The Linux family of distributions are mainly multitasking and multi-user operating systems, which inherently implies a requirement for differentiation of user rights. For this purpose, there are a number of utilities in the OS, which, in accordance with the POSIX standard, allow you to delimit rights using a discretionary access model. One of them is chmod, let's consider the principle of the access model and the utility's role in it.
What is chmod and the Linux discretionary model?
Chmod is a standard OC Linux utility that sets access rights for files and folders, allowing you to define the order in which different users can access a resource. As mentioned earlier, many Linux distributions are based on a discretionary access differentiation model. This means that each file and directory has its own list of attributes: owner, group and a list of permissions for three categories of OS users. Let's take an example, let's create a "secret directory" and files to it by commands:
mkdir -p /tmp/Secret-folder
touch /tmp/Secret-folder/gg
touch /tmp/Secret-folder/gtAnd let's immediately look at the standard attributes that the OS will give you:
ls -la /tmp/Secret-folder 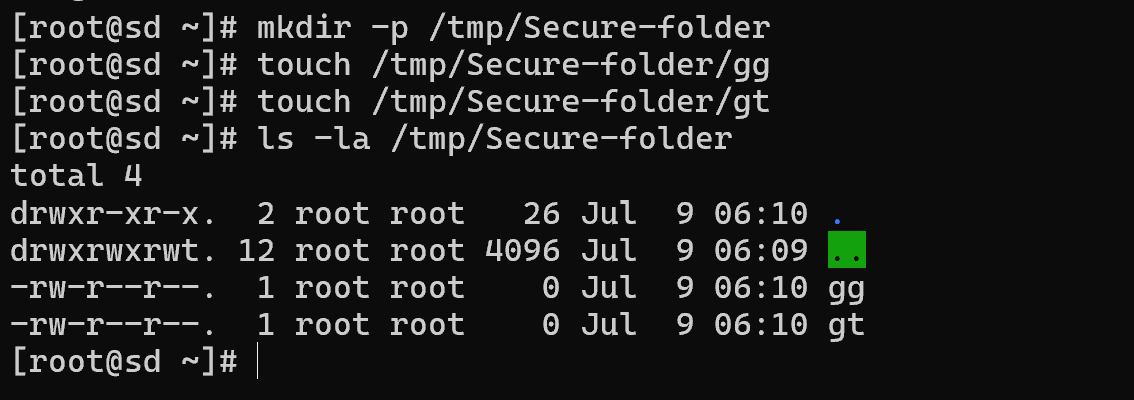
