar solution to GoodbyeDPI, but it uses different algorithms. Consider installing both Windows and Linux solutions.
If DPI is not working - solution on Windows
If you don't have sufficient resources than you can perform actions on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

Firstly let's check if the device has the necessary software to run the dpi solution, press Win+X and select terminal or Powershell. After that enter the command:
winget 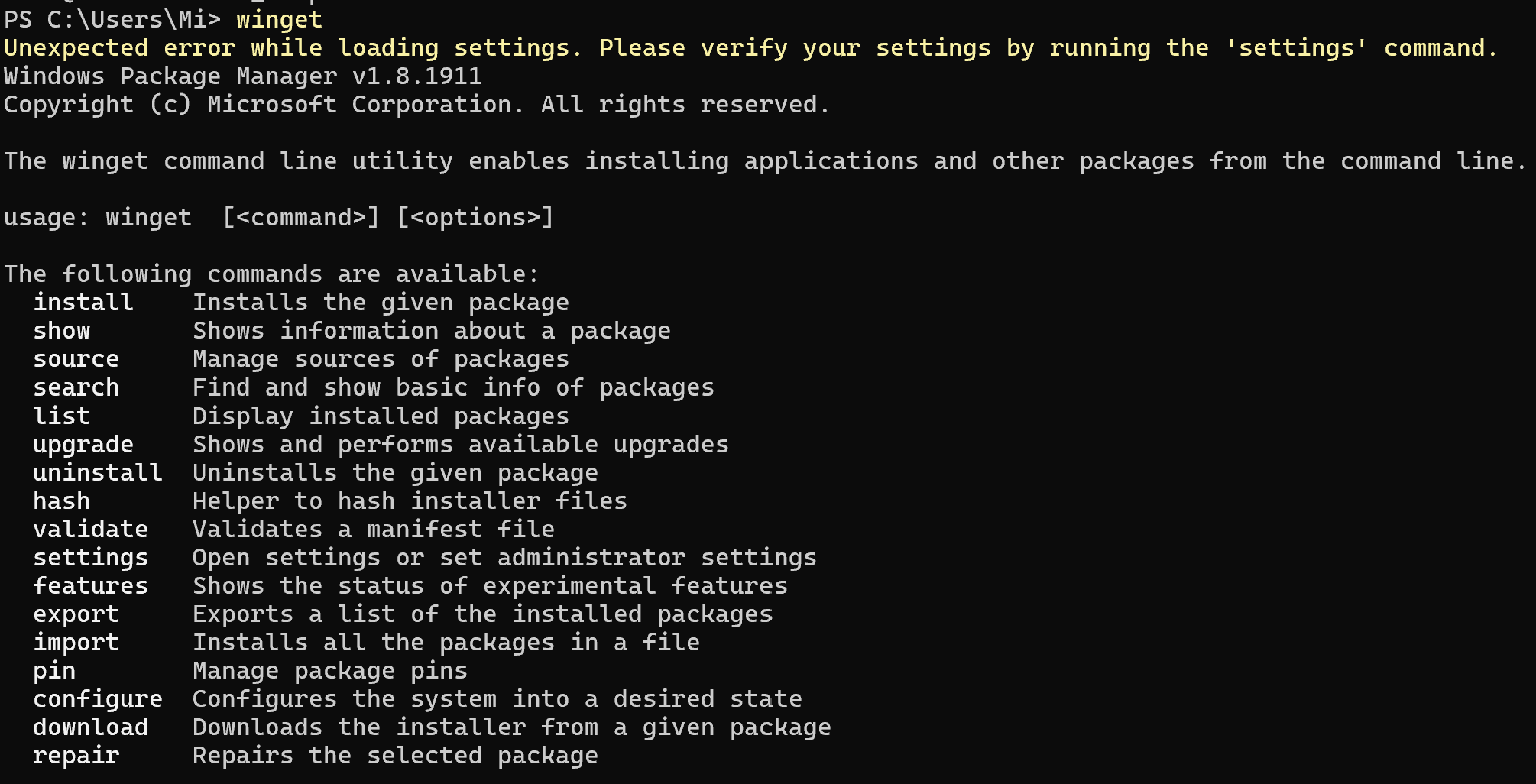
If the terminal outputs such help for the utility, then great - you have it installed and ready to work. But if not, you can install it from the official MS Store source and continue with the steps below. Let's download the package with Golang language for DPI instruction compilations:
winget install Golang.Go 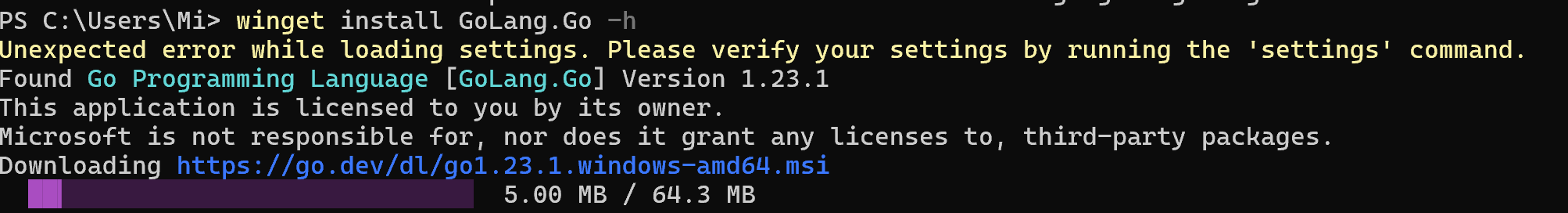
Afterwards, close the terminal and open it via the already known Win + X combination. This solution will update the paths to the software and provide access to the files. Let's run the command to install the DPI itself from the Github repositories:
go install github.com/xvzc/SpoofDPI/cmd/spoofdpi@latest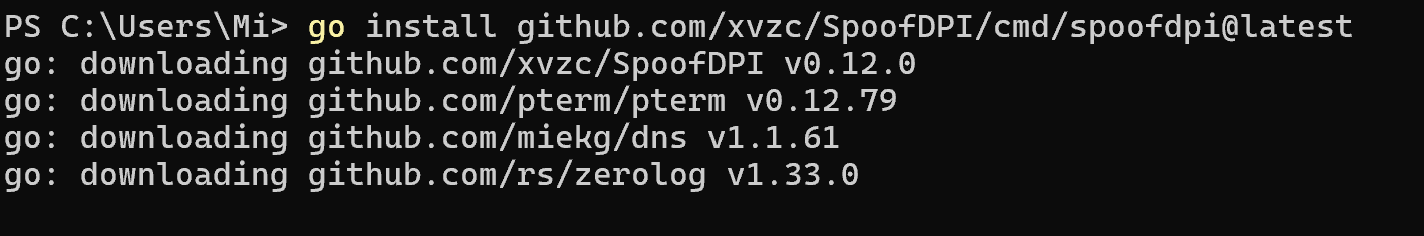
This command will download all the sources, load the necessary dependencies, and compile the files. If everything was successful, then repeat the manipulation with a restart of the terminal and enter:
spoofdpi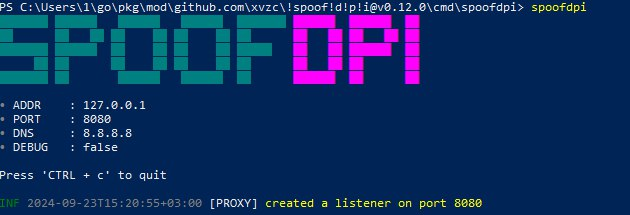
The DPI service has been raised on the device, where you now need to direct traffic by proxying for the browser in the settings or use the system ones. To do this, press the keyboard shortcut Win + I and go to ‘Network and Internet’ and then ‘Proxy’, and then fill in the data as indicated in the screenshot:
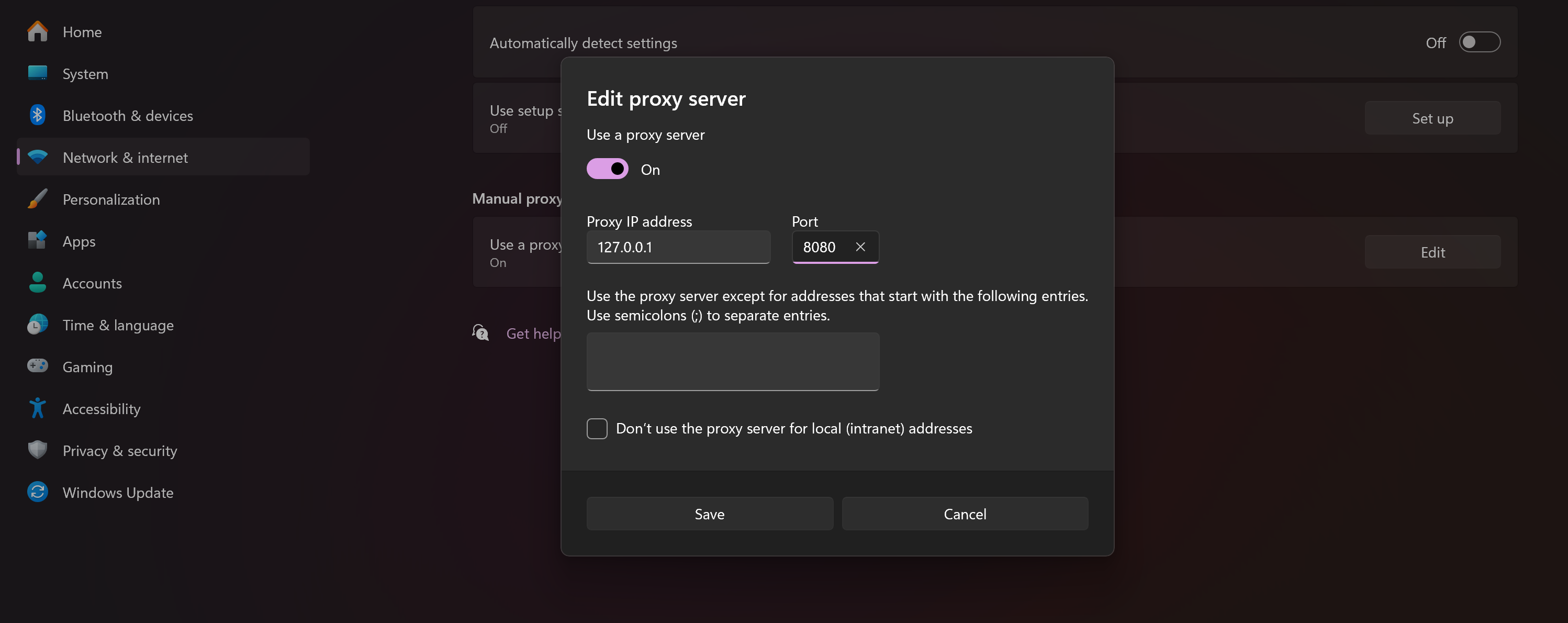
After that, the service loads in a matter of milliseconds and allows you to access resources. But please note that the detection rules are updated and this solution is up to date at the time of publication.
If DPI doesn't work - Linux solution
The scheme is approximately the same, you need to install the compiler, and then download the necessary dependencies. To install it, go to the official Golang site, where you can already choose the necessary version for your OS and processor architecture:
apt autoremove && wget https://go.dev/dl/go1.22.7.linux-amd64.tar.gzUnpack the downloaded archive, using the command:
tar -xf go1.22.7.linux-amd64.tar.gzImmediately specify new environment variables for working with the language, instead of the template path specify the one where the binary is located. Usually this is the directory where you unzipped the archive:
export PATH=$PATH:~/go/binAnd finally install the software by writing the command:
go install github.com/xvzc/SpoofDPI/cmd/spoofdpi@latest 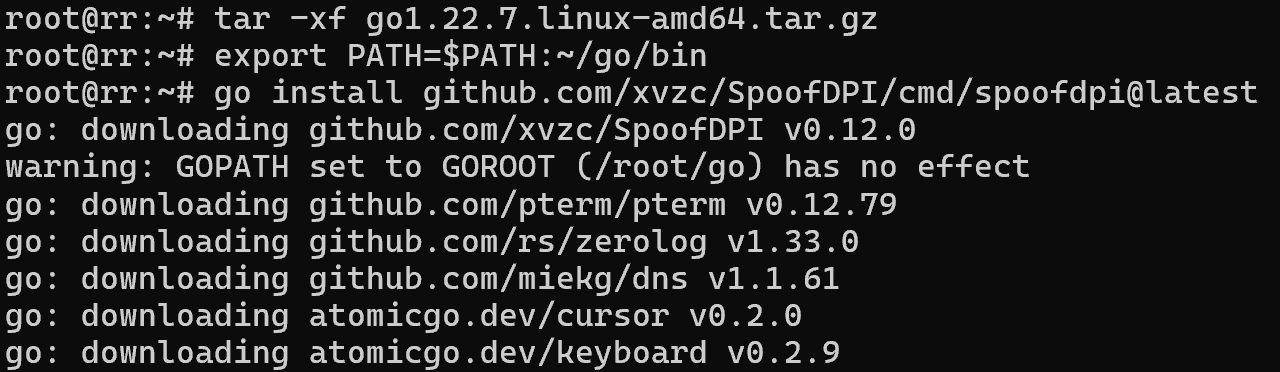
After that we can access anti-DPI via the command and raise the corresponding proxying service, which will modify the traffic coming to the network point:
spoofdpi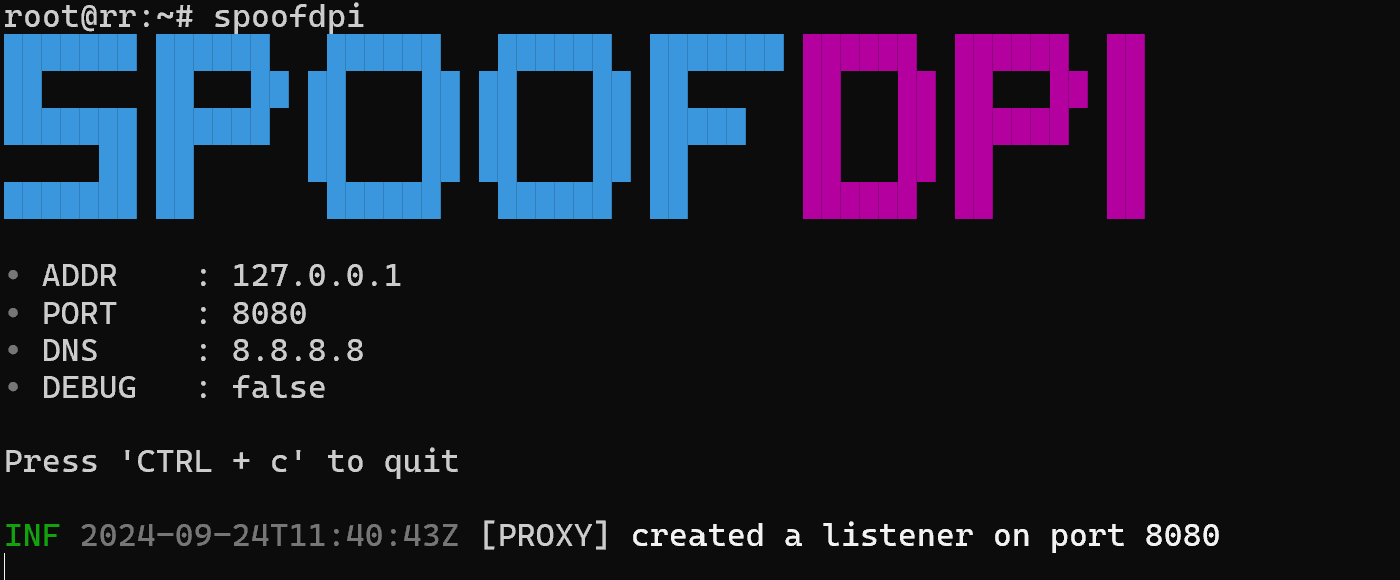
And now you can also specify separately for each application or system proxy redirection to this service. After that access to services will not be restricted.
Conclusion
Deep Packet Inspection (DPI) is widely used to analyze and filter network traffic, which can sometimes result in unintended access restrictions. While traditional tools may not always remain effective as detection rules evolve, alternative technical approaches can help diagnose and mitigate connectivity issues on Windows and Linux systems. Because DPI mechanisms change over time, ongoing updates and careful configuration are required to maintain stable network access.
FAQ
- 1. What is DPI (Deep Packet Inspection)?
DPI is a traffic filtering technology that inspects network packets in real time, identifies patterns, and blocks access to specific websites or services. - 2. What is the difference between DPI and anti-DPI?
DPI blocks traffic based on predefined patterns, while anti-DPI tools like GoodbyeDPI or SpoofDPI modify traffic to bypass detection. - 3. Why doesn’t GoodbyeDPI always work?
Because network providers constantly update detection patterns, older bypass tools may fail. SpoofDPI uses different algorithms that can help in cases where GoodbyeDPI is ineffective. - 4. Can I use SpoofDPI on both Windows and Linux?
Yes. SpoofDPI works cross-platform, though installation steps differ slightly between Windows and Linux (using Winget vs. manual Golang setup). - 5. Is it legal to use anti-DPI tools?
Legality depends on your country’s laws and the services you are trying to access. Always ensure you comply with local regulations before using such tools. - 6. Do I need Golang to install SpoofDPI?
Yes, since SpoofDPI is built in Go, you need the Go compiler installed to download, build, and run it from source. - 7. How do I redirect traffic through SpoofDPI?
After running spoofdpi, configure your system or browser proxy settings to direct traffic through the service. - 8. Will SpoofDPI always guarantee access to blocked sites?
Not necessarily. As DPI detection evolves, bypass methods may stop working. You may need to update the tool or try alternative anti-DPI solutions.