To the left of the displayed files and directories, you can see the set of their attributes, where the example of the gg file is:
- -rw-r--r-- access rights to the file;
- root root entry indicates the owner and group;
- jul 9 06:10 displays the time the file was last opened/modified.
Since we are the owners of the file, we can easily control the state of the access attributes, let's take a closer look at them. Each element on the left side has strings defining access rights to the file:
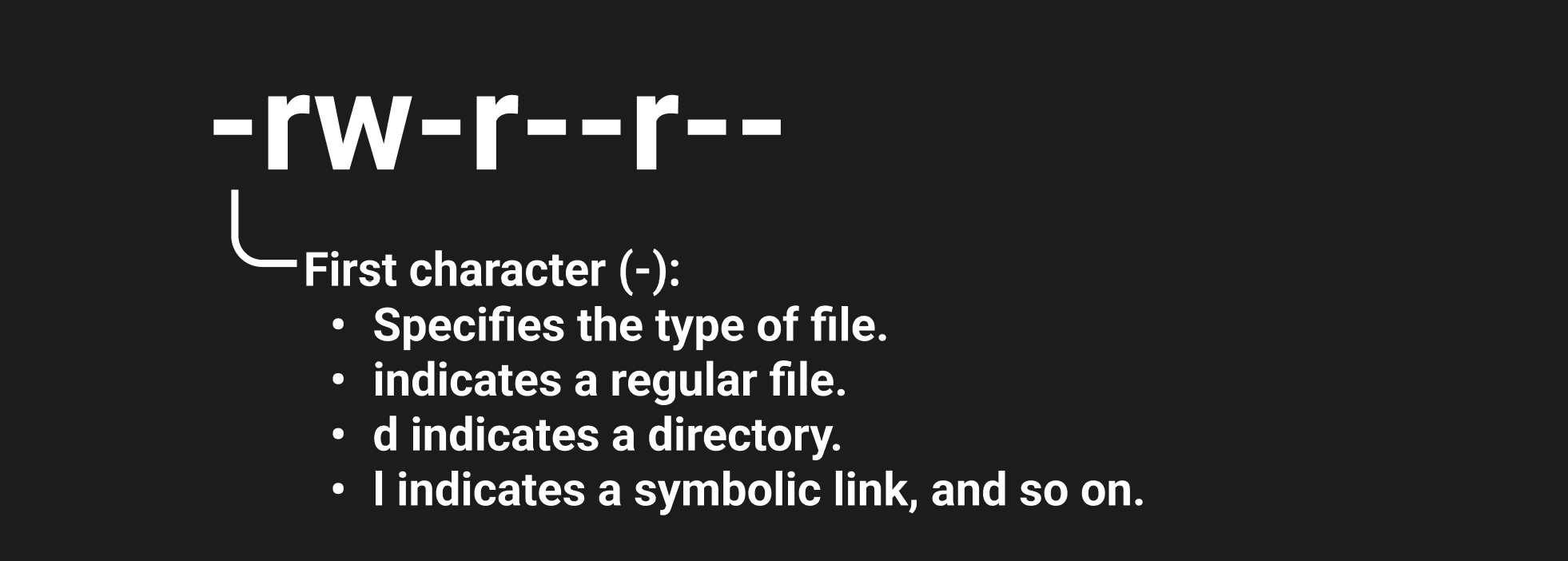
This bit may also contain SUID and GUID values that allow to run the file on behalf of its owner/group of owners, rather than those provided by the user. This solution allows you to temporarily grant rights, however, it is strongly not recommended for use! Since there is no privilege differentiation system, it is better to use sudo for this purpose.
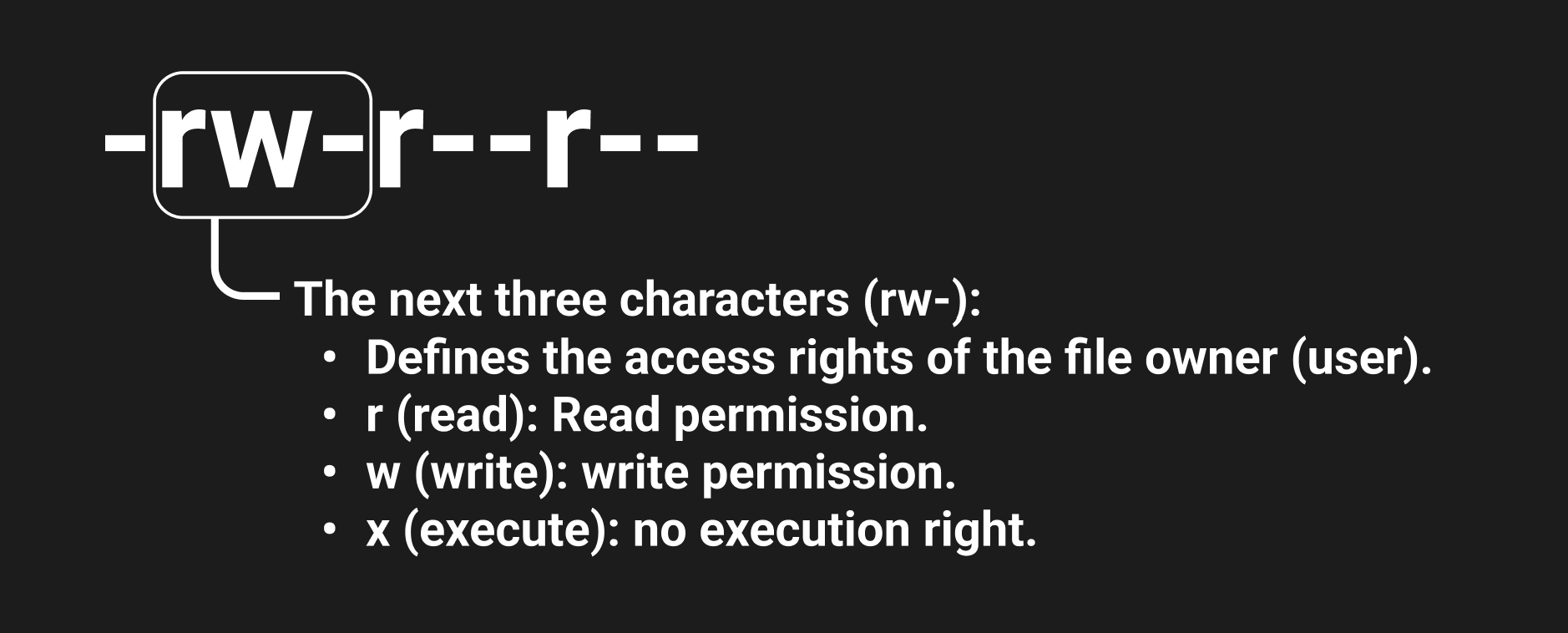
Then there are the file owner rights, which allow read and write access to the file, however, the owner or root can always change their level of access to the file or/and directory.

An owner's group brings together users who are in the same group as the owner. Usually, they either have the same rights as the owner or slightly reduced rights.

The other users are those that are not included in the list of the owner and his group. As a result, the string of access attributes is divided into 3 triplets and one bit: the rights of the owner, group, other users and the control bit. We will come back to the last one, let's consider their work on a practical example.
How to use chmod?
Similar to the previously created folder at the beginning, let's implement the following directory and the files in it:
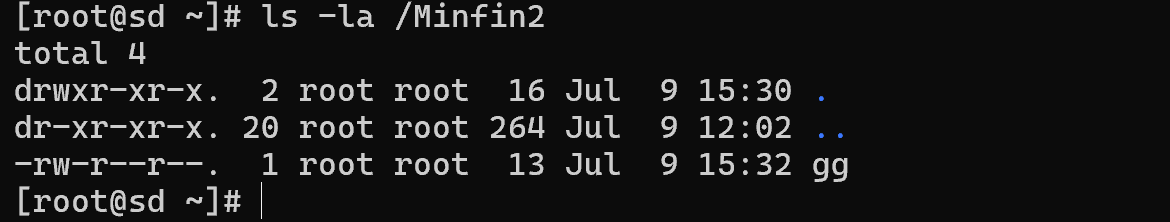
You may have noticed objects with a name in the form of a dot or two, and to the left of them the type of directory. The point is that when we go to the folder itself, we may need to briefly refer to it or the directory above it, and that's what these links are for. One point links to the current directory, two points link to the directory above.
For example, let's allow users in the owner group to write to a file, they currently have read-only permissions:
chmod 664 /Minfin2/gg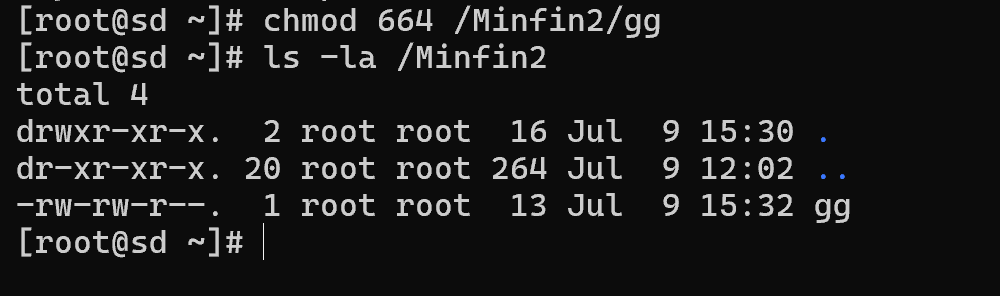
What do the numbers 664 mean? It was decided that each right in the triplet would have a numerical designation:
- 4 is read or reading;
- 2 is write, or writing, deleting, creating objects;
- 1 is execute or execute, scripts, binary files.
Each digit is the sum of the rights for one triplet group, the first 6 is rw for the owner, the second 6 for the group and the last 4 read for the rest. So 664 is equivalent to rw-rw-r-- the attributes of the file. Let's try from another user in the owner group to delete the file gg, the w access parameter on the file allows us to do this. But we catch the error permission denied:
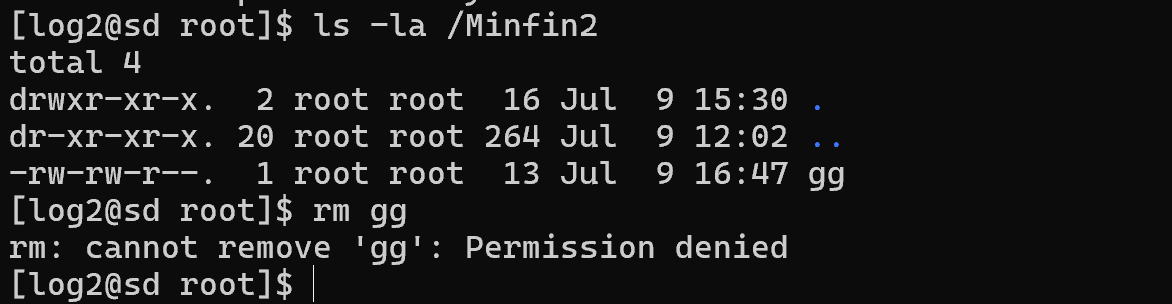
Why? Because there are permissions on the file, the point is that Linux has a hierarchical access rights check. This means that on the path to the file itself, the user must have permissions in directories too, except for the files themselves. Let's try to assign them and then delete the file:
chmod 775 /Minfin2 && rm /Minfin2/gg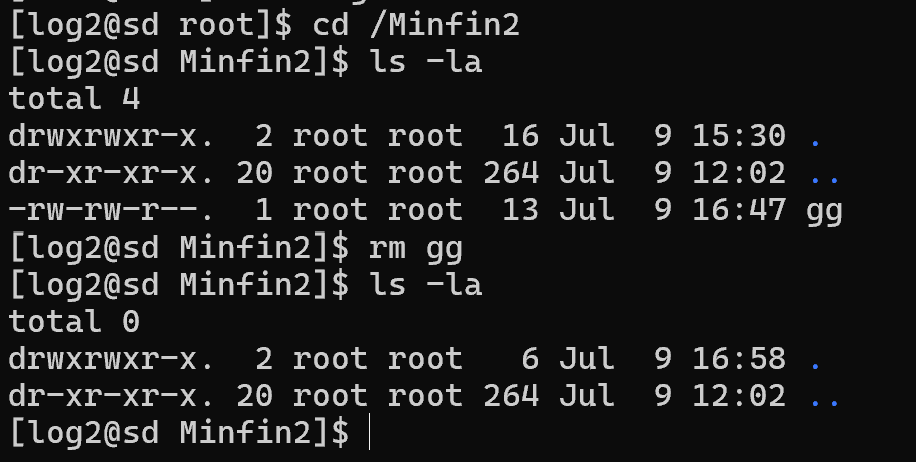
And success! The file was deleted, thanks to the fact that permissions were correctly granted to the file itself and the directory in which it was stored. If numbers are not a suitable form of control, we can use symbols. For example, give the owner the full set, the group and others the triplet r-x:
chmod ugo-rwx /Minfin2/gg && chmod u+rwx /Minfin2/gg && chmod /Minfin2/gg go+rx As you can see this solution is much longer than the numerical rights designation, however, it is just as functional and fulfils the tasks. All steps in the tutorial can be performed on powerful cloud servers. Serverspace provides isolated VPS / VDS servers for common and virtualize usage.

It will take some time to deploy server capacity. After that you can connect in any of the convenient ways.



